4th Dimension, MS Access, and FileMaker Pro
... applications. Their needs can range from a simple database that tracks songs in an MP3 collection all the way to a multi-user client/server application that supports hundreds or even thousands of users as well as millions of records. The range of needs is quite broad so no database is ideal in all c ...
... applications. Their needs can range from a simple database that tracks songs in an MP3 collection all the way to a multi-user client/server application that supports hundreds or even thousands of users as well as millions of records. The range of needs is quite broad so no database is ideal in all c ...
Chapter 4: SQL
... Host language: A language to which SQL queries are embedded is referred to as a host language. The basic form of these languages follows that of the System R embedding of SQL into PL/I. EXEC SQL statement is used to identify embedded SQL request to the preprocessor ...
... Host language: A language to which SQL queries are embedded is referred to as a host language. The basic form of these languages follows that of the System R embedding of SQL into PL/I. EXEC SQL statement is used to identify embedded SQL request to the preprocessor ...
Azure SQL Database Firewall Security
... Microsoft Azure SQL Database provides a relational database service for Azure and other Internet-based applications. To help protect your data, the Azure SQL Database firewall prevents access to the Azure SQL Database server until you specify which computers have permission. To connect to your Azure ...
... Microsoft Azure SQL Database provides a relational database service for Azure and other Internet-based applications. To help protect your data, the Azure SQL Database firewall prevents access to the Azure SQL Database server until you specify which computers have permission. To connect to your Azure ...
Chapter 22
... Some Classes of Data-Mining Problems Classification : Finding rules that partition the given data ...
... Some Classes of Data-Mining Problems Classification : Finding rules that partition the given data ...
Solutions to Review Questions
... lists of requirements. We create data models representing each user view. A data model that represents a single user view is called a local logical data model. We then merge the local data models to create a global logical data model representing all user views of the company. A diagram representing ...
... lists of requirements. We create data models representing each user view. A data model that represents a single user view is called a local logical data model. We then merge the local data models to create a global logical data model representing all user views of the company. A diagram representing ...
Oracle Database Appliance Frequently Asked Questions
... purchase database and options licenses starting from a minimum of 2 processor cores, up to the system maximum of 24 processor cores. This enables customers to start small, licensing only required cores and purchase additional licenses as business demand grows. ...
... purchase database and options licenses starting from a minimum of 2 processor cores, up to the system maximum of 24 processor cores. This enables customers to start small, licensing only required cores and purchase additional licenses as business demand grows. ...
Optimizing Large Data Handling in SAP ASE for Better
... The most noticeable change was delivered by the optimizer controls and optimization goals. SAP ASE now has optimization goals, which provide hints to the optimizer to choose the right query plan for executing the query. Here are the optimization goals, which can be set at a server, session or query ...
... The most noticeable change was delivered by the optimizer controls and optimization goals. SAP ASE now has optimization goals, which provide hints to the optimizer to choose the right query plan for executing the query. Here are the optimization goals, which can be set at a server, session or query ...
Chapter 1
... processing, and user interfaces are divided into separate areas that are fairly independent of one another ...
... processing, and user interfaces are divided into separate areas that are fairly independent of one another ...
Slides for Ch-15
... 1. For each data item Q, if transaction Ti reads the initial value of Q in schedule S, then transaction Ti must, in schedule S´, also read the initial value of Q. 2. For each data item Q if transaction Ti executes read(Q) in schedule S, and that value was produced by transaction Tj (if any), then tr ...
... 1. For each data item Q, if transaction Ti reads the initial value of Q in schedule S, then transaction Ti must, in schedule S´, also read the initial value of Q. 2. For each data item Q if transaction Ti executes read(Q) in schedule S, and that value was produced by transaction Tj (if any), then tr ...
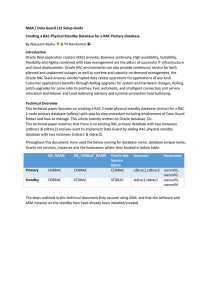
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
... duplicate internally it performs bounce of standby database and whenever instance is closed there will be no more services registered with the listener and hence by setting, we can escape from “ORA-12514: TNS:listener does not currently know of service requested in connect descriptor” and Oracle can ...
... duplicate internally it performs bounce of standby database and whenever instance is closed there will be no more services registered with the listener and hence by setting, we can escape from “ORA-12514: TNS:listener does not currently know of service requested in connect descriptor” and Oracle can ...
MedSchema_Draft - The BioText Project
... (NLM) [1]. PubMed allows individuals to conduct searches directly by entering search terms on web pages and viewing results, and supports software-based queries across the Internet with programming utilities offered by the NLM [2]. Because we were interested in developing custom-made programs that q ...
... (NLM) [1]. PubMed allows individuals to conduct searches directly by entering search terms on web pages and viewing results, and supports software-based queries across the Internet with programming utilities offered by the NLM [2]. Because we were interested in developing custom-made programs that q ...
entity set
... • Example: if we wish to track multiple meeting dates between a student and her advisor, we cannot assume a relationship for each meeting. We can use a multivalued attribute though ...
... • Example: if we wish to track multiple meeting dates between a student and her advisor, we cannot assume a relationship for each meeting. We can use a multivalued attribute though ...
ER Model
... • Example: if we wish to track multiple meeting dates between a student and her advisor, we cannot assume a relationship for each meeting. We can use a multivalued attribute though ...
... • Example: if we wish to track multiple meeting dates between a student and her advisor, we cannot assume a relationship for each meeting. We can use a multivalued attribute though ...
9I DATA GUARD: TRUTH, MYTHS, AND FAILOVER 9i Data Guard
... This two-way communication channel is used to pass requests between sites, and to monitor the health of all of the sites in the broker configuration. The command line interface which is installed when Oracle 9i is installed (by default) is called DGMGRL and its located under $ORACLE_HOME/bin. You do ...
... This two-way communication channel is used to pass requests between sites, and to monitor the health of all of the sites in the broker configuration. The command line interface which is installed when Oracle 9i is installed (by default) is called DGMGRL and its located under $ORACLE_HOME/bin. You do ...
CODESOFT Tutorial
... relationship. Each row in a table is called a record. The purpose of a record is to manage an object, the properties of which are organized across the different columns of the table in the form of fields. A database can contain a number of tables. To link the different tables within a given database ...
... relationship. Each row in a table is called a record. The purpose of a record is to manage an object, the properties of which are organized across the different columns of the table in the form of fields. A database can contain a number of tables. To link the different tables within a given database ...
Database Management Systems Course Content Example for
... check the increase in area of the MBR for each entry when enlarging the MBR to enclose R. Choose Entry with the minimum increase in area (if this entry is not unique, choose the one with the smallest area); enlarge Entry.MBR and follow Entry.Subtree ...
... check the increase in area of the MBR for each entry when enlarging the MBR to enclose R. Choose Entry with the minimum increase in area (if this entry is not unique, choose the one with the smallest area); enlarge Entry.MBR and follow Entry.Subtree ...
Jakarta Torque - PPT
... Adding Functionality to the Object Model The sub classes are used to extend the object model. E.g. : Add toString() functions to the model ...
... Adding Functionality to the Object Model The sub classes are used to extend the object model. E.g. : Add toString() functions to the model ...
MySQL
... Introduction to MySQL for student projects MySQL is a widely used open source relational database management system, developed on the client/server model. The MySQL client is an interactive command-line program that allows you to connect to a MySQL server, run queries and view results (it can also b ...
... Introduction to MySQL for student projects MySQL is a widely used open source relational database management system, developed on the client/server model. The MySQL client is an interactive command-line program that allows you to connect to a MySQL server, run queries and view results (it can also b ...
Implementing Geolocation
... the six DTT multiplexes after DSO, and lies between 470 and 790MHz. This is known as interleaved spectrum because not all this spectrum in any particular location will be used for DTT and so is available for other services as long as they can interleave their usage around the primary users. ...
... the six DTT multiplexes after DSO, and lies between 470 and 790MHz. This is known as interleaved spectrum because not all this spectrum in any particular location will be used for DTT and so is available for other services as long as they can interleave their usage around the primary users. ...
Databases
... – Often the same information was stored in multiple master files. – Made it more difficult to effectively integrate data and obtain an organization-wide view of the data. – Also, the same information may not have been consistent between files. • If a student changed his phone number, it may have bee ...
... – Often the same information was stored in multiple master files. – Made it more difficult to effectively integrate data and obtain an organization-wide view of the data. – Also, the same information may not have been consistent between files. • If a student changed his phone number, it may have bee ...
2.0 The Background of Database Systems
... The second part of the segment presents a set of good practices and guidelines. Good practices for data modeling, schema representation, using CASE tools, data fields naming conventions, third form normalization, using database triggers, and primary key selection are presented for a good design of t ...
... The second part of the segment presents a set of good practices and guidelines. Good practices for data modeling, schema representation, using CASE tools, data fields naming conventions, third form normalization, using database triggers, and primary key selection are presented for a good design of t ...
ITtestPapers.com
... for cleaning up the cache and Freeing resources that the process was using PMON also checks on dispatcher and server processes and restarts them if they have failed. 84. What is the function of ARCH ? Archiver (ARCH) copies the on-line redo log files to archival storage when they are full. ARCH is a ...
... for cleaning up the cache and Freeing resources that the process was using PMON also checks on dispatcher and server processes and restarts them if they have failed. 84. What is the function of ARCH ? Archiver (ARCH) copies the on-line redo log files to archival storage when they are full. ARCH is a ...
Effective Keyword Based Selection of Relational Databases
... measured as a combination of two factors: 1) Proximity factor – Inverse of distance 2) Frequency factor, given a distance d – Number of combinations of exactly d+1 distinct tuples that can be joined in a sequence to get the two keywords in the ...
... measured as a combination of two factors: 1) Proximity factor – Inverse of distance 2) Frequency factor, given a distance d – Number of combinations of exactly d+1 distinct tuples that can be joined in a sequence to get the two keywords in the ...
epiCentre_UserManual_ITAdministrators
... As part of the epiCentre configuration wizard, each client is asked for an encryption key. This encryption key is used for all database encryption. Every client at a facility must be configured with the same encryption key so that they can encrypt and decrypt the data in a common fashion. The benefi ...
... As part of the epiCentre configuration wizard, each client is asked for an encryption key. This encryption key is used for all database encryption. Every client at a facility must be configured with the same encryption key so that they can encrypt and decrypt the data in a common fashion. The benefi ...