Sl no - Sharada Vikas Trust
... Static Mathematical Model gives the relationship between the system attributes when the system is in equilibrium. For example in market model there is balance between supply and demand for commodity and both factors depend upon price. Dynamic Mathematical Model allows the change of system attributes ...
... Static Mathematical Model gives the relationship between the system attributes when the system is in equilibrium. For example in market model there is balance between supply and demand for commodity and both factors depend upon price. Dynamic Mathematical Model allows the change of system attributes ...
2.10 Consider the following sequence of (0,1) random numbers
... © Manuel D. Rossetti, All Rights Reserved Chapter 2 Solutions for Simulation Modeling and Arena, 2nd Edition, by Manuel D. Rossetti, John-Wiley & Sons. ...
... © Manuel D. Rossetti, All Rights Reserved Chapter 2 Solutions for Simulation Modeling and Arena, 2nd Edition, by Manuel D. Rossetti, John-Wiley & Sons. ...
REAL-TIME ANALYSIS OF AGGREGATE NETWORK TRAFFIC FOR
... developing techniques for analyzing network traffic. If efficient analysis tools were available, it could become possible to detect the attacks, anomalies and to appropriately take action to contain the attacks before they have had time to propagate across the network. In this dissertation, we sugge ...
... developing techniques for analyzing network traffic. If efficient analysis tools were available, it could become possible to detect the attacks, anomalies and to appropriately take action to contain the attacks before they have had time to propagate across the network. In this dissertation, we sugge ...
lecture13 - Academic Csuohio
... numbers of packets that receiver is permitted to accept • When packet with (seq num = lower edge of window) arrives – Packet is passed to higher layer – Ack is generated – Window slid down by 1 (remains same size as was initially) ...
... numbers of packets that receiver is permitted to accept • When packet with (seq num = lower edge of window) arrives – Packet is passed to higher layer – Ack is generated – Window slid down by 1 (remains same size as was initially) ...
ppt - EECS: www-inst.eecs.berkeley.edu
... Avoid overhead and delays of ordered, reliable delivery ...
... Avoid overhead and delays of ordered, reliable delivery ...
Bayesian Concept Learning and Application for a Simple Language
... • The goal is to learn indicator function , which defines which elements are in the set . • Consider an example called the number game. • Choose some simple arithmetical concept . ...
... • The goal is to learn indicator function , which defines which elements are in the set . • Consider an example called the number game. • Choose some simple arithmetical concept . ...
Some convergence theorems for stochastic learning
... various responses are possible, and suppose that each such exposure or trial can alter the subject’s response tendencies in the situation. It is assumed that the subject’s response tendencies on trial 71 are determined by his state S, at that time. The set of possible states is denoted S and called ...
... various responses are possible, and suppose that each such exposure or trial can alter the subject’s response tendencies in the situation. It is assumed that the subject’s response tendencies on trial 71 are determined by his state S, at that time. The set of possible states is denoted S and called ...
Communication Systems and Networks
... Suppose that the process is non-homogeneous i.e., the rate varies with time, i.e., λ(t) ≤λ, for all t
... Suppose that the process is non-homogeneous i.e., the rate varies with time, i.e., λ(t) ≤λ, for all t
Lecture notes - UT Computer Science
... We can similarly show that the Fourier transform of FCauchy(γ) (t) is exp(−2π|t|γ). Thus, if X1 ∼ Cauchy(γ1 ), X2 ∼ Cauchy(γ2 ), then: FX1 +X2 (t) = FX1 (t)FX2 (t) = exp (−2π|t|(γ1 + γ2 )) = FCauchy(γ1 +γ2 ) (t) X1 + X2 + . . . Xn ∼ Cauchy(1). n This seemingly violates the law of large numbers which ...
... We can similarly show that the Fourier transform of FCauchy(γ) (t) is exp(−2π|t|γ). Thus, if X1 ∼ Cauchy(γ1 ), X2 ∼ Cauchy(γ2 ), then: FX1 +X2 (t) = FX1 (t)FX2 (t) = exp (−2π|t|(γ1 + γ2 )) = FCauchy(γ1 +γ2 ) (t) X1 + X2 + . . . Xn ∼ Cauchy(1). n This seemingly violates the law of large numbers which ...
A numerical characteristic of extreme values
... Rapidly varying tail distributions are various. · Very rapid tail decay : the normal distribution and the Rayleigh distribution. · Middle tail decay: the exponential type, i.e. the exponential distribution, the Gamma distribution, the Chi-square distribution, the generalized inverse Gaussian distri ...
... Rapidly varying tail distributions are various. · Very rapid tail decay : the normal distribution and the Rayleigh distribution. · Middle tail decay: the exponential type, i.e. the exponential distribution, the Gamma distribution, the Chi-square distribution, the generalized inverse Gaussian distri ...
Joint distributions of discrete random variables
... An easier approach is the following: For each of the M phone numbers called, a person a can agree to participate or not (a Bernoulli random variable). For that to happen, two events must occur 1. The phone is answered (with probability π) 2. Given the phone is answered, somebody agrees to participa ...
... An easier approach is the following: For each of the M phone numbers called, a person a can agree to participate or not (a Bernoulli random variable). For that to happen, two events must occur 1. The phone is answered (with probability π) 2. Given the phone is answered, somebody agrees to participa ...
A note on the number of replication runs in
... These sources of randomness are used to represent the diversity of these characteristics, as they are found in reality. However, they have a large effect on the results of the simulation, and different simulation runs can therefore produce very different results, due to a different sequence of rando ...
... These sources of randomness are used to represent the diversity of these characteristics, as they are found in reality. However, they have a large effect on the results of the simulation, and different simulation runs can therefore produce very different results, due to a different sequence of rando ...
Documentation
... can you decide whether an exponential function is a suitable description? (We will talk more about this in the second module.) (c) What assumptions are made to infer population size from the CBC data? ...
... can you decide whether an exponential function is a suitable description? (We will talk more about this in the second module.) (c) What assumptions are made to infer population size from the CBC data? ...
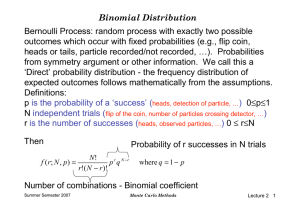
Binomial Distribution Bernoulli Process: random process with
... numbers produced by the algorithm should have the properties we expect for uncorrelated random numbers. Note that having a prescription for generating the random numbers is useful, since we often need reproducible sequences for debugging and reproducibility of programs. ...
... numbers produced by the algorithm should have the properties we expect for uncorrelated random numbers. Note that having a prescription for generating the random numbers is useful, since we often need reproducible sequences for debugging and reproducibility of programs. ...
Linking Cubes - mathmethods4steve
... Once they have built the sequence they should be told to look for patterns both physical and numerical. The following questions should be used along with demonstrations to help students understand the numerical representations of the physical patterns they see. Question 1: How many cubes would you a ...
... Once they have built the sequence they should be told to look for patterns both physical and numerical. The following questions should be used along with demonstrations to help students understand the numerical representations of the physical patterns they see. Question 1: How many cubes would you a ...
Randomness at the root of things 2: Poisson sequences
... a piece of mathematics that is very familiar in Alevel physics. So here goes. Suppose that the probability that no events have arrived after time t is p0 (t). What is the probability p0 (t + dt) that there will still be no event after waiting a further time dt? It is the probability of two things ha ...
... a piece of mathematics that is very familiar in Alevel physics. So here goes. Suppose that the probability that no events have arrived after time t is p0 (t). What is the probability p0 (t + dt) that there will still be no event after waiting a further time dt? It is the probability of two things ha ...
TCP flow control and congestion control
... TCP Flow Control (Sender behavior) Sender can fill up the spare room in the receiver’s buffer by sending more data Sender maintains the size of data that has already been sent but unacknowledged = bytes_unACKed ...
... TCP Flow Control (Sender behavior) Sender can fill up the spare room in the receiver’s buffer by sending more data Sender maintains the size of data that has already been sent but unacknowledged = bytes_unACKed ...
8th Grade Summer Math Packet
... Print out each packet Work on each one throughout the summer Show all of your work right on the packet (Do not use a separate sheet of paper) Bring your packets with you on the first day of school in September ***Calculators are NOT allowed, unless only used to check your work!*** You will r ...
... Print out each packet Work on each one throughout the summer Show all of your work right on the packet (Do not use a separate sheet of paper) Bring your packets with you on the first day of school in September ***Calculators are NOT allowed, unless only used to check your work!*** You will r ...
Algorithms for Distributions
... for u ∈ [0, 1]. If U is a random variable having the U[0,1] distribution, then Q(U ) has the cdf F . Thus in theory we have a method for generating random numbers X1 , . . . , Xn from any distribution, namely to first generate U [0, 1]’s U1 , . . . , Un and then to get Xi = Q(Ui ). This is easy to d ...
... for u ∈ [0, 1]. If U is a random variable having the U[0,1] distribution, then Q(U ) has the cdf F . Thus in theory we have a method for generating random numbers X1 , . . . , Xn from any distribution, namely to first generate U [0, 1]’s U1 , . . . , Un and then to get Xi = Q(Ui ). This is easy to d ...
MPLS, Transport Intro, TCP Intro
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
... » Could be a “shim” on top of Ethernet/etc.: » Existing routers could act as MPLS switches just by examining that shim -- no radical re-design. Gets flexibility benefits, though not cell switching advantages ...
Probability
... EX: A die is rolled. Find the probability the number showing is even. Even: 2, 4 , 6 # of favorable outcomes = 3 # of total outcomes = 6 ...
... EX: A die is rolled. Find the probability the number showing is even. Even: 2, 4 , 6 # of favorable outcomes = 3 # of total outcomes = 6 ...
Simulation
... The Poisson distribution is the limit of a sequence of binomial distributions with parameters n and pn, where n is increasing to infinity, and pn is decreasing to 0, but where the expected value (or mean) npn converges to a constant λ. The variance npn(1 − pn) converges to this same constant. Thus, ...
... The Poisson distribution is the limit of a sequence of binomial distributions with parameters n and pn, where n is increasing to infinity, and pn is decreasing to 0, but where the expected value (or mean) npn converges to a constant λ. The variance npn(1 − pn) converges to this same constant. Thus, ...
CORD Fabric, Overlay Virtualization, and Service Composition
... Figure 2. Fabric Software and Hardware. The leaf and spine switches are identical Accton 6712 (OCPcertified) switches with 32 40G ports. The only difference is in their usage. The leaf switches use 24 of the 32 ports to connect servers, access blades and metro equipment, reserving 8 of the port ...
... Figure 2. Fabric Software and Hardware. The leaf and spine switches are identical Accton 6712 (OCPcertified) switches with 32 40G ports. The only difference is in their usage. The leaf switches use 24 of the 32 ports to connect servers, access blades and metro equipment, reserving 8 of the port ...
802.11ag The - Silex Technology
... for applications, using different frequency bands to separate VoIP and streamingvideo applications from data transmissions. 802.11a handles the media traffic, and 802.11g carries data traffic. Supporting the dual-band scenario is just about the only reasonable way to handle an enterprise's large cov ...
... for applications, using different frequency bands to separate VoIP and streamingvideo applications from data transmissions. 802.11a handles the media traffic, and 802.11g carries data traffic. Supporting the dual-band scenario is just about the only reasonable way to handle an enterprise's large cov ...