EVOLUTION OF COMPUTER NETWORKS
... computer networks. As a result of technological advances in the field of computer-components manufacturing, large-scale integrated circuits (LSI devices) appeared. LSI devices were characterized by relatively low cost and advanced functional capabilities. This led to the development of minicomputers ...
... computer networks. As a result of technological advances in the field of computer-components manufacturing, large-scale integrated circuits (LSI devices) appeared. LSI devices were characterized by relatively low cost and advanced functional capabilities. This led to the development of minicomputers ...
Chapter 9 - EECS People Web Server
... Managing Access Controls To appropriately manage access controls, an organization must have in place a formal access control policy, which determines how access rights are granted to entities and groups This policy must include provisions for periodically reviewing all access rights, granting a ...
... Managing Access Controls To appropriately manage access controls, an organization must have in place a formal access control policy, which determines how access rights are granted to entities and groups This policy must include provisions for periodically reviewing all access rights, granting a ...
Luminary Micro Customer Presentation
... based on the times of the local clocks. For example an actuator could be commanded to change its value at time T and a sensor to measure a value at time T+delta. Since the clocks are synchronized, the resulting actions are coordinated in time. ...
... based on the times of the local clocks. For example an actuator could be commanded to change its value at time T and a sensor to measure a value at time T+delta. Since the clocks are synchronized, the resulting actions are coordinated in time. ...
EMA: Successful Network Operations in a Cloud
... detect and report them. But organizations that use 11 or more network monitoring tools typically catch only 48% of network problems. Furthermore, IT organizations that fail to take an integrated approach to network management have very unstable networks. For instance, 34% of network teams that use 1 ...
... detect and report them. But organizations that use 11 or more network monitoring tools typically catch only 48% of network problems. Furthermore, IT organizations that fail to take an integrated approach to network management have very unstable networks. For instance, 34% of network teams that use 1 ...
Lab 7
... All of these scripts are intended as tools to help you with this lab. Although we have tested them heavily, we are not completely certain that they will function properly every time. We apologize for any problems you may encounter and welcome your input on changes. If you receive ANY messages such a ...
... All of these scripts are intended as tools to help you with this lab. Although we have tested them heavily, we are not completely certain that they will function properly every time. We apologize for any problems you may encounter and welcome your input on changes. If you receive ANY messages such a ...
Mobile Networking
... – Spontaneous or ad hoc networking • A group of users get together for a meeting and share information amongst their portable devices (phones, PDAs, laptops, MP3 players, …) • Some of the users have direct access to wireless networks provided by operators (and hence to Internet); some users do not – ...
... – Spontaneous or ad hoc networking • A group of users get together for a meeting and share information amongst their portable devices (phones, PDAs, laptops, MP3 players, …) • Some of the users have direct access to wireless networks provided by operators (and hence to Internet); some users do not – ...
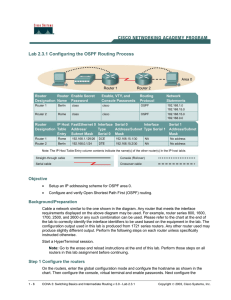
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
Evaluation of Network Topology Inference in Opaque
... for topology inference [12], [22]. The idea is that a source node sends probing packets to at least two receiver nodes. The receivers measure their individual packet loss rate. From correlations in the loss rates it is then possible to deduce common subpaths between the source and the receivers. Ide ...
... for topology inference [12], [22]. The idea is that a source node sends probing packets to at least two receiver nodes. The receivers measure their individual packet loss rate. From correlations in the loss rates it is then possible to deduce common subpaths between the source and the receivers. Ide ...
L h
... RIP (Routing information Protocol 路由信息协议 ) is a distance-vector protocol that allows routers to exchange information about destinations for computing routes throughout the network. OSPF (Open Shortest Path First 开放最短路径优先) is a dynamic routing protocol for use in Internet Protocol (IP) networks. ...
... RIP (Routing information Protocol 路由信息协议 ) is a distance-vector protocol that allows routers to exchange information about destinations for computing routes throughout the network. OSPF (Open Shortest Path First 开放最短路径优先) is a dynamic routing protocol for use in Internet Protocol (IP) networks. ...
RIVIERA TELEPHONE COMPANY, INC. Broadband
... customers experience a safe and secure broadband Internet environment that is fast, reliable and affordable. RTC wants its customers to indulge in all that the Internet has to offer, whether it is social networking, streaming videos and music, to communicating through email and videoconferencing ...
... customers experience a safe and secure broadband Internet environment that is fast, reliable and affordable. RTC wants its customers to indulge in all that the Internet has to offer, whether it is social networking, streaming videos and music, to communicating through email and videoconferencing ...
Impact of Sensor Networks on Future InterNetDesign
... Facing these challenges • Today, we use a wide range of ad hoc, application specific techniques in the SensorNet patch – Zillion different low-power MACs – Many link-specific, app-specific multihop routing protocols – Epidemic dissemination, directed diffusion, synopsis diffusion, … – All sorts of ...
... Facing these challenges • Today, we use a wide range of ad hoc, application specific techniques in the SensorNet patch – Zillion different low-power MACs – Many link-specific, app-specific multihop routing protocols – Epidemic dissemination, directed diffusion, synopsis diffusion, … – All sorts of ...
local area networks
... Another configuration of the bus topology is the master/slave bus topology, consisting of several slave controllers and one master network controller (see Figure 18-7). In this configuration, the master sends data to the slaves; if the master needs data from a slave, it will poll (address) the slave ...
... Another configuration of the bus topology is the master/slave bus topology, consisting of several slave controllers and one master network controller (see Figure 18-7). In this configuration, the master sends data to the slaves; if the master needs data from a slave, it will poll (address) the slave ...
Web Security Security+ Guide to Network Security Fundamentals
... – Have full access to Windows operating system ...
... – Have full access to Windows operating system ...
SEMESTER 1 Chapter 5
... It can perform unequal cost load balancing. It uses Diffusing Update Algorithm (DUAL) to calculate the shortest path. There are no periodic updates as with RIP and IGRP. Routing updates are sent only when there is a change in the topology. As vectors of distance and direction No ...
... It can perform unequal cost load balancing. It uses Diffusing Update Algorithm (DUAL) to calculate the shortest path. There are no periodic updates as with RIP and IGRP. Routing updates are sent only when there is a change in the topology. As vectors of distance and direction No ...
paper
... tolerance against the bit errors caused by noise and other fiber effects. [5] analytically evaluated BER performance of OFDM system that are intensity modulated in presence of baseband distortion at the transmitter and noise at the receiver. It showed that maintaining the system performance at a spe ...
... tolerance against the bit errors caused by noise and other fiber effects. [5] analytically evaluated BER performance of OFDM system that are intensity modulated in presence of baseband distortion at the transmitter and noise at the receiver. It showed that maintaining the system performance at a spe ...
The Internet: How It Works
... • Data is broken into small units called packets • Packets are sent over various routes to their destination • Packets are reassembled by the receiving computer • Packets contain – Destination/source addresses – Reassembling instructions – Data ...
... • Data is broken into small units called packets • Packets are sent over various routes to their destination • Packets are reassembled by the receiving computer • Packets contain – Destination/source addresses – Reassembling instructions – Data ...
Chapter 3
... Each bridge inspects the source address in all the frames it receives Record the information at the bridge and build the table When a bridge first boots, this table is empty Entries are added over time A timeout is associated with each entry The bridge discards the entry after a specified period of ...
... Each bridge inspects the source address in all the frames it receives Record the information at the bridge and build the table When a bridge first boots, this table is empty Entries are added over time A timeout is associated with each entry The bridge discards the entry after a specified period of ...
Efficiency through Eavesdropping: Link-layer Packet Caching
... reserved for the RTS-id/CTS exchange at this point. Upon reception of an RTS-id frame, the receiver checks its local packet cache for a packet whose ID matches that in the RTS frame. If present, the receiver sends a CTSACK and processes the frame as if it had been received normally. A CTS-ACK is sim ...
... reserved for the RTS-id/CTS exchange at this point. Upon reception of an RTS-id frame, the receiver checks its local packet cache for a packet whose ID matches that in the RTS frame. If present, the receiver sends a CTSACK and processes the frame as if it had been received normally. A CTS-ACK is sim ...
PPT_2
... (more) Addresses: 6 bytes if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
... (more) Addresses: 6 bytes if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
Future Internet with Information Centric Networks
... – Routing the request message to the responsible NRS node where the object name is translated into one or multiple source addresses – Routing the request message to the source address(es) – Routing the data from the source(s) to the requester. ...
... – Routing the request message to the responsible NRS node where the object name is translated into one or multiple source addresses – Routing the request message to the source address(es) – Routing the data from the source(s) to the requester. ...
Network Node of INDIV-5 AMR
... • Passing on all relevant consumption values to all network nodes on the network • Communication via the INDIV-5 AMR gateway ...
... • Passing on all relevant consumption values to all network nodes on the network • Communication via the INDIV-5 AMR gateway ...
Ch06
... • Generally only one per host • If more than one, then usually one of each type – Specify transport protocol (TCP, UDP) ...
... • Generally only one per host • If more than one, then usually one of each type – Specify transport protocol (TCP, UDP) ...