Taxonomy of communication networks
... Packet Switching vs. Circuit Switching Advantages of packet switching over circuit switching most important advantage of packet-switching over circuit switching is statistical multiplexing, and therefore more efficient bandwidth usage Disadvantages of packet switching potential congestion: p ...
... Packet Switching vs. Circuit Switching Advantages of packet switching over circuit switching most important advantage of packet-switching over circuit switching is statistical multiplexing, and therefore more efficient bandwidth usage Disadvantages of packet switching potential congestion: p ...
Firewall
... too protocol specific (IPv4 vs. IPv6 vs. ARP, etc.), resulting in code replication when firewall engines are created with iptables ...
... too protocol specific (IPv4 vs. IPv6 vs. ARP, etc.), resulting in code replication when firewall engines are created with iptables ...
- Lancaster University
... packets observed during this time section is 462 which is less than 0.46% of the total number of packets (101620). Further, the size of TCP packets is generally small. On the other hand, UDP datagrams clearly seem to be one of two types. One type is datagrams that are bigger than 600 bytes, most bei ...
... packets observed during this time section is 462 which is less than 0.46% of the total number of packets (101620). Further, the size of TCP packets is generally small. On the other hand, UDP datagrams clearly seem to be one of two types. One type is datagrams that are bigger than 600 bytes, most bei ...
1 Which of the following devices can we use to segment our lan
... (D) A router connects to the Frame Relay network using only one VC to connect various end points (E) Capacity of an access line is based on the maximum bandwidth requirement of the VC 31 Which statements describe features of full-duplex Ethernet? (choose two answers) (A) runs CSMA/CD protocol (B) in ...
... (D) A router connects to the Frame Relay network using only one VC to connect various end points (E) Capacity of an access line is based on the maximum bandwidth requirement of the VC 31 Which statements describe features of full-duplex Ethernet? (choose two answers) (A) runs CSMA/CD protocol (B) in ...
The Data-Link Layer: Access Networks and Lans (Abridged Version)
... different link protocols over different links: e.g., Ethernet on first link, frame relay on intermediate links, 802.11 on last link each link protocol provides different services e.g., may or may not provide rdt over link ...
... different link protocols over different links: e.g., Ethernet on first link, frame relay on intermediate links, 802.11 on last link each link protocol provides different services e.g., may or may not provide rdt over link ...
AD7893 美国模拟器件公司ADI英文数据手册
... 2. Low Power, Single Supply Operation The AD7893 operates from a single +5 V supply and consumes only 25 mW. This low power, single supply operation makes it ideal for battery powered or portable applications. ...
... 2. Low Power, Single Supply Operation The AD7893 operates from a single +5 V supply and consumes only 25 mW. This low power, single supply operation makes it ideal for battery powered or portable applications. ...
last draft
... of octets between applications running on hosts. TCP is resilient against packet loss through retransmission of unacknowledged packets, at the expense of latency. TCP also seeks to fairly fill available bandwidth through expansion of the congestion window until packet loss occurs. TCP works very wel ...
... of octets between applications running on hosts. TCP is resilient against packet loss through retransmission of unacknowledged packets, at the expense of latency. TCP also seeks to fairly fill available bandwidth through expansion of the congestion window until packet loss occurs. TCP works very wel ...
20412002 - Telecommunications Industry Association
... a wired ground in the cable. It is generally undesirable to have both return paths. Cable routing is generally a daisy chain (direct run from chassis to chassis) although some systems may allow stub cabling from a main backbone cable. Each signal pair will normally have a resistor, equal to the char ...
... a wired ground in the cable. It is generally undesirable to have both return paths. Cable routing is generally a daisy chain (direct run from chassis to chassis) although some systems may allow stub cabling from a main backbone cable. Each signal pair will normally have a resistor, equal to the char ...
Weekly Review Slides - CSE Labs User Home Pages
... • Packet-level errors: packet delay or loss due to network congestion/buffer overflow • Out of order delivery: packets may takes different paths • Link/node failures: cable is cut or system crash • [and of course, cyber attacks! –> will not be covered in this class: if interested, take “computer sec ...
... • Packet-level errors: packet delay or loss due to network congestion/buffer overflow • Out of order delivery: packets may takes different paths • Link/node failures: cable is cut or system crash • [and of course, cyber attacks! –> will not be covered in this class: if interested, take “computer sec ...
Slides
... – Must force packets to reach their destination – Without crossing the failed resource • Tunnel to the node after the failed link • Tunnel to an intermediate node ...
... – Must force packets to reach their destination – Without crossing the failed resource • Tunnel to the node after the failed link • Tunnel to an intermediate node ...
Gigabit Multimedia Serial Link Deserializer with LVDS System Interface MAX9268 General Description Features
... deserializer features an LVDS system interface for reduced pin count and a smaller package, and pairs with any GMSL serializer to form a complete digital serial link for joint transmission of high-speed video, audio, and bidirectional control data. ...
... deserializer features an LVDS system interface for reduced pin count and a smaller package, and pairs with any GMSL serializer to form a complete digital serial link for joint transmission of high-speed video, audio, and bidirectional control data. ...
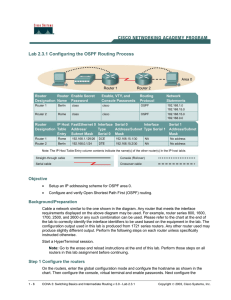
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
Let`s ChronoSync: Decentralized Dataset State Synchronization in
... Fig. 4. 3 Each child node of the tree root holds a cryptographic digest calculated by applying, for example, SHA-256 hash function over a user’s producer status. Recursively applying the same hash function to all child nodes of the root results in the digest that represents state of the whole datase ...
... Fig. 4. 3 Each child node of the tree root holds a cryptographic digest calculated by applying, for example, SHA-256 hash function over a user’s producer status. Recursively applying the same hash function to all child nodes of the root results in the digest that represents state of the whole datase ...
Scott`s review ppt
... Differential connections are typically used with signals under one volt or when the instrumentation does not meet the criteria for RSE. In a system wired for differential inputs, each input has its own reference. Differential inputs are also useful as they eliminate noise problems because any common ...
... Differential connections are typically used with signals under one volt or when the instrumentation does not meet the criteria for RSE. In a system wired for differential inputs, each input has its own reference. Differential inputs are also useful as they eliminate noise problems because any common ...
PMIPv6 Implementation on NS-3 - LINK@KoreaTech
... home network prefix and other parameters MAG will emulate the home link on its access link. MN always obtain its “home network prefix”, any where in the network. It will ensure that MN believes it is at its home. ...
... home network prefix and other parameters MAG will emulate the home link on its access link. MN always obtain its “home network prefix”, any where in the network. It will ensure that MN believes it is at its home. ...
unigate® cl
... The Protocol Developer supports a variety of functions to fit the received or to send data into the right “form”. Mathematics- or memory processing commands are known from other Script languages and are easy to understand implemented, even for laymen. ...
... The Protocol Developer supports a variety of functions to fit the received or to send data into the right “form”. Mathematics- or memory processing commands are known from other Script languages and are easy to understand implemented, even for laymen. ...
Serial digital interface
.jpg?width=300)
Serial digital interface (SDI) is a family of digital video interfaces first standardized by SMPTE (The Society of Motion Picture and Television Engineers) in 1989. For example, ITU-R BT.656 and SMPTE 259M define digital video interfaces used for broadcast-grade video. A related standard, known as high-definition serial digital interface (HD-SDI), is standardized in SMPTE 292M; this provides a nominal data rate of 1.485 Gbit/s.Additional SDI standards have been introduced to support increasing video resolutions (HD, UHD and beyond), frame rates, stereoscopic (3D) video, and color depth. Dual link HD-SDI consists of a pair of SMPTE 292M links, standardized by SMPTE 372M in 1998; this provides a nominal 2.970 Gbit/s interface used in applications (such as digital cinema or HDTV 1080P) that require greater fidelity and resolution than standard HDTV can provide. 3G-SDI (standardized in SMPTE 424M) consists of a single 2.970 Gbit/s serial link that allows replacing dual link HD-SDI. As of August 2014, 6G-SDI and 12G-SDI products are already in the market, although their corresponding standards are still in proposal phase.These standards are used for transmission of uncompressed, unencrypted digital video signals (optionally including embedded audio and time code) within television facilities; they can also be used for packetized data. Coaxial variants of the specification range in length but are typically less than 300 meters. Fiber optic variants of the specification such as 297M allow for long-distance transmission limited only by maximum fiber length or repeaters. SDI and HD-SDI are usually available only in professional video equipment because various licensing agreements restrict the use of unencrypted digital interfaces, such as SDI, prohibiting their use in consumer equipment. Several professional video and HD-video capable DSLR cameras and all uncompressed video capable consumer cameras use the HDMI interface, often called Clean HDMI. There are various mod kits for existing DVD players and other devices, which allow a user to add a serial digital interface to these devices.