A Three Level Tree Structure Database Architecture for Global
... register (VLR). Each mobile network has a home location register (HLR) where the service profiles of the mobile subscriber like location of the current users and the type of service these users are using. Mobile terminal resides in the Visitor locations register (VLR) and also manage the copy of the ...
... register (VLR). Each mobile network has a home location register (HLR) where the service profiles of the mobile subscriber like location of the current users and the type of service these users are using. Mobile terminal resides in the Visitor locations register (VLR) and also manage the copy of the ...
2. Creating a database Designing the database schema
... ('Ferdinand', 'Magellan', NULL, 'ferdy', NULL, '29/8/2007'); Often you don’t want to allow a field to ever be left empty. You probably want to make sure, for example, that every user has a password. You make sure that any field in a table must contain a value by adding the words NOT NULL after the ...
... ('Ferdinand', 'Magellan', NULL, 'ferdy', NULL, '29/8/2007'); Often you don’t want to allow a field to ever be left empty. You probably want to make sure, for example, that every user has a password. You make sure that any field in a table must contain a value by adding the words NOT NULL after the ...
Slides from Lecture 14 - Courses - University of California, Berkeley
... • It is true, it is the most widely used open source database system with users and uses that range from individuals to major corporations and includes… ...
... • It is true, it is the most widely used open source database system with users and uses that range from individuals to major corporations and includes… ...
Presentation Title
... Coherent Users who see your schema should immediately have a good idea of what they are seeing. • Proper Normalization goes a long way towards this goal ...
... Coherent Users who see your schema should immediately have a good idea of what they are seeing. • Proper Normalization goes a long way towards this goal ...
Computer Forensics
... • Create table for customer users: – Create the CUSTOMERS table – Insert rows into the CUSTOMERS table – Create three users for testing, VPD_CLERK1, VPD_CLERK2, and VPD_CLERK3 – Grant the necessary privileges on the CUSTOMERS table to use each test ...
... • Create table for customer users: – Create the CUSTOMERS table – Insert rows into the CUSTOMERS table – Create three users for testing, VPD_CLERK1, VPD_CLERK2, and VPD_CLERK3 – Grant the necessary privileges on the CUSTOMERS table to use each test ...
Hibernate Vs JDBC - Mindfire Solutions
... -8times for same write. Automatic Transparent Persistence allows the developer to concentrate more on business logic rather than this application code. With JDBC, caching is maintained by handcoding. 7) Automatic Versioning and Time Stamping By database versioning one can be assured that the change ...
... -8times for same write. Automatic Transparent Persistence allows the developer to concentrate more on business logic rather than this application code. With JDBC, caching is maintained by handcoding. 7) Automatic Versioning and Time Stamping By database versioning one can be assured that the change ...
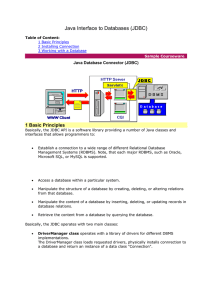
Java Interface to Databases (JDBC)
... should be loaded as a JDBC driver class. Please recollect that almost any modern DBMS supports JDBC. Primitively speaking, there are JDBC drivers for each implementation of DBMS. For example, we can load JDBC driver for MySQL DBMS. ...
... should be loaded as a JDBC driver class. Please recollect that almost any modern DBMS supports JDBC. Primitively speaking, there are JDBC drivers for each implementation of DBMS. For example, we can load JDBC driver for MySQL DBMS. ...
Performance Considerations for the Database Engines
... all rows that make up a page of data. The size of the page can be set to 4K or 32K bytes. A lock on a table would include aU pages of data within the table. A lock on the tablespace would include all tables with the tablespace. The DB2 database engine directly affects locking through the process of ...
... all rows that make up a page of data. The size of the page can be set to 4K or 32K bytes. A lock on a table would include aU pages of data within the table. A lock on the tablespace would include all tables with the tablespace. The DB2 database engine directly affects locking through the process of ...
Database Security:An Introduction
... to another account B, privilege can be given to B with or without the GRANT OPTION. If the GRANT OPTION is given, this means that B can also grant that privilege on R to other accounts. • Suppose that B is given the GRANT OPTION by A and that B then grants the privilege on R to a third account C, ...
... to another account B, privilege can be given to B with or without the GRANT OPTION. If the GRANT OPTION is given, this means that B can also grant that privilege on R to other accounts. • Suppose that B is given the GRANT OPTION by A and that B then grants the privilege on R to a third account C, ...
BRENDA in 2013: integrated reactions, kinetic data, enzyme
... ligands in BRENDA are stored with different names, some with 20 different names like the common adenosine 50 -phosphate (AMP). Using the structural information the ligands in BRENDA are then linked to the ChEBI (3) database of chemical entities of biological interest. In many cases the biochemical r ...
... ligands in BRENDA are stored with different names, some with 20 different names like the common adenosine 50 -phosphate (AMP). Using the structural information the ligands in BRENDA are then linked to the ChEBI (3) database of chemical entities of biological interest. In many cases the biochemical r ...
DBA_Cheat_Sheet
... Find Last Time Database was Accessed The code from the website below shows you the last time any index was accessed. This uses a DMV so the information will be cleared out after a server restart. SELECT last_user_seek = MAX(last_user_seek), last_user_scan = MAX(last_user_scan), ...
... Find Last Time Database was Accessed The code from the website below shows you the last time any index was accessed. This uses a DMV so the information will be cleared out after a server restart. SELECT last_user_seek = MAX(last_user_seek), last_user_scan = MAX(last_user_scan), ...
KorthDB6_ch17 - Internet Database Lab.
... General-purpose computer system: one to a few CPUs and a number of device controllers that are connected through a common bus that provides access to shared memory. ...
... General-purpose computer system: one to a few CPUs and a number of device controllers that are connected through a common bus that provides access to shared memory. ...
Final - NCC Education
... Explain the role of a DBMS (database management system) in a distributed database system. Your answer should refer to the concepts of concurrency control and query optimiser. Any DBMS that needs to operate for a distributed database will be more complex than for a stand-alone database (1 mark). More ...
... Explain the role of a DBMS (database management system) in a distributed database system. Your answer should refer to the concepts of concurrency control and query optimiser. Any DBMS that needs to operate for a distributed database will be more complex than for a stand-alone database (1 mark). More ...
account-number
... branch results in referential-integrity constraint violation, the delete “cascades” to the account relation, deleting the tuple that refers to the branch that was deleted. Cascading updates are similar. ...
... branch results in referential-integrity constraint violation, the delete “cascades” to the account relation, deleting the tuple that refers to the branch that was deleted. Cascading updates are similar. ...
PowerPoint
... What is an Access query? • If you want to see just a portion of the data in a table you can create a query. • A query is a question you ask about the data stored in a database table. • Access responds by displaying the data according to your question. – For example, if you ask to see all the custome ...
... What is an Access query? • If you want to see just a portion of the data in a table you can create a query. • A query is a question you ask about the data stored in a database table. • Access responds by displaying the data according to your question. – For example, if you ask to see all the custome ...
Proximity Search in Databases - Stanford InfoLab
... The graph from Figure 3 is in fact an OEM database, though we have augmented the model to support weights on edges. To generate the Find and Near sets for our proximity measurement, our application simply takes keywords as input. Note that in an OEM database, a keyword could identify an object with ...
... The graph from Figure 3 is in fact an OEM database, though we have augmented the model to support weights on edges. To generate the Find and Near sets for our proximity measurement, our application simply takes keywords as input. Note that in an OEM database, a keyword could identify an object with ...
Compile-Time Path Expansion in Lore 1
... path expression operators with the actual set of possible matching paths, eliminating unnecessary exploration of the full database at run-time. Cycles must be handled carefully: the semantics of Lorel is to traverse a data cycle no more than once when evaluating a path expression with a closure oper ...
... path expression operators with the actual set of possible matching paths, eliminating unnecessary exploration of the full database at run-time. Cycles must be handled carefully: the semantics of Lorel is to traverse a data cycle no more than once when evaluating a path expression with a closure oper ...
DBA Cheat Sheet
... Find Last Time Database was Accessed The code from the website below shows you the last time any index was accessed. This uses a DMV so the information will be cleared out after a server restart. SELECT last_user_seek = MAX(last_user_seek), last_user_scan = MAX(last_user_scan), ...
... Find Last Time Database was Accessed The code from the website below shows you the last time any index was accessed. This uses a DMV so the information will be cleared out after a server restart. SELECT last_user_seek = MAX(last_user_seek), last_user_scan = MAX(last_user_scan), ...
Open - United States Power Squadrons
... security settings, it may be necessary to go on line manually before this procedure can work. If the “MQ Series Client” software is not available, then the email method may be used. Select menu Import/Request Roster from Website. If the user has an active ISP, DB2000 will go on line and connect to t ...
... security settings, it may be necessary to go on line manually before this procedure can work. If the “MQ Series Client” software is not available, then the email method may be used. Select menu Import/Request Roster from Website. If the user has an active ISP, DB2000 will go on line and connect to t ...
HUAWEI OceanStor S5500T Exchange Server 2010 Solution with
... This solution is intended for medium-to-large enterprise that is planning to deploy Microsoft Exchange Server 2010 on HUAWEI storage and would like to leverage the Exchange Server 2010 mailbox resiliency Database Availability Group (DAG) feature. The solution design represents an Exchange Server 201 ...
... This solution is intended for medium-to-large enterprise that is planning to deploy Microsoft Exchange Server 2010 on HUAWEI storage and would like to leverage the Exchange Server 2010 mailbox resiliency Database Availability Group (DAG) feature. The solution design represents an Exchange Server 201 ...
Presented by Kaberi Nayak Senior Oracle Apps DBA
... Upgrading an Oracle E-Business Suite Release 11i database server and instance from Oracle9i Release 2 (9.2.0), Oracle 10g Release 1 (10.1.0), Oracle 10g Release 2 (10.2.0), or Oracle Database 11g Release 1 (11.1.0) to Oracle Database 11g Release 2 (11.2.0) Applying the latest certified Oracle Databa ...
... Upgrading an Oracle E-Business Suite Release 11i database server and instance from Oracle9i Release 2 (9.2.0), Oracle 10g Release 1 (10.1.0), Oracle 10g Release 2 (10.2.0), or Oracle Database 11g Release 1 (11.1.0) to Oracle Database 11g Release 2 (11.2.0) Applying the latest certified Oracle Databa ...
Configuring Oracle on Linux For Peak Performance
... • Assists developers with difficult database issues • Responsible for ensuring good performance, proper security, as well as backup and recovery strategies Terminology ...
... • Assists developers with difficult database issues • Responsible for ensuring good performance, proper security, as well as backup and recovery strategies Terminology ...