On the Optimal Path Length for Tor
... Also, the compromise rate is the same regardless of whether three- or two-hop paths are used for each malicious router configuration since the attacker gains no advantage from participating in circuits that are not compromised. Now consider an adversary whose routers selectively disrupt circuits on ...
... Also, the compromise rate is the same regardless of whether three- or two-hop paths are used for each malicious router configuration since the attacker gains no advantage from participating in circuits that are not compromised. Now consider an adversary whose routers selectively disrupt circuits on ...
Technical Report DSL Forum TR-059
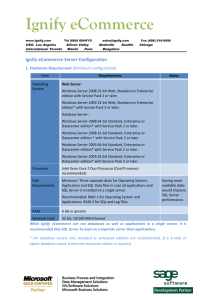
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
Principles of Computer Security
... • An example of a DoS attack targeting a specific protocol or service – Illustrates basic principles of most DoS attacks • Exploit a weakness inherent to the function of the TCP/IP protocol – Uses TCP three-way handshake to flood a system with faked connection requests ...
... • An example of a DoS attack targeting a specific protocol or service – Illustrates basic principles of most DoS attacks • Exploit a weakness inherent to the function of the TCP/IP protocol – Uses TCP three-way handshake to flood a system with faked connection requests ...
Easyln Products for LonWorks
... systems to access field level data. By this standardized interface SCADA systems communicate with PLCs and field busses, production level data are thus integrated into office applications. Even data exchange with other field bus systems is made this way. The Easylon OPC Server was the first OPC serv ...
... systems to access field level data. By this standardized interface SCADA systems communicate with PLCs and field busses, production level data are thus integrated into office applications. Even data exchange with other field bus systems is made this way. The Easylon OPC Server was the first OPC serv ...
Chapter 6
... The Link Layer and LANs A note on the use of these Powerpoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs ...
... The Link Layer and LANs A note on the use of these Powerpoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs ...
00-03-0019-00-0000Linksec_Handoff_Issues_r2
... • Consequently, down at the link layer, an attachment switches from one place to another – Association-authentication-authorization in one of several possible orders and flavors – Either by picking a new attachment point for an interface, or picking a new interface ...
... • Consequently, down at the link layer, an attachment switches from one place to another – Association-authentication-authorization in one of several possible orders and flavors – Either by picking a new attachment point for an interface, or picking a new interface ...
Secure Efficient Distance Vector Routing for Mobile Wireless Ad Hoc
... the address of this node’s neighbor router that is the first hop on this shortest route to that destination; the distance to the destination is known as the metric in that table entry. When routing a packet to some destination, the node transmits the packet to the indicated neighbor router, and each ...
... the address of this node’s neighbor router that is the first hop on this shortest route to that destination; the distance to the destination is known as the metric in that table entry. When routing a packet to some destination, the node transmits the packet to the indicated neighbor router, and each ...
Network Your DIRECTV Plus® HDDVR
... A powerline connection uses your home’s existing power lines to connect your DSL/cable router to your DIRECTV Plus®HD DVR via an Ethernet Adapter that uses HomePlug(R) or a similar power line technology. Two Ethernet Adapters are needed: one to connect to the router and one to connect to the DIRECTV ...
... A powerline connection uses your home’s existing power lines to connect your DSL/cable router to your DIRECTV Plus®HD DVR via an Ethernet Adapter that uses HomePlug(R) or a similar power line technology. Two Ethernet Adapters are needed: one to connect to the router and one to connect to the DIRECTV ...
FIG. 18.3 Determining the effect of the voltage source E
... zero (short-circuit representation) and current sources to zero (open-circuit representation). The current through, or voltage across, a portion of the network produced by each source was then added algebraically to find the total solution for the current or voltage. ...
... zero (short-circuit representation) and current sources to zero (open-circuit representation). The current through, or voltage across, a portion of the network produced by each source was then added algebraically to find the total solution for the current or voltage. ...
DVB-RCS presentation at Bhubaneswar
... The link from SIT to Hub is called Return Link (RL) and it is responsible to carry the return link traffic using Multi-Frequency Time Division Multiple Access (MF-TDMA) based on ATM or MPEG standard. Single SIT allows data rate up to 2 Mbps. Presently each SIT is configured in Hub for Maximum 624 / ...
... The link from SIT to Hub is called Return Link (RL) and it is responsible to carry the return link traffic using Multi-Frequency Time Division Multiple Access (MF-TDMA) based on ATM or MPEG standard. Single SIT allows data rate up to 2 Mbps. Presently each SIT is configured in Hub for Maximum 624 / ...
PDF
... ARP. Whenever a host needs to discover its default gateway, it initiates an ARP request. During this event, the default gateway creates a cache entry for this end host: an ARP entry. This ARP entry times out after the time specified in the preconfigured timer elapses. Occasionally, the end host rese ...
... ARP. Whenever a host needs to discover its default gateway, it initiates an ARP request. During this event, the default gateway creates a cache entry for this end host: an ARP entry. This ARP entry times out after the time specified in the preconfigured timer elapses. Occasionally, the end host rese ...
Rudimentary NMS Software Components (Chapter 7)
... Layer 3 VPNs provide a much more scalable solution because the number of connections required is proportional to a number of sites, not the square of the number of sites. Layer 3 VPNs avoid the need for a full mesh between all of the ...
... Layer 3 VPNs provide a much more scalable solution because the number of connections required is proportional to a number of sites, not the square of the number of sites. Layer 3 VPNs avoid the need for a full mesh between all of the ...
Success Probability of Multiple-Preamble Based Single
... D. Trade-off between collision probability and code ambiguity Although Multi-preamble RA can significantly reduce collision probability, this has a trade-off with its code ambiguity. In case of a codeword length of n = 1 (as in LTE) there is no code-ambiguity, and resource utilisation is 1; however, ...
... D. Trade-off between collision probability and code ambiguity Although Multi-preamble RA can significantly reduce collision probability, this has a trade-off with its code ambiguity. In case of a codeword length of n = 1 (as in LTE) there is no code-ambiguity, and resource utilisation is 1; however, ...
SNMP (Simple Network Management Protocol)
... •Traps are unrequested event reports that are sent to a management system by an SNMP agent process •When a trappable event occurs, a trap message is generated by the agent and is sent to a trap destination (a specific, configured network address) •Many events can be configured to signal a trap, like ...
... •Traps are unrequested event reports that are sent to a management system by an SNMP agent process •When a trappable event occurs, a trap message is generated by the agent and is sent to a trap destination (a specific, configured network address) •Many events can be configured to signal a trap, like ...
P2P Doctor - Computer Science Division
... – 9.3% of such peers has unroutable peers in their buddy list (discovered by peer exchange). – Those 9.3% of peers are high affected by unroutable peers – None of them in the Anti-P2P blacklist – 6 out of the top 10 peers in terms of number of connection they issued to the honeynet are running Linux ...
... – 9.3% of such peers has unroutable peers in their buddy list (discovered by peer exchange). – Those 9.3% of peers are high affected by unroutable peers – None of them in the Anti-P2P blacklist – 6 out of the top 10 peers in terms of number of connection they issued to the honeynet are running Linux ...
IETF GEOPRIV Status - Emergency Services Workshop
... Configuring endpoints with location Transmitting location between points Requesting location information ...
... Configuring endpoints with location Transmitting location between points Requesting location information ...
3rd Edition, Chapter 5 - Ursinus College Student, Faculty and Staff
... cocktail party (shared air, acoustical) Data Link Layer 5-18 ...
... cocktail party (shared air, acoustical) Data Link Layer 5-18 ...
PPT - Communications
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Routed via this entity, and the SourceRoute optio ...
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this counter will include only those packets which were Source-Routed via this entity, and the SourceRoute optio ...
Improving Tor using a TCP-over-DTLS Tunnel
... (CWND) is a variable that stores the number of packets that TCP is currently willing to send to the peer. When the number of packets in flight exceeds the congestion window then the sending of more data is throttled until acknowledgments are received. Once congestion throttles sending, the data queu ...
... (CWND) is a variable that stores the number of packets that TCP is currently willing to send to the peer. When the number of packets in flight exceeds the congestion window then the sending of more data is throttled until acknowledgments are received. Once congestion throttles sending, the data queu ...
RelNotes
... upgrading from an older version of PROSet. It is recommended that you uninstall the older version of PROSet before performing an upgrade. If you are installing a driver in a computer with existing Intel adapters, be sure to update all adapters with the same new software. This will ensure that all ad ...
... upgrading from an older version of PROSet. It is recommended that you uninstall the older version of PROSet before performing an upgrade. If you are installing a driver in a computer with existing Intel adapters, be sure to update all adapters with the same new software. This will ensure that all ad ...