8.2 Interim Agreements on Key Issue #2: QoS
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
TCOM 507 Class 2
... there is no call setup delay which makes them most suited for interactive data applications or high traffic volumes . As such PAMA is used typically to connect high data traffic sites within an organization. SCPC (Single Channel Per Carrier) refers to the usage of a single satellite carrier for carr ...
... there is no call setup delay which makes them most suited for interactive data applications or high traffic volumes . As such PAMA is used typically to connect high data traffic sites within an organization. SCPC (Single Channel Per Carrier) refers to the usage of a single satellite carrier for carr ...
Chapter 7 - SaigonTech
... 2.2.3. Ethernet Error Handling • Collisions are the only type of error for which Ethernet automatically attempts to resend the data • Errors can occur when data is altered in medium – Usually caused by noise or faulty media connections – When the destination computer receives a frame, the CRC is re ...
... 2.2.3. Ethernet Error Handling • Collisions are the only type of error for which Ethernet automatically attempts to resend the data • Errors can occur when data is altered in medium – Usually caused by noise or faulty media connections – When the destination computer receives a frame, the CRC is re ...
Network Reference Model for cdma2000 Spread Spectrum
... The DF is an entity that is responsible for delivering intercepted communications to one or more collection functions. The DFs typically include: • the ability to accept call contents for each intercept subject over one or more channels from each Access function. • the ability to deliver call conten ...
... The DF is an entity that is responsible for delivering intercepted communications to one or more collection functions. The DFs typically include: • the ability to accept call contents for each intercept subject over one or more channels from each Access function. • the ability to deliver call conten ...
Chapter 11
... • RFID tags (continued) – Basic types of tags • Passive tags (most common type) – They are small, can be produced in large quantities at low cost, and do not require battery power – Use the electromagnetic energy in the RF waves • Active tags – Equipped with a battery – Can transmit the signal farth ...
... • RFID tags (continued) – Basic types of tags • Passive tags (most common type) – They are small, can be produced in large quantities at low cost, and do not require battery power – Use the electromagnetic energy in the RF waves • Active tags – Equipped with a battery – Can transmit the signal farth ...
3GPP TSG-SA2 Meeting #30
... WLAN black box. Some of them are stable requirements; others are more points for consideration as it is currently unclear what the decision and consequent requirement will be. The objective of this document is to bring these together in one document, point out that there is a need for further work t ...
... WLAN black box. Some of them are stable requirements; others are more points for consideration as it is currently unclear what the decision and consequent requirement will be. The objective of this document is to bring these together in one document, point out that there is a need for further work t ...
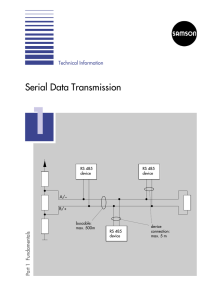
Serial Data Transmission
... Both criteria are influenced by the electric line parameters and the influence increases with the length of the line as well as with the number of participants connected. As a result, each cable type is limited in its line length and maximum number of participants. The higher the signal frequency, t ...
... Both criteria are influenced by the electric line parameters and the influence increases with the length of the line as well as with the number of participants connected. As a result, each cable type is limited in its line length and maximum number of participants. The higher the signal frequency, t ...
Adding Location-Based Services to Existing Architectures
... As described in Examples 1 and 2, the user’s LBS application will be sent information detailing the “location estimate” of a particular mobile subscriber. The information received will include “geographical information,” as described in [3GPP TS 09.02]. “Geographical information” gives the location ...
... As described in Examples 1 and 2, the user’s LBS application will be sent information detailing the “location estimate” of a particular mobile subscriber. The information received will include “geographical information,” as described in [3GPP TS 09.02]. “Geographical information” gives the location ...
Oracle Communications ASAP Product Overview
... Executive Overview Today’s communications industry is characterized by intense competition, limited resources, and continuously shrinking margins. To be successful in this environment, service providers must be first to market with new, differentiated services; offer instant activation of those ser ...
... Executive Overview Today’s communications industry is characterized by intense competition, limited resources, and continuously shrinking margins. To be successful in this environment, service providers must be first to market with new, differentiated services; offer instant activation of those ser ...
True-False Questions
... security and privacy are more difficult. it is best used for cable television. even a radio can pick up the digital signal. Both a and c ...
... security and privacy are more difficult. it is best used for cable television. even a radio can pick up the digital signal. Both a and c ...
- IEEE Mentor
... black box. Some of them are stable requirements; others are more points for consideration as it is currently unclear what the decision and consequent requirement will be. The objective of this document is to bring these together in one document, point out that there is a need for further work to cla ...
... black box. Some of them are stable requirements; others are more points for consideration as it is currently unclear what the decision and consequent requirement will be. The objective of this document is to bring these together in one document, point out that there is a need for further work to cla ...
appendix a: wlan-related terminology - University of Houston
... 5) WEP Key Vulnerability: WEP key based encryption was included to provide same level of data confidentiality in wireless networks as exists in typical wired networks. However a lot of concerns were raised later regarding the usefulness of WEP. Some of them are as following: a. Manual Key Managemen ...
... 5) WEP Key Vulnerability: WEP key based encryption was included to provide same level of data confidentiality in wireless networks as exists in typical wired networks. However a lot of concerns were raised later regarding the usefulness of WEP. Some of them are as following: a. Manual Key Managemen ...
802.11ag The - Silex Technology
... by the receiver) is a function of the transmission environment and does not depend significantly on the transmission frequency. Further, multipath effects are addressed by OFDM, the modulation scheme of choice for both 802.11a and 802.11g. Significant differences in multipath performance thus depend ...
... by the receiver) is a function of the transmission environment and does not depend significantly on the transmission frequency. Further, multipath effects are addressed by OFDM, the modulation scheme of choice for both 802.11a and 802.11g. Significant differences in multipath performance thus depend ...
Md. Zahirul Islam
... beacon LED or FM transmitter on the mobile terminal. These systems are proposed to provide 155 Mb/s ATM access to mobile terminals in a room . Electronic tracking systems have also been proposed which exploit a diffuse optical channel to aid acquisition. The advantage of this topology is that it is ...
... beacon LED or FM transmitter on the mobile terminal. These systems are proposed to provide 155 Mb/s ATM access to mobile terminals in a room . Electronic tracking systems have also been proposed which exploit a diffuse optical channel to aid acquisition. The advantage of this topology is that it is ...
Wireless and IP Communications Technician (CCC
... with challenging academic standards and relevant technical knowledge and skills needed to prepare for further education and careers in the Manufacturing career cluster; provides technical skill proficiency, and includes competency-based applied learning that contributes to the academic knowledge, hi ...
... with challenging academic standards and relevant technical knowledge and skills needed to prepare for further education and careers in the Manufacturing career cluster; provides technical skill proficiency, and includes competency-based applied learning that contributes to the academic knowledge, hi ...
cs2302 computer networks
... campus. Currently LAN size is limited to a few kilometers. It may be from two PC‟s to throughout a company. The most common LAN topologies are bus, ring and star. They have data rates from 4 to 16 Mbps. Today the speed is on increasing and can reach 100 mbps. 2. Metropolitan Area Network: They are d ...
... campus. Currently LAN size is limited to a few kilometers. It may be from two PC‟s to throughout a company. The most common LAN topologies are bus, ring and star. They have data rates from 4 to 16 Mbps. Today the speed is on increasing and can reach 100 mbps. 2. Metropolitan Area Network: They are d ...
Lawful Interception Offering
... Modified ITU-T V.110, according to TS 48.020 A-TRAU, according to TS 48.020 ...
... Modified ITU-T V.110, according to TS 48.020 A-TRAU, according to TS 48.020 ...
Trust, Privacy, and Security - Computer Science
... Slides based on publisher’s slides for 1st and 2nd edition of: Introduction to Wireless and Mobile Systems by Agrawal & Zeng © 2003, 2006, Dharma P. Agrawal and Qing-An Zeng. All rights reserved. Some original slides were modified by L. Lilien, who strived to make such modifications clearly visible. ...
... Slides based on publisher’s slides for 1st and 2nd edition of: Introduction to Wireless and Mobile Systems by Agrawal & Zeng © 2003, 2006, Dharma P. Agrawal and Qing-An Zeng. All rights reserved. Some original slides were modified by L. Lilien, who strived to make such modifications clearly visible. ...
Lecture-01: Course Introduction - University of Colorado Boulder
... • For digital data, to what extent do impairments limit data rate? • Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under given ...
... • For digital data, to what extent do impairments limit data rate? • Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under given ...
Lecture-02: Signals fundamentals
... • For digital data, to what extent do impairments limit data rate? • Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under given ...
... • For digital data, to what extent do impairments limit data rate? • Channel Capacity – the maximum rate at which data can be transmitted over a given communication path, or channel, under given ...
Technical Report
... • ISDN - (2) 64kbps channels - aggregate 128kbs - and higher by combining ISDN lines (video conferencing) • X.25 -The ITT standard for connecting terminal equipment to packet switching data circuits. Max effective speed 2mbps • FRAME RELAY - can offers users transmission speeds of 2.048 megabits per ...
... • ISDN - (2) 64kbps channels - aggregate 128kbs - and higher by combining ISDN lines (video conferencing) • X.25 -The ITT standard for connecting terminal equipment to packet switching data circuits. Max effective speed 2mbps • FRAME RELAY - can offers users transmission speeds of 2.048 megabits per ...
PDF Download(PDF Type,777kbytes)
... consumption, since Optical-Electrical-Optical (O-E-O) conversion in the access central office is not needed. EλAN employs a digital coherent*6 OFDM system with adaptive modulation, a technique that can realize dramatically high optical frequency utilization efficiency and large-scale flexible servic ...
... consumption, since Optical-Electrical-Optical (O-E-O) conversion in the access central office is not needed. EλAN employs a digital coherent*6 OFDM system with adaptive modulation, a technique that can realize dramatically high optical frequency utilization efficiency and large-scale flexible servic ...
(PPT, 328KB)
... for uplink wireless transmission in future mobile communication systems where transmitter power efficiency is of paramount ...
... for uplink wireless transmission in future mobile communication systems where transmitter power efficiency is of paramount ...