FREE Sample Here
... generates a unique 4-byte number, the FCS. When the destination node receives the frame, its Data Link layer services unscramble the FCS via the same CRC algorithm and ensure that the frame’s fields match their original form. If this comparison fails, the receiving node assumes that the frame has be ...
... generates a unique 4-byte number, the FCS. When the destination node receives the frame, its Data Link layer services unscramble the FCS via the same CRC algorithm and ensure that the frame’s fields match their original form. If this comparison fails, the receiving node assumes that the frame has be ...
FREE Sample Here
... generates a unique 4-byte number, the FCS. When the destination node receives the frame, its Data Link layer services unscramble the FCS via the same CRC algorithm and ensure that the frame’s fields match their original form. If this comparison fails, the receiving node assumes that the frame has be ...
... generates a unique 4-byte number, the FCS. When the destination node receives the frame, its Data Link layer services unscramble the FCS via the same CRC algorithm and ensure that the frame’s fields match their original form. If this comparison fails, the receiving node assumes that the frame has be ...
downloading
... • It’s modular: – Independent wires for each end node – Independent traffic in each wire – A second layer of switches can be added to build a hierarchical network that extends the same two benefits above – ALWAYS DESIGN WITH MODULARITY IN MIND ...
... • It’s modular: – Independent wires for each end node – Independent traffic in each wire – A second layer of switches can be added to build a hierarchical network that extends the same two benefits above – ALWAYS DESIGN WITH MODULARITY IN MIND ...
20100609-Tier3WS
... – Takes about 2 weeks to upgrade when there is a new ISO – 1 – 2 Weeks to establish the initial testing parameters and set up ...
... – Takes about 2 weeks to upgrade when there is a new ISO – 1 – 2 Weeks to establish the initial testing parameters and set up ...
New Tools on the Bot War Front
... Over the past 10 years, computer attacks have shifted from operating systems to applications. On the client side, the easiest target has become the user with a web browser. Users often browse to a seemingly innocent site and get loaded up with malware that their antivirus isn’t catching. The worst o ...
... Over the past 10 years, computer attacks have shifted from operating systems to applications. On the client side, the easiest target has become the user with a web browser. Users often browse to a seemingly innocent site and get loaded up with malware that their antivirus isn’t catching. The worst o ...
NETWORK LAN PLANNER
... each client shares their resources with Other workstations in the network. Examples of peer-to-peer networks are: Small office networks where resource use is minimal and a home network. A client-server network is where every client is connected to the server and each other. Client-server networks us ...
... each client shares their resources with Other workstations in the network. Examples of peer-to-peer networks are: Small office networks where resource use is minimal and a home network. A client-server network is where every client is connected to the server and each other. Client-server networks us ...
Asymmetric network connectivity using weighted harmonic averages
... not feel close to any node, including Erdös, while Erdös will feel very close to this virtual node due to the large number of paths. We would expect for a tree-like network (where there is a single path between Erdös and any other author) that the transition with E0i = Ei0 would occur for nodes h ...
... not feel close to any node, including Erdös, while Erdös will feel very close to this virtual node due to the large number of paths. We would expect for a tree-like network (where there is a single path between Erdös and any other author) that the transition with E0i = Ei0 would occur for nodes h ...
slides
... RINA over X (Ethernet, TCP, UDP, USB, shared memory, etc.) Support for native RINA applications ...
... RINA over X (Ethernet, TCP, UDP, USB, shared memory, etc.) Support for native RINA applications ...
Ethernet - ECE Users Pages
... Each interface must wait until there is no signal on the channel, then it can begin transmitting. If some other interface is transmitting there will be a signal on the channel, which is called carrier. All other interfaces must wait until carrier ceases before trying to transmit, and this process is ...
... Each interface must wait until there is no signal on the channel, then it can begin transmitting. If some other interface is transmitting there will be a signal on the channel, which is called carrier. All other interfaces must wait until carrier ceases before trying to transmit, and this process is ...
pptx - Cornell Computer Science
... • Next Monday, Review chapter 4 from the book, Network Layer – We will also briefly discuss data center topologies ...
... • Next Monday, Review chapter 4 from the book, Network Layer – We will also briefly discuss data center topologies ...
aaa accounting
... server information used for billing, auditing, and reporting - user identities, start and stop times, executed commands, number of packets, and number of bytes Accounting enables tracking of the services users are accessing as well as the amount of network resources they are consuming With AAA a ...
... server information used for billing, auditing, and reporting - user identities, start and stop times, executed commands, number of packets, and number of bytes Accounting enables tracking of the services users are accessing as well as the amount of network resources they are consuming With AAA a ...
IP Optical Networks
... [5] C. Baransel, W. Dobosiz, P. Gewicburzynski, “Routing in Multihop Packet Switching Networks: Gb/s Challenge”, IEEE Network Magazine, 1995, pp. 38-61. ...
... [5] C. Baransel, W. Dobosiz, P. Gewicburzynski, “Routing in Multihop Packet Switching Networks: Gb/s Challenge”, IEEE Network Magazine, 1995, pp. 38-61. ...
The Broadband Services Router 64000 (BSR 64000) provides
... CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (single router appearanc ...
... CMTS functions and it scales economically to meet ever-increasing subscriber demands and the introduction of new services. The BSR 64000 design is based on centralized routing table calculations and distributed forwarding, and it provides the benefits of simple configuration (single router appearanc ...
l4-1 - Heyook Lab
... – Example: A would not send the first routing update to B, since B is the next hop on A’s current route to C – Split Horizon does not solve count-to-infinity in all cases! » You can produce the count-to-infinity problem in Lab 4. ...
... – Example: A would not send the first routing update to B, since B is the next hop on A’s current route to C – Split Horizon does not solve count-to-infinity in all cases! » You can produce the count-to-infinity problem in Lab 4. ...
Is Your Storage Area Network Secure? An Overview
... confidentiality and integrity, organizations must be aware of all potential points where a security breach might occur and to include these into consideration when designing SAN security solutions. Ability to identify the points of vulnerability and implement a reliable security solution is the key ...
... confidentiality and integrity, organizations must be aware of all potential points where a security breach might occur and to include these into consideration when designing SAN security solutions. Ability to identify the points of vulnerability and implement a reliable security solution is the key ...
Institutionen för systemteknik Multiple Synchronized Video Streams on IP Network
... Video surveillance today can look very different depending on the objective and on the location where it is used. Some applications need a high image resolution and frame rate to carefully analyze the vision of a camera, while other applications could use a poorer resolution and a lower frame rate t ...
... Video surveillance today can look very different depending on the objective and on the location where it is used. Some applications need a high image resolution and frame rate to carefully analyze the vision of a camera, while other applications could use a poorer resolution and a lower frame rate t ...
Part 1
... – Multiple IP packets aggregated into a burst at the ingress node – Data bursts disassembled at the egress node – Packets/bursts buffered at the edge during burst assembly/disassembly ...
... – Multiple IP packets aggregated into a burst at the ingress node – Data bursts disassembled at the egress node – Packets/bursts buffered at the edge during burst assembly/disassembly ...
Gigabit Fiber Ethernets (Optical Ethernet)
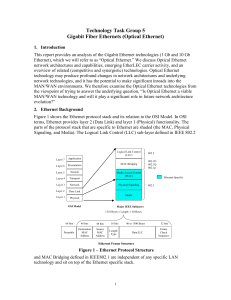
... optics have achieved reaches in the range of 40 to 70 km, and with extenders the reach can be as high as 110 km. With these distance achievements GbE has the capability to connect most, if not all, offices in a metropolitan area without requiring intermediate repeaters or amplification. The standard ...
... optics have achieved reaches in the range of 40 to 70 km, and with extenders the reach can be as high as 110 km. With these distance achievements GbE has the capability to connect most, if not all, offices in a metropolitan area without requiring intermediate repeaters or amplification. The standard ...
슬라이드 1 - University of Minnesota
... Name Directory Service based on MAODV and Multicast DNS for IPv6 MANET ...
... Name Directory Service based on MAODV and Multicast DNS for IPv6 MANET ...
Optical Fibre Communication Systems
... If p 2n -1, the Clos network is strict sense nonblocking (i.e. there will free line that can be used to connect input 1 to output 1) If p n, then the Clos network is re-arrangeably non-blocking (RNB) (i.e. reducing the number of middle stage switches) ...
... If p 2n -1, the Clos network is strict sense nonblocking (i.e. there will free line that can be used to connect input 1 to output 1) If p n, then the Clos network is re-arrangeably non-blocking (RNB) (i.e. reducing the number of middle stage switches) ...
Review, Mobile IP Principals, Cont…
... Review, Power Management, Cont… AP buffers packets to the sleeping nodes AP send Traffic Delivery Information Message (TDIM) that contains the list of nodes that will receive data in that frame, how much data and when. ...
... Review, Power Management, Cont… AP buffers packets to the sleeping nodes AP send Traffic Delivery Information Message (TDIM) that contains the list of nodes that will receive data in that frame, how much data and when. ...
Multimedia Service
... playback can lag tens of seconds after transmission still have timing constraint Interactivity Challenge is the distribution to a large number of concurrent fast forward impossible clients: IP multicast, P2P and rewind, pause possible! content delivery network Streaming Services ...
... playback can lag tens of seconds after transmission still have timing constraint Interactivity Challenge is the distribution to a large number of concurrent fast forward impossible clients: IP multicast, P2P and rewind, pause possible! content delivery network Streaming Services ...