Mobile Applications and Web Services
... − There could be a requirement for programming some parts of an application (for example in a WSN environment) after deployment. Some of the reasons for this could be: − The complete deployment setting and requirements may not be know prior to the deployment and as a result the network may not funct ...
... − There could be a requirement for programming some parts of an application (for example in a WSN environment) after deployment. Some of the reasons for this could be: − The complete deployment setting and requirements may not be know prior to the deployment and as a result the network may not funct ...
tutorial7
... • The algorithm is robust for topology changes • However, it has 2 drawbacks: – Packets are flooded to the whole network on the periodic basis – All routers must keep state on a per-group and per-source basis ...
... • The algorithm is robust for topology changes • However, it has 2 drawbacks: – Packets are flooded to the whole network on the periodic basis – All routers must keep state on a per-group and per-source basis ...
Building a trustworthy, secure, and private
... D broadcasts INVALID packet with current sequence = 5, new sequence = 21. S3 examines its route table, the entry to D is not false. S3 forwards packet to S1. S1 finds that its route entry to D has sequence 20, which is > 5. It knows that the route is false. The hop which provides this false route to ...
... D broadcasts INVALID packet with current sequence = 5, new sequence = 21. S3 examines its route table, the entry to D is not false. S3 forwards packet to S1. S1 finds that its route entry to D has sequence 20, which is > 5. It knows that the route is false. The hop which provides this false route to ...
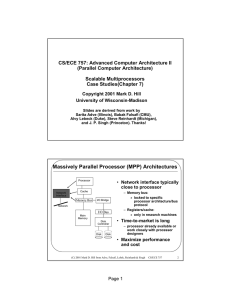
Massively Parallel Processor (MPP) Architectures
... processor may execute routine at address provided by message (active messages) if message queue full; NACK is sent also, error messages may be generated by support circuitry (C) 2003, J. E. Smith ...
... processor may execute routine at address provided by message (active messages) if message queue full; NACK is sent also, error messages may be generated by support circuitry (C) 2003, J. E. Smith ...
Document
... Keys are used for crypting data sent forward/backward. When the onion bounces along, they are stored at each intermediate hop (i.e., OR). ...
... Keys are used for crypting data sent forward/backward. When the onion bounces along, they are stored at each intermediate hop (i.e., OR). ...
Can
... When a collision occurs during arbitration between two or more CAN nodes that transmit at the same time, the node(s) with the lower priority message(s) will detect the collision. The lower priority node(s) will then switch to receiver mode and wait for the next bus idle to attempt transmission again ...
... When a collision occurs during arbitration between two or more CAN nodes that transmit at the same time, the node(s) with the lower priority message(s) will detect the collision. The lower priority node(s) will then switch to receiver mode and wait for the next bus idle to attempt transmission again ...
Distance vector routing protocols
... Sends an update about network 10.1.0.0 out the Serial 0/0/0 interface with a metric of 1. Sends an update about networks 10.2.0.0 with a metric of 1 and 10.3.0.0 with a metric of 2 out the FastEthernet 0/0 interface. Receives an update from R2 about network 10.4.0.0 on Serial 0/0/0 with a metr ...
... Sends an update about network 10.1.0.0 out the Serial 0/0/0 interface with a metric of 1. Sends an update about networks 10.2.0.0 with a metric of 1 and 10.3.0.0 with a metric of 2 out the FastEthernet 0/0 interface. Receives an update from R2 about network 10.4.0.0 on Serial 0/0/0 with a metr ...
from polyu.edu.hk - Department of Electronic and Information
... Digital Interface) format. The MIDI format file stores music information in digital forms that can facilitate repeated performance at later times [14]. Referring to Table 2, tick n is the time mark which indicates the time at which an event occurs. An event is either the start or end of a musical no ...
... Digital Interface) format. The MIDI format file stores music information in digital forms that can facilitate repeated performance at later times [14]. Referring to Table 2, tick n is the time mark which indicates the time at which an event occurs. An event is either the start or end of a musical no ...
192.168.32.112-119
... Simpler to configure, yet more difficult to maintain Very low CPU time-consuming and memoryconsuming Not at all suited for large networks and only marginally suited for redundant topologies Dynamic is: More difficult to configure, but need not be manually maintained up to date Usually mo ...
... Simpler to configure, yet more difficult to maintain Very low CPU time-consuming and memoryconsuming Not at all suited for large networks and only marginally suited for redundant topologies Dynamic is: More difficult to configure, but need not be manually maintained up to date Usually mo ...
Distance Vector Routing Protocols
... Incorrectly configured route redistribution Slow convergence Incorrectly configured discard routes ...
... Incorrectly configured route redistribution Slow convergence Incorrectly configured discard routes ...
2 - Distributed Systems
... Stretch: ratio in delay between overlay path and network‐level path. Example: message from B to C follow path of length 71 in overlay but 47 at network‐level => stretch = 71/47=1.51. Tree cost: total cost of links in the tree ...
... Stretch: ratio in delay between overlay path and network‐level path. Example: message from B to C follow path of length 71 in overlay but 47 at network‐level => stretch = 71/47=1.51. Tree cost: total cost of links in the tree ...
ID Layer for Internet of Things Based on Name
... well as the search and delivery of the information related to them. The idea is to include the ID layer into the network level and offering NON network facilities as, among others, in-network caching of IoT data, ID/location separation and support for multicast. Basically, the proposal is a hierarch ...
... well as the search and delivery of the information related to them. The idea is to include the ID layer into the network level and offering NON network facilities as, among others, in-network caching of IoT data, ID/location separation and support for multicast. Basically, the proposal is a hierarch ...
Security in Automotive Domain Using Secure Socket Layer
... oscillating device. Nodes can be added to the LIN network scientific and medical (ISM) band at 2.45 GHz. It enables without requiring hardware or software changes in other wireless ad-hoc networking of various devices like personal slave nodes. And the maximum transmission speed will be digital assi ...
... oscillating device. Nodes can be added to the LIN network scientific and medical (ISM) band at 2.45 GHz. It enables without requiring hardware or software changes in other wireless ad-hoc networking of various devices like personal slave nodes. And the maximum transmission speed will be digital assi ...
I/O Router Placement and Fine-Grained Routing
... to converge to a single path as it nears the destination. Thus, it is important to avoid putting routers in the same plane. This can help avoid congestion, but many-to-one communication patterns in a 3D torus will always suffer from some amount of congestion. Minimizing the hop count between clients ...
... to converge to a single path as it nears the destination. Thus, it is important to avoid putting routers in the same plane. This can help avoid congestion, but many-to-one communication patterns in a 3D torus will always suffer from some amount of congestion. Minimizing the hop count between clients ...
1 - Cyber-Physical Systems Integration Group @ DGIST
... redundancy, and thus do not require high node density • Data rate: WBANs are employed for monitoring human physiological activities. Thus, the application data streams exhibit relatively stable rates ...
... redundancy, and thus do not require high node density • Data rate: WBANs are employed for monitoring human physiological activities. Thus, the application data streams exhibit relatively stable rates ...
Using PlanetLab for Network Research: Myths, Realities, and Best Practices 1
... community taught us lessons that may shape its continued evolution and may generalize beyond PlanetLab to other systems. First, users do not always search out “best practice” approaches: they expect the straightforward approach to work. Second, users rarely report failed attempts: we learned of the ...
... community taught us lessons that may shape its continued evolution and may generalize beyond PlanetLab to other systems. First, users do not always search out “best practice” approaches: they expect the straightforward approach to work. Second, users rarely report failed attempts: we learned of the ...
Lab 15 - Kno.e.sis
... • TCP/IP applet simulates a reliable communication between two nodes (computers) in a network • DAT – Data packet • ACK – Acknowledgement that data was received without errors • NAK – Negative Acknowledgement which says there was an error in data receiving. CS 1150 – Lab 15 – Networking ...
... • TCP/IP applet simulates a reliable communication between two nodes (computers) in a network • DAT – Data packet • ACK – Acknowledgement that data was received without errors • NAK – Negative Acknowledgement which says there was an error in data receiving. CS 1150 – Lab 15 – Networking ...
OverlayNetworks
... • X sends Ping message to Y; Y forwards Ping message. • All peers receiving Ping message respond with Pong message • X receives many Pong messages. It can then setup additional TCP connections ...
... • X sends Ping message to Y; Y forwards Ping message. • All peers receiving Ping message respond with Pong message • X receives many Pong messages. It can then setup additional TCP connections ...
A Distributed Reputation Approach to Cooperative Internet Routing Protection
... When people look for information about unknown entities, they generally seek the opinions and recommendations of those who they regard to have good reputations. This works quite well in the real world— authentication is no harder than recognizing one’s voice or face, and reputations are persistent a ...
... When people look for information about unknown entities, they generally seek the opinions and recommendations of those who they regard to have good reputations. This works quite well in the real world— authentication is no harder than recognizing one’s voice or face, and reputations are persistent a ...
Lecture 1
... (.255) and a router amplifies (broadcasts) the ping out to every machine on that network – Pinging 129.252.49.255 will send a ping to all the hosts in 129.2522.49.0-129.252.49.255 – This capability should be turned off on routers ...
... (.255) and a router amplifies (broadcasts) the ping out to every machine on that network – Pinging 129.252.49.255 will send a ping to all the hosts in 129.2522.49.0-129.252.49.255 – This capability should be turned off on routers ...
Routing in packet switching networks
... • Best path is based on different metrics: hops, delay, available bandwidth, in general, call them cost. • The best path is one with minimum cost or shortest path. • The routing algorithm must be told which metric to use • The routers exchange (routing) information to obtain values of these metrics ...
... • Best path is based on different metrics: hops, delay, available bandwidth, in general, call them cost. • The best path is one with minimum cost or shortest path. • The routing algorithm must be told which metric to use • The routers exchange (routing) information to obtain values of these metrics ...
Sensor network
... routing path between any two nodes. Furthermore, in each step (other than the last step arriving at the destination), a node can always find a next-hop node that is more than Rc-2Rs closer (in terms of both Euclidean and projected distance) to the destination than itself. ...
... routing path between any two nodes. Furthermore, in each step (other than the last step arriving at the destination), a node can always find a next-hop node that is more than Rc-2Rs closer (in terms of both Euclidean and projected distance) to the destination than itself. ...