namvar-11
... Stuart Russell and Peter Norvig. Artificial Intelligence: A Modern Approach. Prentice Hall Series in Artificial Intelligence, 1995. ...
... Stuart Russell and Peter Norvig. Artificial Intelligence: A Modern Approach. Prentice Hall Series in Artificial Intelligence, 1995. ...
(PPTX 104k)
... A whole system approach to improving practice and reducing delay – we see the Protocol as one element of this For practitioners to have a useful guide and reference point To be in a strong position to achieve the 26 week timescale Improved quality of social work assessments and plans submitted ...
... A whole system approach to improving practice and reducing delay – we see the Protocol as one element of this For practitioners to have a useful guide and reference point To be in a strong position to achieve the 26 week timescale Improved quality of social work assessments and plans submitted ...
Recharter INTRO
... Strawman Reduced Scope ” The near term design goals of the WG are to support small-tomedium sized MANET network areas scaling up to approximately one hundred nodes. Provided progress is made on the core unicast standards, ancillary work may be considered by the WG including development of specifica ...
... Strawman Reduced Scope ” The near term design goals of the WG are to support small-tomedium sized MANET network areas scaling up to approximately one hundred nodes. Provided progress is made on the core unicast standards, ancillary work may be considered by the WG including development of specifica ...
Networking
... Introduced as a protocol suite in the 1970’s to support ARPAnet (American Research Projects Agency), who are the US defence network. After installing TCP/IP on ARPANET in 1983 all devices were configured to use the new protocol. Using this protocol a hybrid network known as the Internet was born. ...
... Introduced as a protocol suite in the 1970’s to support ARPAnet (American Research Projects Agency), who are the US defence network. After installing TCP/IP on ARPANET in 1983 all devices were configured to use the new protocol. Using this protocol a hybrid network known as the Internet was born. ...
A crash course in networking
... – The number of possible sub-groups of network participants is 2N-N-1 , where N is the number of participants. This grows much more rapidly than ...
... – The number of possible sub-groups of network participants is 2N-N-1 , where N is the number of participants. This grows much more rapidly than ...
What is a Network Protocol?
... A protocol is a set of rules that governs the communications between computers on a network.These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transfer. ...
... A protocol is a set of rules that governs the communications between computers on a network.These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transfer. ...
Network protocols - VCE IT Lecture Notes
... Sometimes there is more than one choice of protocol for a task, such as how messages pass across a network (IPX/SPX vs TCP/IP, POP vs IMAP). As long as all the connected computers use the same protocol, it really does not matter which protocol is used (like diplomats agreeing on a language for negot ...
... Sometimes there is more than one choice of protocol for a task, such as how messages pass across a network (IPX/SPX vs TCP/IP, POP vs IMAP). As long as all the connected computers use the same protocol, it really does not matter which protocol is used (like diplomats agreeing on a language for negot ...
Chapter 2 Protocols and Architecture
... May involve different operating systems Protocol specification must be precise ...
... May involve different operating systems Protocol specification must be precise ...
Slide 1
... – is an Internet layer protocol used for establishing dynamic host groups for IP multicasting. ...
... – is an Internet layer protocol used for establishing dynamic host groups for IP multicasting. ...
PPT - ME Kabay
... Protocol Converters Adapt data flow to link systems using dissimilar link-level protocols Code converters translate ASCII and EBCDIC E.g., asynchronous terminal linked to SDLC host ...
... Protocol Converters Adapt data flow to link systems using dissimilar link-level protocols Code converters translate ASCII and EBCDIC E.g., asynchronous terminal linked to SDLC host ...
Document
... • If possible, avoid buffer management using hardware buffering • Run the protocol entirely in the user space In ...
... • If possible, avoid buffer management using hardware buffering • Run the protocol entirely in the user space In ...
Tcp/ip
... • The TCP/IP stack is a four-layered set of protocols for computer networks, including the Internet • A socket is an endpoint of a communication flow on a computer network that uniquely identifies an application and device • HTTP is the set of rules that govern how multimedia files are transmitted a ...
... • The TCP/IP stack is a four-layered set of protocols for computer networks, including the Internet • A socket is an endpoint of a communication flow on a computer network that uniquely identifies an application and device • HTTP is the set of rules that govern how multimedia files are transmitted a ...
An overview
... The header contains sufficient information for implementing the intended services. The header is an overhead to the payload. The payload generally contains a header from another protocol. ...
... The header contains sufficient information for implementing the intended services. The header is an overhead to the payload. The payload generally contains a header from another protocol. ...
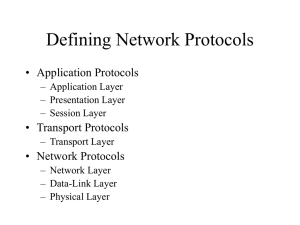
Defining Network Protocols
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
... • Dynamic Host Configuration Protocol • Assigns IP address, gateway (router) address, name server, netmask, time server, and other configuration information based on a NIC’s MAC address • IP addresses may be fixed or taken from a pool of available addresses • Allows assigning temporary addresses for ...
1-ITN-chap-3g
... Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. Internet Protocol - IP is responsible for assigning the appropriate addresses, and delivering them across the best path to the destina ...
... Transport Protocol - Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. Internet Protocol - IP is responsible for assigning the appropriate addresses, and delivering them across the best path to the destina ...
Chapter 10
... Transport layer divides stream into packets Can optimize transfer if knows largest packet size that will fit in one frame If strict layering is used, transport layer will not know the datagram or frame formats, or number of header ...
... Transport layer divides stream into packets Can optimize transfer if knows largest packet size that will fit in one frame If strict layering is used, transport layer will not know the datagram or frame formats, or number of header ...
ppt - CSE Home
... E.g, for cable, take payload, add error protection (ReedSolomon), header and framing, then turn into a signal Modulate data to assigned channel and time (upstream) Downstream, 6 MHz (~30 Mbps), Upstream ~2 MHz (~3 Mbps) ...
... E.g, for cable, take payload, add error protection (ReedSolomon), header and framing, then turn into a signal Modulate data to assigned channel and time (upstream) Downstream, 6 MHz (~30 Mbps), Upstream ~2 MHz (~3 Mbps) ...
ANTS Goals - Networks and Mobile Systems
... Node Operating System • hosts user-defined protocols ...
... Node Operating System • hosts user-defined protocols ...
Communication systems
... Overview of how messages are passed between source and destination 1. Message creation – The message is compiled at the source in preparation for sending, using some type of software application, and perhaps collection of message data from one of the system’s users or participants. 2. Organisation o ...
... Overview of how messages are passed between source and destination 1. Message creation – The message is compiled at the source in preparation for sending, using some type of software application, and perhaps collection of message data from one of the system’s users or participants. 2. Organisation o ...
sample statement
... Biological samples received for protocol number ___________ (sponsor protocol number _____________ [sample: DAC-1001]) will be processed exactly in the manner described in the protocol version approved by the Human Studies Subcommittee and the Research and Development Committee. [option 1:] Document ...
... Biological samples received for protocol number ___________ (sponsor protocol number _____________ [sample: DAC-1001]) will be processed exactly in the manner described in the protocol version approved by the Human Studies Subcommittee and the Research and Development Committee. [option 1:] Document ...