network programming - Mathematical, Statistical, and Scientific
... Unlike TCP, no connection is established prior to sending data. The sender just carries on after sending a message. TCP is connection oriented, UDP is connectionless. TCP is more reliable whereas UDP is more streamlined. Scientific Software (MCS 507) ...
... Unlike TCP, no connection is established prior to sending data. The sender just carries on after sending a message. TCP is connection oriented, UDP is connectionless. TCP is more reliable whereas UDP is more streamlined. Scientific Software (MCS 507) ...
Investigating Two Different Approaches for Encrypted Traffic
... application types is an important task of network management to detect security threats or throttle/block traffic from unwanted applications. Earlier detection provides better solutions to block or control the problem by the network/system administrators. Furthermore, accurate classification of netw ...
... application types is an important task of network management to detect security threats or throttle/block traffic from unwanted applications. Earlier detection provides better solutions to block or control the problem by the network/system administrators. Furthermore, accurate classification of netw ...
Europa: Efficient User Mode Packet Forwarding in Network Virtualization
... is an important factor differentiating our work from existing work in operating system area. As we will see later in the paper, avoiding the overhead of invoking system calls is important for an Europa virtual router to forward packets at high speed, because using system calls to interact between us ...
... is an important factor differentiating our work from existing work in operating system area. As we will see later in the paper, avoiding the overhead of invoking system calls is important for an Europa virtual router to forward packets at high speed, because using system calls to interact between us ...
Promising the future: 40G to 100G
... With infrastructure migration imperative, KPN began with transport network restructuring. In June 2005, KPN signed an exclusive contract with Huawei for CWDM and DWDM for the access layer and national trunks, respectively, laying a solid basis for broadband network operation which enabled the operat ...
... With infrastructure migration imperative, KPN began with transport network restructuring. In June 2005, KPN signed an exclusive contract with Huawei for CWDM and DWDM for the access layer and national trunks, respectively, laying a solid basis for broadband network operation which enabled the operat ...
NETWORKED ATTACHED DEVICES AT SNS
... LabVIEW EPICS Client I/O Server • Bases on EPICS base 3.14.8 • Runs on LabVIEW for Windows • Requires LabVIEW Datalogging & ...
... LabVIEW EPICS Client I/O Server • Bases on EPICS base 3.14.8 • Runs on LabVIEW for Windows • Requires LabVIEW Datalogging & ...
App Development for Smart Devices
... • The final two parameters in sendTextMessage let you specify Intents to track the transmission and delivery. • Implement and register corresponding Broadcast Receivers that listen for the actions you specify when creating the Pending Intents you pass in sendTextMessage. • Intent parameter, sentI ...
... • The final two parameters in sendTextMessage let you specify Intents to track the transmission and delivery. • Implement and register corresponding Broadcast Receivers that listen for the actions you specify when creating the Pending Intents you pass in sendTextMessage. • Intent parameter, sentI ...
routed - Current UG - The University of Sydney
... • Two basic algorithms used by routing update protocols – Distance-vector – Link-state ...
... • Two basic algorithms used by routing update protocols – Distance-vector – Link-state ...
On Networks N300 WiFi Router(N300R) User Manual
... configuration is correct. Your Internet service provider (ISP) should have provided you with all the information needed to connect to the Internet. If you cannot locate this information, ask your ISP to provide it. When your router Internet connection is set up, you no longer need to launch the ISP’ ...
... configuration is correct. Your Internet service provider (ISP) should have provided you with all the information needed to connect to the Internet. If you cannot locate this information, ask your ISP to provide it. When your router Internet connection is set up, you no longer need to launch the ISP’ ...
4020-Lecture3_4 - eee
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
Link Layer
... walkthrough: send datagram from A to B via R focus on addressing – at IP (datagram) and MAC layer (frame) assume A knows B’s IP address assume A knows IP address of first hop router, R (how?) assume A knows R’s MAC address (how?) ...
... walkthrough: send datagram from A to B via R focus on addressing – at IP (datagram) and MAC layer (frame) assume A knows B’s IP address assume A knows IP address of first hop router, R (how?) assume A knows R’s MAC address (how?) ...
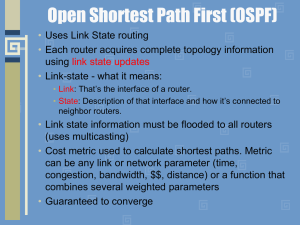
module10b
... • Router Priority: This value is used to determine who will become designated or backup designated router. • DR and BDR IP address: Designated and Backup Designated router for multiple access networks such as an Ethernet segment. • Authentication password: You can use clear text and MD5 authenticati ...
... • Router Priority: This value is used to determine who will become designated or backup designated router. • DR and BDR IP address: Designated and Backup Designated router for multiple access networks such as an Ethernet segment. • Authentication password: You can use clear text and MD5 authenticati ...
Discovery_Routing_Switching_Chapter2
... What portion of the IP address is used to route packets? ...
... What portion of the IP address is used to route packets? ...
Net Setting page - X-Core Technology Co., Ltd.
... streaming. The Stream2 will not show-up if Stream1 shared Full FrameRate (30fps). Please setup the Framerate for using or requests. Important! Click 3GPP button will send this stream (1 or 2) out for 3GPP signal. There’s also a 3GPP button at the down side of Stream2 settings for choice. Please setu ...
... streaming. The Stream2 will not show-up if Stream1 shared Full FrameRate (30fps). Please setup the Framerate for using or requests. Important! Click 3GPP button will send this stream (1 or 2) out for 3GPP signal. There’s also a 3GPP button at the down side of Stream2 settings for choice. Please setu ...
GET-IT!
... “In the early days of the Internet one could rely on a flat name space given by IP addresses; knowing the IP address of a computer would very likely allow now to talk to that computer in some way. This is no longer the case: firewalls partition the Internet into administrative domains that are isola ...
... “In the early days of the Internet one could rely on a flat name space given by IP addresses; knowing the IP address of a computer would very likely allow now to talk to that computer in some way. This is no longer the case: firewalls partition the Internet into administrative domains that are isola ...
Chapter5 - Philadelphia University Jordan
... authors of the textbook: Wireless and Mobile Networks, concepts and protocols. See slide number one. ...
... authors of the textbook: Wireless and Mobile Networks, concepts and protocols. See slide number one. ...
Slides - Asia Pacific Advanced Network
... information between equipment in addition to controller. ...
... information between equipment in addition to controller. ...
Week#8, Week#9, Week#10 - Philadelphia University
... authors of the textbook: Wireless and Mobile Networks, concepts and protocols. See slide number one. ...
... authors of the textbook: Wireless and Mobile Networks, concepts and protocols. See slide number one. ...
ZXHN H108N - Movistar.
... auto-negotiation capability for different standards (G.dmt, T1.413 Issue 2) according to the settings on the central office Digital Subscriber Line Access Multiplexer (DSLAM). It provides four 10/100Base-T Ethernet interfaces and one Universal Serial Bus (USB) 2.0 Host interface. It supports Institu ...
... auto-negotiation capability for different standards (G.dmt, T1.413 Issue 2) according to the settings on the central office Digital Subscriber Line Access Multiplexer (DSLAM). It provides four 10/100Base-T Ethernet interfaces and one Universal Serial Bus (USB) 2.0 Host interface. It supports Institu ...
Labeled Optical Burst Switching and IP/WDM Integration
... – many functions not necessary/meaningful for data traffic (e.g., bidirectional/symmetric links) – use predominantly rings: not BW efficient, but quick protection/restoration (<= 50 ms) ...
... – many functions not necessary/meaningful for data traffic (e.g., bidirectional/symmetric links) – use predominantly rings: not BW efficient, but quick protection/restoration (<= 50 ms) ...
Réunion EGEE France Activités « réseau
... to EGEE as part of the existing network infrastructure hierarchy have to be categorized as: – Compliant with the Premium IP service – Supportive of the Premium IP service – Indifferent to the Premium IP service ...
... to EGEE as part of the existing network infrastructure hierarchy have to be categorized as: – Compliant with the Premium IP service – Supportive of the Premium IP service – Indifferent to the Premium IP service ...
tcp - clear - Rice University
... • Each Side of Connection can Send and Receive • What this Means – Maintain different sequence numbers for each direction – A single packet can contain new data for one direction, plus acknowledgement for other • May also contain only data or only acknowledgement T. S. Eugene Ng ...
... • Each Side of Connection can Send and Receive • What this Means – Maintain different sequence numbers for each direction – A single packet can contain new data for one direction, plus acknowledgement for other • May also contain only data or only acknowledgement T. S. Eugene Ng ...
Build A World Class Monitoring System for
... which controls to implement, organizations should evaluate which categories are most relevant to company operations and have the lowest cost with the most impact. For example, if an organization sells products online, web security would likely be a top priority. Within the web security category, an ...
... which controls to implement, organizations should evaluate which categories are most relevant to company operations and have the lowest cost with the most impact. For example, if an organization sells products online, web security would likely be a top priority. Within the web security category, an ...