Networks, Communities and Kronecker Products
... that they follow a range of properties also found in real networks: heavy tails for in- and out-degrees, clustering coefficient, powerlaw spectrum. They also densify and have shrinking diameter. One can interpret the diagonal values of the initiator matrix as the proportion of edges inside each of t ...
... that they follow a range of properties also found in real networks: heavy tails for in- and out-degrees, clustering coefficient, powerlaw spectrum. They also densify and have shrinking diameter. One can interpret the diagonal values of the initiator matrix as the proportion of edges inside each of t ...
PowerPoint - University of Calgary
... another (sub)net but must be electronically reconfigured. - It’s less resource-efficient (every computer must have it’s own IP). - It’s less secure (the computer is “an unmoving target” because once a malicious program has found it, returning to that computer is trivial). ...
... another (sub)net but must be electronically reconfigured. - It’s less resource-efficient (every computer must have it’s own IP). - It’s less secure (the computer is “an unmoving target” because once a malicious program has found it, returning to that computer is trivial). ...
- IEEE Mentor
... We need more use cases motivating why we would want to have voice and video traffic over the smart grid network. The current set of use cases supplied by OpenSG does not currently contain this service. The only video example given in the text is one of surveillance of affected outage areas. It would ...
... We need more use cases motivating why we would want to have voice and video traffic over the smart grid network. The current set of use cases supplied by OpenSG does not currently contain this service. The only video example given in the text is one of surveillance of affected outage areas. It would ...
What is a Communication Network?
... Course Web page: - http://www.eecs.umich.edu/~zmao/eecs589/ - Check it periodically to get the latest information ...
... Course Web page: - http://www.eecs.umich.edu/~zmao/eecs589/ - Check it periodically to get the latest information ...
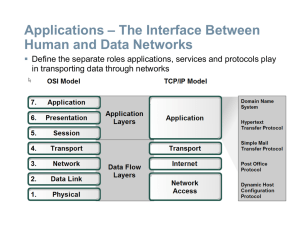
Application Layer Functionality and Protocols
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
... Describe how a switch can eliminate collisions, backoffs and re- transmissions, the leading factors in reduced throughput on a hub-based Ethernet network ...
ppt - Courses
... figure out where the i206 web pages are? • In order for him to use the WWW, Oski’s computer must be connected to another machine acting as a web server (via his ISP). • This machine is in turn connected to other computers, some of which are routers. ...
... figure out where the i206 web pages are? • In order for him to use the WWW, Oski’s computer must be connected to another machine acting as a web server (via his ISP). • This machine is in turn connected to other computers, some of which are routers. ...
$doc.title
... • Write reviews (1 page each) – Summary (problem, solution) – What you like – What could use improvement – What you would do next ...
... • Write reviews (1 page each) – Summary (problem, solution) – What you like – What could use improvement – What you would do next ...
Appendix C Command Line Reference
... NETGEAR ProSafe 802.11g Wireless Access Point WG302v2 Reference Manual Table C-2 Interface Naming Convention (continued) Interface ...
... NETGEAR ProSafe 802.11g Wireless Access Point WG302v2 Reference Manual Table C-2 Interface Naming Convention (continued) Interface ...
Chapter 12 - YSU Computer Science & Information Systems
... – can distribute the AAA information to hundreds or even thousands of access points in a network – uses either the TACACS+ or the RADIUS protocol to provide this network security and tracking – also acts as a central repository for accounting ...
... – can distribute the AAA information to hundreds or even thousands of access points in a network – uses either the TACACS+ or the RADIUS protocol to provide this network security and tracking – also acts as a central repository for accounting ...
2 Structural measures of networks (continued)
... a structural proxy, which is hoped to correlate strongly with the dynamical importance we actually care about. There are a number of such topological measures of importance or centrality. We’ll go through a few of the more common ones. Note that each of these measures has, at its root, a set of theo ...
... a structural proxy, which is hoped to correlate strongly with the dynamical importance we actually care about. There are a number of such topological measures of importance or centrality. We’ll go through a few of the more common ones. Note that each of these measures has, at its root, a set of theo ...
Built-in VPN - NwTech, Inc.
... Client-based access is a good fit for mobile remote users and supports leading client platforms including Google Android, Apple Mac, and Microsoft Windows. Client software versions are conveniently downloadable via their respective web stores. Users are authenticated, for example, via external LDAP ...
... Client-based access is a good fit for mobile remote users and supports leading client platforms including Google Android, Apple Mac, and Microsoft Windows. Client software versions are conveniently downloadable via their respective web stores. Users are authenticated, for example, via external LDAP ...
Hyper-V R2 SP1 is here - Microsoft’s Virtualization
... Enhancements Continues - Network Extending TCP Offload support for Virtual machines VM-Chimney (TCP Offload) allows the CPU workload associated with TCP/IP traffic to be offloaded to the physical NIC, reducing processor usage and increasing network performance. ...
... Enhancements Continues - Network Extending TCP Offload support for Virtual machines VM-Chimney (TCP Offload) allows the CPU workload associated with TCP/IP traffic to be offloaded to the physical NIC, reducing processor usage and increasing network performance. ...
Performance Evaluation of the IEEE 802.16 MAC for QoS Support
... Verify via simulation the ability of IEEE 802.16 MAC to handle multimedia traffic having stringent QoS requirements Determine the best scheduling scheme provided by IEEE 802.16 for multimedia traffic Simulations to be performed on NS-2 ...
... Verify via simulation the ability of IEEE 802.16 MAC to handle multimedia traffic having stringent QoS requirements Determine the best scheduling scheme provided by IEEE 802.16 for multimedia traffic Simulations to be performed on NS-2 ...
Uses of Computer Communications
... Text messaging allows users to send and receive short text messages on a phone or other mobile device or computer Picture messaging allows users to send pictures and sound files Video messaging allows users to send short video clips Wireless instant messaging allows wireless users to exchange real-t ...
... Text messaging allows users to send and receive short text messages on a phone or other mobile device or computer Picture messaging allows users to send pictures and sound files Video messaging allows users to send short video clips Wireless instant messaging allows wireless users to exchange real-t ...
Turn over
... a) The Internet is often described as being a “best effort network”. Briefly explain what is meant by the term “best effort network”. (4 marks). b) Identify, and briefly describe, three QoS parameters that are often measured to characterise the behaviour of a network or network connection. (6 marks) ...
... a) The Internet is often described as being a “best effort network”. Briefly explain what is meant by the term “best effort network”. (4 marks). b) Identify, and briefly describe, three QoS parameters that are often measured to characterise the behaviour of a network or network connection. (6 marks) ...
Chapter 08
... Text messaging allows users to send and receive short text messages on a phone or other mobile device or computer Picture messaging allows users to send pictures and sound files Video messaging allows users to send short video clips Wireless instant messaging allows wireless users to exchange real-t ...
... Text messaging allows users to send and receive short text messages on a phone or other mobile device or computer Picture messaging allows users to send pictures and sound files Video messaging allows users to send short video clips Wireless instant messaging allows wireless users to exchange real-t ...
Authentication
... be protected in accordance with best practice appropriate for that device.” “Network address servers and those used to resolve addresses shall be protected in accordance with best practice appropriate for that device.” ...
... be protected in accordance with best practice appropriate for that device.” “Network address servers and those used to resolve addresses shall be protected in accordance with best practice appropriate for that device.” ...
Week_Six
... Metro Ethernet technology is based on Ethernet technology to offer the best cost-effective, high speed connectivity for MAN and WAN. DSL technology is a high-bandwidth technology over the traditional copper lines. It is designed to work with two modems at either end of the wire. DSL is a transmissio ...
... Metro Ethernet technology is based on Ethernet technology to offer the best cost-effective, high speed connectivity for MAN and WAN. DSL technology is a high-bandwidth technology over the traditional copper lines. It is designed to work with two modems at either end of the wire. DSL is a transmissio ...
Thursday, April 12, 2007 (Wireless, Ad Hoc)
... • Route discovery protocol used to obtain routes on demand • Caching used to minimize use of discovery ...
... • Route discovery protocol used to obtain routes on demand • Caching used to minimize use of discovery ...
Management Information Systems
... Distributed presentation in which all three components are on the server, but the presentation logic is distributed between the client and the server. Remote presentation in which applications logic and database management are on the server, and the presentation logic is located on the client. Distr ...
... Distributed presentation in which all three components are on the server, but the presentation logic is distributed between the client and the server. Remote presentation in which applications logic and database management are on the server, and the presentation logic is located on the client. Distr ...
IC30304pt2
... IP addresses logically split into two parts. First part identifies network. Second part identifies host on that network. Example: the IP address 192.168.0.20: – 192.168.0.x identifies network. – y.y.y.20 identifies host on network. – We have a network with up to 256 (in fact 254) hosts (.0 and .255 ...
... IP addresses logically split into two parts. First part identifies network. Second part identifies host on that network. Example: the IP address 192.168.0.20: – 192.168.0.x identifies network. – y.y.y.20 identifies host on network. – We have a network with up to 256 (in fact 254) hosts (.0 and .255 ...
Module 1: Introduction to TCP/IP
... Adds error-handling information Sequencing and address information is added to the packet Adds error-checking information and prepares data for going on to the physical connection Packet sent as a bit stream ...
... Adds error-handling information Sequencing and address information is added to the packet Adds error-checking information and prepares data for going on to the physical connection Packet sent as a bit stream ...