paper
... Electronics at MIT focusing on network coding for video networking. She was previously an invited scientist at the MIT Media Laboratory where she is still involved in a class on converged video applicat ...
... Electronics at MIT focusing on network coding for video networking. She was previously an invited scientist at the MIT Media Laboratory where she is still involved in a class on converged video applicat ...
Network layer
... characteristics of transmission medium signal levels data rates other related matters ...
... characteristics of transmission medium signal levels data rates other related matters ...
Introduction Networking involves connecting computers and other
... sharing information and resources and for communication. Even though the concept of networking is basic, a great deal of technology is required for one device to connect and communicate with another, and many choices for physical connections and related software are possible. Network media The most ...
... sharing information and resources and for communication. Even though the concept of networking is basic, a great deal of technology is required for one device to connect and communicate with another, and many choices for physical connections and related software are possible. Network media The most ...
“Narrow Waist” of the Internet Key to its Success
... Michel Machado, Arvind Mukundan, Wenfei, Aditya Akella, David Andersen, John Byers, Srinivasan Seshan, Peter Steenkiste, The 9th USENIX Symposium on Networked Systems Design and Implementation (NSDI '12), San Jose, CA, April 2012. “XIA: An Architecture for an Evolvable and Trustworthy Internet”, As ...
... Michel Machado, Arvind Mukundan, Wenfei, Aditya Akella, David Andersen, John Byers, Srinivasan Seshan, Peter Steenkiste, The 9th USENIX Symposium on Networked Systems Design and Implementation (NSDI '12), San Jose, CA, April 2012. “XIA: An Architecture for an Evolvable and Trustworthy Internet”, As ...
Network Segmentation Through Policy Abstraction
... Hans Keller VP, IT Operations, at Erickson Living, a multi-state assisted living community builder had a unique network and security need. The organization over all provides living accommodations for 23,000 residents in 17 communities spread across ten states and employs a staff of 13,000. There are ...
... Hans Keller VP, IT Operations, at Erickson Living, a multi-state assisted living community builder had a unique network and security need. The organization over all provides living accommodations for 23,000 residents in 17 communities spread across ten states and employs a staff of 13,000. There are ...
White Paper - DC
... To understand why standard wireless networks do not work well for industrial applications, it is important to distinguish between control and sensing networks versus data networks. Wireless data networks are primarily designed to link together computers, PDAs, printers, Internet access points, etc. ...
... To understand why standard wireless networks do not work well for industrial applications, it is important to distinguish between control and sensing networks versus data networks. Wireless data networks are primarily designed to link together computers, PDAs, printers, Internet access points, etc. ...
EL736 Communications Networks II: Design and Algorithms
... locations, flow and capacity allocation given access locations only, determine core locations, link locations, flow and capacity ...
... locations, flow and capacity allocation given access locations only, determine core locations, link locations, flow and capacity ...
Spanning Tree
... take the entire network down Cons – In the past Spanning Tree has slowed Mac logins down - If there is a loop in your network you may not know about it if you don't check your switches *** Recommend using “Rapid Spanning Tree Protocol” if you are going to use this *** ...
... take the entire network down Cons – In the past Spanning Tree has slowed Mac logins down - If there is a loop in your network you may not know about it if you don't check your switches *** Recommend using “Rapid Spanning Tree Protocol” if you are going to use this *** ...
PowerPoint2000 - Computer Sciences Dept.
... • Many applications that run over the Internet have minimum performance requirements • The network is one of the two possible sources of poor performance • Wide area network behavior is unpredictable – IP networks are best effort – Constant change is normal ...
... • Many applications that run over the Internet have minimum performance requirements • The network is one of the two possible sources of poor performance • Wide area network behavior is unpredictable – IP networks are best effort – Constant change is normal ...
WIRELESS NETWORK MANAGED THROUGH SDN
... alarming increase in the number of network elements. The current technology involves deployment of a network administrator who has supervisory rights over the network to manage them. This technique has various drawbacks like Complexity, Inconsistent policies, Inability to scale and Vendor dependence ...
... alarming increase in the number of network elements. The current technology involves deployment of a network administrator who has supervisory rights over the network to manage them. This technique has various drawbacks like Complexity, Inconsistent policies, Inability to scale and Vendor dependence ...
The Payment Device - Verifone Support Portal
... Via IP & IP technologies, it is now possible to have ACCESS to services that were not previously accessible We are no longer bound to “traditional” transaction networks We can leverage the “Internet” to provide services to customers around the globe ...
... Via IP & IP technologies, it is now possible to have ACCESS to services that were not previously accessible We are no longer bound to “traditional” transaction networks We can leverage the “Internet” to provide services to customers around the globe ...
130307-ICN-v4 - UCSD CSE - University of California San Diego
... Scopes allow for information location as well as for control of information dissemination Can be physical…. ...
... Scopes allow for information location as well as for control of information dissemination Can be physical…. ...
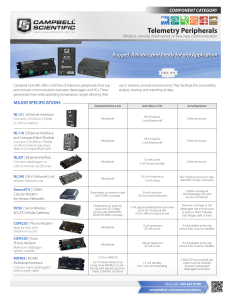
Telemetry Peripherals
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
An Introduction to Computer Networking
... • Computers communicate on single segment of cable and share each other’s data and devices • Simple example of a local area network (LAN) ...
... • Computers communicate on single segment of cable and share each other’s data and devices • Simple example of a local area network (LAN) ...
network-concepts - Home - Websites and Software Solutions
... between users, documents and applications. The data can be used in the for of audio, video, binary, text or graphics. Database server: It is a type of application server. It allows the uses to access the centralised strong database. ...
... between users, documents and applications. The data can be used in the for of audio, video, binary, text or graphics. Database server: It is a type of application server. It allows the uses to access the centralised strong database. ...
Part I: Introduction
... order bits) host part (low order bits) What’s a network ? (from IP address perspective) device interfaces with same network part of IP address can physically reach each other without intervening router ...
... order bits) host part (low order bits) What’s a network ? (from IP address perspective) device interfaces with same network part of IP address can physically reach each other without intervening router ...
IP Addresses - Dr. Wissam Fawaz
... – Telling how to get to distant networks • Some number of local host IP addresses – Telling how to get to local hosts ...
... – Telling how to get to distant networks • Some number of local host IP addresses – Telling how to get to local hosts ...
Intro to internet/WWW
... • We need some sort of address in order to identify different nodes, as if every house has a mailing address in order to receive mail from others • The one used by Internet Protocol is called IP address • Every host on the Internet has a unique IP address, made up of four numbers. E.g.. 192.56.215.1 ...
... • We need some sort of address in order to identify different nodes, as if every house has a mailing address in order to receive mail from others • The one used by Internet Protocol is called IP address • Every host on the Internet has a unique IP address, made up of four numbers. E.g.. 192.56.215.1 ...
090911_KW-LTESecurity-VzW-01
... – Easy to get authentication from home network while in visited network without having to handle Ki ...
... – Easy to get authentication from home network while in visited network without having to handle Ki ...
Slides - TERENA Networking Conference 2010
... Demand access to data Knowledge is power! Demand inter-operability Simpler, cheaper, better Demand security! Ignoring security is so 1990’s. ...
... Demand access to data Knowledge is power! Demand inter-operability Simpler, cheaper, better Demand security! Ignoring security is so 1990’s. ...