DLNA, AIRPLAY AND AIRPRINT ON CAMPUS NETWORKS solution guide
... DLNA and Bonjour rely on Layer 2 protocols that use multicast messages. In order to enable Bonjour and DLNA services on campus networks, IT departments must perform customization to enjoy the following capabilities: • Forward DLNA and Bonjour across subnets and VLANs, especially as devices like Appl ...
... DLNA and Bonjour rely on Layer 2 protocols that use multicast messages. In order to enable Bonjour and DLNA services on campus networks, IT departments must perform customization to enjoy the following capabilities: • Forward DLNA and Bonjour across subnets and VLANs, especially as devices like Appl ...
HZ3313741379
... and hence cannot cope efficiently with significant traffic dynamics. There are well known reasons for this limitation: IGP-based TE only allows for static traffic delivery through native IGP paths, without flexible traffic splitting for dynamic load balancing. In addition, changing IGP link weights ...
... and hence cannot cope efficiently with significant traffic dynamics. There are well known reasons for this limitation: IGP-based TE only allows for static traffic delivery through native IGP paths, without flexible traffic splitting for dynamic load balancing. In addition, changing IGP link weights ...
Hands-On Ethical Hacking and Network Security
... • Several different platforms and technologies can be used to develop Web applications • Attacks differ depending on the platform and technology used to develop the application – Footprinting is used to find out as much information as possible about a target system – The more you know about a system ...
... • Several different platforms and technologies can be used to develop Web applications • Attacks differ depending on the platform and technology used to develop the application – Footprinting is used to find out as much information as possible about a target system – The more you know about a system ...
Evaluating the Eifel Algorithm for TCP in a GPRS Network
... Apparently, Reno with Eifel suffers from lengthy nonspurious timeouts caused by packet losses. Figure 7 shows an example of the poor performance of Reno with Eifel when packet losses occur. The first timeout at second 30 is caused by a delay and is spurious. The Eifel algorithm successfully detects ...
... Apparently, Reno with Eifel suffers from lengthy nonspurious timeouts caused by packet losses. Figure 7 shows an example of the poor performance of Reno with Eifel when packet losses occur. The first timeout at second 30 is caused by a delay and is spurious. The Eifel algorithm successfully detects ...
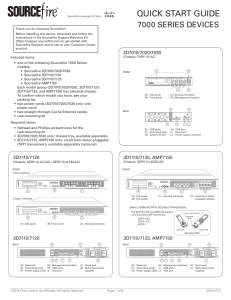
http://www.cisco.com/c/dam/en/us/td/docs/security/sourcefire/3d-system/53/quick-start-guides/QSG-3D7xxx-v53-3-20140311.pdf
... Deploying the Device Your device is typically deployed inside a firewall, where it is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management net ...
... Deploying the Device Your device is typically deployed inside a firewall, where it is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management net ...
load balancing
... • Each source node stores packets in separate transmission buffers according to their destination address • Packet selection at source node – If arriving photonic slot is assigned a destination » Head-of-line packet of buffer associated with destination is selected for transmission, provided not all ...
... • Each source node stores packets in separate transmission buffers according to their destination address • Packet selection at source node – If arriving photonic slot is assigned a destination » Head-of-line packet of buffer associated with destination is selected for transmission, provided not all ...
Applications and Digital Transmission Fundamentals
... Cookies and Web Sessions • Cookies are data exchanged by clients & servers as header lines • Since HTTP stateless, cookies can provide context for HTTP interaction • Set cookie header line in reply message from server includes unique ID number for client • If client accepts cookie, cookie added to ...
... Cookies and Web Sessions • Cookies are data exchanged by clients & servers as header lines • Since HTTP stateless, cookies can provide context for HTTP interaction • Set cookie header line in reply message from server includes unique ID number for client • If client accepts cookie, cookie added to ...
Cray XC Series Network
... locality in the underlying physical process being simulated. Applications with regular data decomposition (e.g., a 2-D mesh) can be executed efficiently on a parallel system with network connections between neighboring nodes, such as the 3-D torus used in Cray XT™ and Cray XE6 systems [2, 3]. Mappin ...
... locality in the underlying physical process being simulated. Applications with regular data decomposition (e.g., a 2-D mesh) can be executed efficiently on a parallel system with network connections between neighboring nodes, such as the 3-D torus used in Cray XT™ and Cray XE6 systems [2, 3]. Mappin ...
A Server-mediated Peer-to-peer System
... and assisted-search. In the experiment, a JWire peer and 2 assisting peers connected to different nodes in the network. Although the network segments of the three involved peers might overlap, each of them must connect to network subsegments to which the other two did not connect. Our focus in this ...
... and assisted-search. In the experiment, a JWire peer and 2 assisting peers connected to different nodes in the network. Although the network segments of the three involved peers might overlap, each of them must connect to network subsegments to which the other two did not connect. Our focus in this ...
Security+ Guide to Network Security Fundamentals
... • An example of obscurity would be not revealing the type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
... • An example of obscurity would be not revealing the type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
RSVP: The ReSerVation Protocol
... • Policy control determines whether the user has administrative permission to make the reservation. • In the future, authentication, access control and accounting for reservation will also be implemented by policy control. • Admission control keeps track of the system resources and determines whethe ...
... • Policy control determines whether the user has administrative permission to make the reservation. • In the future, authentication, access control and accounting for reservation will also be implemented by policy control. • Admission control keeps track of the system resources and determines whethe ...
1. Introduction
... 2.2.2Pastry routing procedure The Pastry routing procedure is as follows [4]: Given a message, a node first tries to route the message to its leaf set. If the key is not represented in the leaf set, the node then tries to forward the message to an entry in its routing table that shares a common pref ...
... 2.2.2Pastry routing procedure The Pastry routing procedure is as follows [4]: Given a message, a node first tries to route the message to its leaf set. If the key is not represented in the leaf set, the node then tries to forward the message to an entry in its routing table that shares a common pref ...
Embedded Solutions
... to distant resources. Satellite links are constrained by the number of packets per second (pps) they can transmit. This is a problem for voice over IP or other applications that generate a large number of small packets. It is typical to run out of pps slots before running out of bandwidth. The IP Mu ...
... to distant resources. Satellite links are constrained by the number of packets per second (pps) they can transmit. This is a problem for voice over IP or other applications that generate a large number of small packets. It is typical to run out of pps slots before running out of bandwidth. The IP Mu ...
ITE PC v4.0 Chapter 1 - Ivailo Chakarov
... • Provides important verification and troubleshooting information • If the data reaches the destination, then the trace lists the interface of every router in the path between the hosts • If the data fails at some hop along the way, the address of the last router that responded to the trace can prov ...
... • Provides important verification and troubleshooting information • If the data reaches the destination, then the trace lists the interface of every router in the path between the hosts • If the data fails at some hop along the way, the address of the last router that responded to the trace can prov ...
Distance Vector Routing Protocols
... – Bandwidth is wasted transporting unnecessary updates. Because RIP updates are broadcast, switches will forward the updates out all ports. – All devices on the LAN must process the update up to the Transport layers, where the receiving device will discard the update. – Advertising updates on a broa ...
... – Bandwidth is wasted transporting unnecessary updates. Because RIP updates are broadcast, switches will forward the updates out all ports. – All devices on the LAN must process the update up to the Transport layers, where the receiving device will discard the update. – Advertising updates on a broa ...
Selective and Early Threat Detection in Large Networked
... The vast majority of attacks targeting networked systems are carried out by self-replicating malware and automatic tools for vulnerability discovery and exploitation. These tools randomly scan the Internet address space looking for reachable targets, and attack them by trying to exploit known vulner ...
... The vast majority of attacks targeting networked systems are carried out by self-replicating malware and automatic tools for vulnerability discovery and exploitation. These tools randomly scan the Internet address space looking for reachable targets, and attack them by trying to exploit known vulner ...
About the Presentations
... Bastion host contains two NICs rather than one One NIC is connected to the external network One is connected to the internal network All traffic must physically go through the firewall to move between the internal and external networks ...
... Bastion host contains two NICs rather than one One NIC is connected to the external network One is connected to the internal network All traffic must physically go through the firewall to move between the internal and external networks ...
Understanding Carrier Ethernet Throughput
... (SFD) serves to align the receiver on the frame to come. The Ethernet header provides most of the Layer 2 local area network addressing information. S-Tags and C-Tags may be applied by the service provider and customer, respectively, to identify specific virtual circuits. Further bytes located farth ...
... (SFD) serves to align the receiver on the frame to come. The Ethernet header provides most of the Layer 2 local area network addressing information. S-Tags and C-Tags may be applied by the service provider and customer, respectively, to identify specific virtual circuits. Further bytes located farth ...
IPv6 Value Proposition
... – For the continued growth and success of the Internet – A natural evolution from IPv4 • Designed with extensibility and scalability in mind ...
... – For the continued growth and success of the Internet – A natural evolution from IPv4 • Designed with extensibility and scalability in mind ...
MSG and PSE Sales Presentation
... Digital Assets Module (MLX) analyzes and classifies your confidential documents and then monitors for that information (or parts of that information) in message stream. ...
... Digital Assets Module (MLX) analyzes and classifies your confidential documents and then monitors for that information (or parts of that information) in message stream. ...
Nodes centralities interference tutorial Example 1 Interference
... The measure shows which fraction of the total betweenness value a node loses or gains with respect to the rest of the network when the node i is removed. Notably, expressing interference values as percentage may facilitate understanding the meaning of the calculated data. The complete analysis of th ...
... The measure shows which fraction of the total betweenness value a node loses or gains with respect to the rest of the network when the node i is removed. Notably, expressing interference values as percentage may facilitate understanding the meaning of the calculated data. The complete analysis of th ...