Thin Servers with Smart Pipes: Designing SoC Accelerators for
... Conclusion Identify several system bottlenecks for high-performance and low-power CPUs Propose the TSSP design: low-power embedded class core + Memcached ...
... Conclusion Identify several system bottlenecks for high-performance and low-power CPUs Propose the TSSP design: low-power embedded class core + Memcached ...
Pass4sure 920
... Exam Preparation. Our 920-803 Q&As contains the most updated Nortel 920-803 real tests. You can use our 920-803 Q&As on any PC with most versions of Acrobat Reader and prepare the exam easily. ...
... Exam Preparation. Our 920-803 Q&As contains the most updated Nortel 920-803 real tests. You can use our 920-803 Q&As on any PC with most versions of Acrobat Reader and prepare the exam easily. ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP
... The Routing Information Protocol (RIP) is one of the oldest distance-vector routing protocol and employs the hop count as a routing metric. The RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from the source to a destination. Maximum number of hops allowed ...
... The Routing Information Protocol (RIP) is one of the oldest distance-vector routing protocol and employs the hop count as a routing metric. The RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from the source to a destination. Maximum number of hops allowed ...
Virtualization Security Checklist
... disabled. (A virtual switch might not support topology discovery or dynamic trunking protocols, such as Cisco PVST+. That is because virtual switches might not have a need to detect connected network devices.) 1.c.5 Use Layer 2 security configurations: Layer 2 security policies provide enhanced netw ...
... disabled. (A virtual switch might not support topology discovery or dynamic trunking protocols, such as Cisco PVST+. That is because virtual switches might not have a need to detect connected network devices.) 1.c.5 Use Layer 2 security configurations: Layer 2 security policies provide enhanced netw ...
Network Discovery Protocol LLDP and LLDPMED
... devices. (See Figure 1.) Because devices continually broadcast and listen for LLDP messages, they can discover when a new device is added or one removed. In this way, they maintain an accurate picture of a dynamic network. ...
... devices. (See Figure 1.) Because devices continually broadcast and listen for LLDP messages, they can discover when a new device is added or one removed. In this way, they maintain an accurate picture of a dynamic network. ...
FTTH
... Better quality pictures. More bandwidth possible with lower investment. Improved reliability. ...
... Better quality pictures. More bandwidth possible with lower investment. Improved reliability. ...
- Mitra.ac.in
... Q.1] What is OSI Model? Explain all the Seven Layers of OSI Model? Q.2] What are the layers of the OSI model? Enlist them. Which layer is responsible for following i] For adding a header that includes routing information. ii] For media access control layer. iii] For combining messages or segments in ...
... Q.1] What is OSI Model? Explain all the Seven Layers of OSI Model? Q.2] What are the layers of the OSI model? Enlist them. Which layer is responsible for following i] For adding a header that includes routing information. ii] For media access control layer. iii] For combining messages or segments in ...
Linux+ Guide to Linux Certification
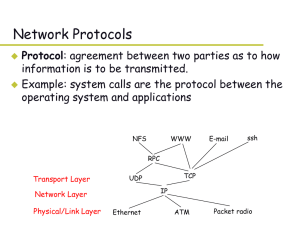
... • A network is a collection of connected computers that share information • A protocol is a set of rules that defines the format of information that is transmitted across a network • Each computer on a TCP/IP network must have a valid IPv4 or IPv6 address • The IPv4 configuration of a network interf ...
... • A network is a collection of connected computers that share information • A protocol is a set of rules that defines the format of information that is transmitted across a network • Each computer on a TCP/IP network must have a valid IPv4 or IPv6 address • The IPv4 configuration of a network interf ...
Servers
... • Servers exchange heartbeats with each other over the private net • Inform the receiving server the availability of the sending server ...
... • Servers exchange heartbeats with each other over the private net • Inform the receiving server the availability of the sending server ...
chap07.ppt
... detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 2nd edition ...
... detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 2nd edition ...
Blueprint For Security Chapter 6
... detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 2nd edition ...
... detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 2nd edition ...
Chapter2R - Radford University
... IP packet has (1,1) and (2,2) as IP source and destination addresses IP table at server indicates packet should be sent to router, so IP packet is encapsulated in Ethernet frame with addresses s and r Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type fie ...
... IP packet has (1,1) and (2,2) as IP source and destination addresses IP table at server indicates packet should be sent to router, so IP packet is encapsulated in Ethernet frame with addresses s and r Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type fie ...
bizhub 750/600 bizhub 751/601
... monochrome product line to fulfill their needs New Konica Minolta Alliance Program Plus (KMAP+) ► IPv6 as well as CAC card support (IC Card Authentication) Internet Protocol version 6 (IPv6) is designated as the successor of IPv4 bizhub 751/601 Series will provide full support for the new IPv6 ...
... monochrome product line to fulfill their needs New Konica Minolta Alliance Program Plus (KMAP+) ► IPv6 as well as CAC card support (IC Card Authentication) Internet Protocol version 6 (IPv6) is designated as the successor of IPv4 bizhub 751/601 Series will provide full support for the new IPv6 ...
Chapter 9: Network and Communication
... online, with other users connected to a server • Collaboration software includes tools that enable users to share documents via online meetings and communicate with other connected users ...
... online, with other users connected to a server • Collaboration software includes tools that enable users to share documents via online meetings and communicate with other connected users ...
SNMP Monitoring: One Critical Component to Network Management
... SNMP delivers management information in a common, non-proprietary manner, making it easy for an administrator to manage devices from different vendors using the same tools and interface. Its power is in the fact that it is a standard: one SNMP-compliant management station can communicate with agents ...
... SNMP delivers management information in a common, non-proprietary manner, making it easy for an administrator to manage devices from different vendors using the same tools and interface. Its power is in the fact that it is a standard: one SNMP-compliant management station can communicate with agents ...
Lecture 16
... • Type – 16-bit flag used to indicate which upper layer protocol gets the frame • Body – variable length area to put the data from LLC ...
... • Type – 16-bit flag used to indicate which upper layer protocol gets the frame • Body – variable length area to put the data from LLC ...
Carrier-Class Infrastructure
... • To provide insight from the platform supplier perspective • To share experiences we’ve seen and been a part of regarding this network scenario • To help guide developers out of the field and into the lab…There will be no sales if there is no product ...
... • To provide insight from the platform supplier perspective • To share experiences we’ve seen and been a part of regarding this network scenario • To help guide developers out of the field and into the lab…There will be no sales if there is no product ...
Chapter 9: Network and Communication
... online, with other users connected to a server • Collaboration software includes tools that enable users to share documents via online meetings and communicate with other connected users ...
... online, with other users connected to a server • Collaboration software includes tools that enable users to share documents via online meetings and communicate with other connected users ...
Part I: Introduction
... dynamically get address: “plug-and-play” host broadcasts “DHCP discover” msg DHCP server responds with “DHCP offer” msg host requests IP address: “DHCP request” msg DHCP server sends address: “DHCP ack” msg The common practice in LAN and home access ...
... dynamically get address: “plug-and-play” host broadcasts “DHCP discover” msg DHCP server responds with “DHCP offer” msg host requests IP address: “DHCP request” msg DHCP server sends address: “DHCP ack” msg The common practice in LAN and home access ...
Selling an Idea or a Product
... Epoch # – uniquely identifies which set of sequence numbers are being used. ...
... Epoch # – uniquely identifies which set of sequence numbers are being used. ...
M*N - UCL Computer Science
... Peers do not maintain the lists of entities in each cell, but they join and leave multicast groups as their entities move between cells ...
... Peers do not maintain the lists of entities in each cell, but they join and leave multicast groups as their entities move between cells ...