![[2016-NEW!] 200-120 New Questions and Answers -](http://s1.studyres.com/store/data/000108812_1-bba6a7d69201d6f7aa4d0f7684ac7604-300x300.png)
[2016-NEW!] 200-120 New Questions and Answers -
... The access link needs to be configured in multiple VLANs. The link between the switches is configured in the wrong VLAN. The link between the switches needs to be configured as a trunk. VTP is not configured to carry VLAN information between the switches. Switch IP addresses must be configured in or ...
... The access link needs to be configured in multiple VLANs. The link between the switches is configured in the wrong VLAN. The link between the switches needs to be configured as a trunk. VTP is not configured to carry VLAN information between the switches. Switch IP addresses must be configured in or ...
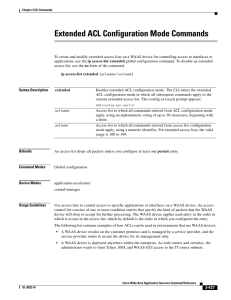
Extended ACL Configuration Mode Commands
... a 0 indicates a position that must be matched and a 1 indicates a position that does not matter. For instance, the wildcard 0.0.0.255 causes the last eight bits in the source IP address to be ignored. Therefore, the permit 192.168.1.0 0.0.0.255 entry allows access from any host on the 192.168.1.0 ne ...
... a 0 indicates a position that must be matched and a 1 indicates a position that does not matter. For instance, the wildcard 0.0.0.255 causes the last eight bits in the source IP address to be ignored. Therefore, the permit 192.168.1.0 0.0.0.255 entry allows access from any host on the 192.168.1.0 ne ...
IM7200-L Cellular Addendum
... This service periodically pings a nominated IP address. Each ping attempt sends out a configurable number of pings, and the ping attempt fails if none of these pings are successful. With the default settings, the keep alive ping attempts are sent at the 30 second intervals. Each ping attempt sends a ...
... This service periodically pings a nominated IP address. Each ping attempt sends out a configurable number of pings, and the ping attempt fails if none of these pings are successful. With the default settings, the keep alive ping attempts are sent at the 30 second intervals. Each ping attempt sends a ...
authors(v7) - IDA.LiU.se
... “cell”) in infrastructure mode contains: • wireless hosts • access point (AP): base station • ad hoc mode: hosts only ...
... “cell”) in infrastructure mode contains: • wireless hosts • access point (AP): base station • ad hoc mode: hosts only ...
Brief overview of our MURI proposal
... Thrust 1: Novel Algorithms • Local, Distributed graph Algorithms (Chung-Graham, Jadbabaie) – Graph algorithms for partitioning ...
... Thrust 1: Novel Algorithms • Local, Distributed graph Algorithms (Chung-Graham, Jadbabaie) – Graph algorithms for partitioning ...
8_19Counter Hack 6 scanning
... Ports like doors on each of machines Port scan knock on each door to see if anyone is listening behind it Someone behind the door, get a response No one behind the door, no answer back ...
... Ports like doors on each of machines Port scan knock on each door to see if anyone is listening behind it Someone behind the door, get a response No one behind the door, no answer back ...
Document
... Other trunking protocols have been used but are obsolete, including Inter-Switch Link (ISL), IEEE 802.10 (originally a security protocol but a subset was introduced for trunking), and ATM LAN ...
... Other trunking protocols have been used but are obsolete, including Inter-Switch Link (ISL), IEEE 802.10 (originally a security protocol but a subset was introduced for trunking), and ATM LAN ...
Security for Internet QoS
... • Cookie authentication techniques – Digital signature: uses public key and one-way hashing to compute the packet digest; secure but inefficient – Sealing: digital signature minus encryption, making it a seal, plus some value appended as “key”, i.e., routers should have the key to check the authenti ...
... • Cookie authentication techniques – Digital signature: uses public key and one-way hashing to compute the packet digest; secure but inefficient – Sealing: digital signature minus encryption, making it a seal, plus some value appended as “key”, i.e., routers should have the key to check the authenti ...
Software and Support Systems
... A network operating system is the most important software component. Numerous network support programs are also required to support users on a LAN. Support devices such as hubs, switches, routers, servers, modems, power supplies, and more are also necessary. ...
... A network operating system is the most important software component. Numerous network support programs are also required to support users on a LAN. Support devices such as hubs, switches, routers, servers, modems, power supplies, and more are also necessary. ...
Different Hashing Algorithms
... Schema: Description of the database and its tables. Usually written using a DDL. Cardinality: Number of rows in a table. Degree: Number of colums in a table. Domain: The set of all allowable values an attribute can take. Entity Integrity & Referential Integrity: View: Virtual table defined from othe ...
... Schema: Description of the database and its tables. Usually written using a DDL. Cardinality: Number of rows in a table. Degree: Number of colums in a table. Domain: The set of all allowable values an attribute can take. Entity Integrity & Referential Integrity: View: Virtual table defined from othe ...
Lecture - 12
... » Support billions of hosts, even with inefficient address allocation » Reduce the size of the routing tables » Simplify the protocol, to allow routers to process packets faster » Provide better security (authentication and privacy) than current IP » Pay more attention to type of service, particular ...
... » Support billions of hosts, even with inefficient address allocation » Reduce the size of the routing tables » Simplify the protocol, to allow routers to process packets faster » Provide better security (authentication and privacy) than current IP » Pay more attention to type of service, particular ...
3rd Edition, Chapter 5
... frame contains A-to-B IP datagram A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address R creates frame containing A-to-B IP datagram sends to B ...
... frame contains A-to-B IP datagram A’s adapter sends frame R’s adapter receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s MAC address R creates frame containing A-to-B IP datagram sends to B ...
Part I: Introduction
... protocol with all other routers in AS also responsible for routing to destinations outside AS run inter-AS routing protocol with other gateway routers ...
... protocol with all other routers in AS also responsible for routing to destinations outside AS run inter-AS routing protocol with other gateway routers ...
Layer 3 IP Packet
... Belongs to a different network Is a host on a different IP network Have an IP address and subnet mask of a different network Cisco IOS will not allow two active interfaces on the same router to belong to the same network. Note: A single interface on a router can be used to connect to multi ...
... Belongs to a different network Is a host on a different IP network Have an IP address and subnet mask of a different network Cisco IOS will not allow two active interfaces on the same router to belong to the same network. Note: A single interface on a router can be used to connect to multi ...
Quality of Service (QoS) for Enterprise Networks
... congestion on an interface. Meaning, they determine the priority on how to send packets when there’s more data than can be sent at a particular time. Queuing algorithms are activated only when a device is experiencing congestion and are then deactivated when congestion clears. There’s a limit on the ...
... congestion on an interface. Meaning, they determine the priority on how to send packets when there’s more data than can be sent at a particular time. Queuing algorithms are activated only when a device is experiencing congestion and are then deactivated when congestion clears. There’s a limit on the ...
powerpoint lecture
... – Browser uses tags to display graphical content – Knowledge needed to use Web page design tools ...
... – Browser uses tags to display graphical content – Knowledge needed to use Web page design tools ...
CISSP summary
... brute force attack (try many different characters) aka exhaustive dictionary attack (try many different words) Social engineering (convince an individual to give access) Rainbow Tables (tables with passwords that are already in hash format password checker and password hacker both programs that can ...
... brute force attack (try many different characters) aka exhaustive dictionary attack (try many different words) Social engineering (convince an individual to give access) Rainbow Tables (tables with passwords that are already in hash format password checker and password hacker both programs that can ...
hilltop.bradley.edu
... – Browser uses tags to display graphical content – Knowledge needed to use Web page design tools ...
... – Browser uses tags to display graphical content – Knowledge needed to use Web page design tools ...
Network Simulator Tutorial
... real-system not available, is complex/costly or dangerous (eg: space simulations, flight simulations) quickly evaluate design alternatives (eg: different system configurations) evaluate complex functions for which closed form formulas or numerical techniques not available ...
... real-system not available, is complex/costly or dangerous (eg: space simulations, flight simulations) quickly evaluate design alternatives (eg: different system configurations) evaluate complex functions for which closed form formulas or numerical techniques not available ...
投影片 1 - NTUT
... based approach,” in Proc. Internet Society INET, Jul. 1998. 6. Sonia Fahmy and Minseok Kwon, “Characterizing Overlay Multicast Networks and Their Costs,” IEEE Transaction on Networking, Vol. 15, no. 2, April 2007 ...
... based approach,” in Proc. Internet Society INET, Jul. 1998. 6. Sonia Fahmy and Minseok Kwon, “Characterizing Overlay Multicast Networks and Their Costs,” IEEE Transaction on Networking, Vol. 15, no. 2, April 2007 ...
Modern Technologies
... The technology enables computers using the same or compatible P2P programs to form a network and share digital files directly with other computers on the network. ...
... The technology enables computers using the same or compatible P2P programs to form a network and share digital files directly with other computers on the network. ...
Covert Communication in VANETS using Internet Protocol Header Bit
... prevent them from illegal and direct access[1] by the invader. Steganography of data can be done in various ways: ...
... prevent them from illegal and direct access[1] by the invader. Steganography of data can be done in various ways: ...
3rdEdition_Chapter6
... access of data frames: avoid collisions of long data frames optional; not typically used sender first transmits small request-to-send (RTS) packets to AP using CSMA RTSs may still collide with each other (but they’re short) AP broadcasts clear-to-send CTS in response to RTS CTS heard by all nodes ...
... access of data frames: avoid collisions of long data frames optional; not typically used sender first transmits small request-to-send (RTS) packets to AP using CSMA RTSs may still collide with each other (but they’re short) AP broadcasts clear-to-send CTS in response to RTS CTS heard by all nodes ...