ppt - FSU Computer Science
... Analogous to the transport-layer services, but: Service: host-to-host No choice: network provides one or the other Implementation: in the core ...
... Analogous to the transport-layer services, but: Service: host-to-host No choice: network provides one or the other Implementation: in the core ...
information technology
... CT – Class Test (Minimum of two tests to be conducted by the Institute) ESE – University End Semester Examination will be conducted by the institute through concerned affiliating University. Electives: New Electives may be added by the department according to the needs of emerging fields of technolo ...
... CT – Class Test (Minimum of two tests to be conducted by the Institute) ESE – University End Semester Examination will be conducted by the institute through concerned affiliating University. Electives: New Electives may be added by the department according to the needs of emerging fields of technolo ...
Development Kit For the PIC® MCU
... • The SPI byte is set to 0xFE for an EZSP frame. • The length can take values from 3 to 133. The Length byte defines the length of just the EZSP frame and is only included if there is information in the EZSP frame. In case of an error in communication, the length byte is replaced by the Error byte th ...
... • The SPI byte is set to 0xFE for an EZSP frame. • The length can take values from 3 to 133. The Length byte defines the length of just the EZSP frame and is only included if there is information in the EZSP frame. In case of an error in communication, the length byte is replaced by the Error byte th ...
[PDF]
... together constitute a personal area network which is a small scale mobile network. In recent years protocols such as Mobile IPv4 (MIP) and Mobile IPv6 (MIPv6) for supporting seamless connectivity to mobile hosts are developed. To support network mobility extending the existing protocols or developin ...
... together constitute a personal area network which is a small scale mobile network. In recent years protocols such as Mobile IPv4 (MIP) and Mobile IPv6 (MIPv6) for supporting seamless connectivity to mobile hosts are developed. To support network mobility extending the existing protocols or developin ...
Anomaly Detection in Inter-Domain Routing Information
... among ASes and, since the version 4 it deploys a Classless Inter-Domain Routing (CIDR) in order to decrease the size of routing table. BGP was created when the number of ASes involved was much smaller than now and for this reason it was not developed with a perspective of security. Consequently, the ...
... among ASes and, since the version 4 it deploys a Classless Inter-Domain Routing (CIDR) in order to decrease the size of routing table. BGP was created when the number of ASes involved was much smaller than now and for this reason it was not developed with a perspective of security. Consequently, the ...
Interdomain and Policy Routing, BGP, MPLS
... Shannon Capacity (1948): the maximum data rate (C) of a noisy channel with bandwidth B Hz and a given signal-to-noise ratio is: ...
... Shannon Capacity (1948): the maximum data rate (C) of a noisy channel with bandwidth B Hz and a given signal-to-noise ratio is: ...
oneM2M-ARC-2013-0412R01-BRequest_Resource
... • oneM2M-REQ-2013-0260R02 Leveraging Broadcasting/Multicasting Capability of Underlying Networks -- Case of Neighbourhood Alerting on Traffic Accident - This contribution illustrates the case that an automotive telematics service provider alerts Telematics Service Provider vehicles around where a t ...
... • oneM2M-REQ-2013-0260R02 Leveraging Broadcasting/Multicasting Capability of Underlying Networks -- Case of Neighbourhood Alerting on Traffic Accident - This contribution illustrates the case that an automotive telematics service provider alerts Telematics Service Provider vehicles around where a t ...
CCNA Fast Track - K C Communications
... Ethernet II/DIX frame has TYPE field and no LENGTH or 802.2 fields. Ethernet IEEE 802.3 frames have 7 byte preamble, 1 byte SD, Ethernet IEEE 802.3 frames have LENGTH field and no TYPE field, Ethernet IEEE 802.3 frames have 802.2 field for 2 byte DSAP, 2 byte SSAP, 2 control bytes and 5 byte SNAP (i ...
... Ethernet II/DIX frame has TYPE field and no LENGTH or 802.2 fields. Ethernet IEEE 802.3 frames have 7 byte preamble, 1 byte SD, Ethernet IEEE 802.3 frames have LENGTH field and no TYPE field, Ethernet IEEE 802.3 frames have 802.2 field for 2 byte DSAP, 2 byte SSAP, 2 control bytes and 5 byte SNAP (i ...
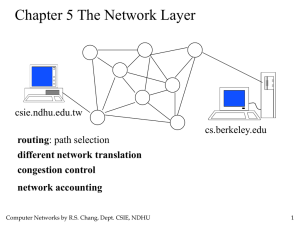
Network Layer
... First, since the delay metric was queue length, it did not take line bandwidth into account when choosing routes. ...
... First, since the delay metric was queue length, it did not take line bandwidth into account when choosing routes. ...
Wireless Mesh Networks - BWN-Lab
... Health and Medical Systems: In a hospital or medical center, monitoring and diagnosis data need to be processed and transmitted from one room to another for various purposes. Data transmission is usually broadband, since high resolution medical images and various periodical monitoring informatio ...
... Health and Medical Systems: In a hospital or medical center, monitoring and diagnosis data need to be processed and transmitted from one room to another for various purposes. Data transmission is usually broadband, since high resolution medical images and various periodical monitoring informatio ...
Banana Tree Protocol, an End-host Multicast Protocol
... packet to its neighbors. When a node receives a multicast packet from its neighbor it forwards the packet to its other neighbors. If a node’s parent leaves or fails, a partition is formed. The node then reconnects to the root. Note that this cannot create a loop because the root cannot be the node’s ...
... packet to its neighbors. When a node receives a multicast packet from its neighbor it forwards the packet to its other neighbors. If a node’s parent leaves or fails, a partition is formed. The node then reconnects to the root. Note that this cannot create a loop because the root cannot be the node’s ...
ppt - UCI
... Split the stream into K stripes (with MDC coding) For each stripe create a multicast tree such that the forest ...
... Split the stream into K stripes (with MDC coding) For each stripe create a multicast tree such that the forest ...
Proceedings of USITS ’03: 4th USENIX Symposium on Internet Technologies and Systems
... link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such rejected links is a constant and this only in ates the expected number of hops by a constant. We also assume that all nodes have accurate knowledge of n. The p ...
... link is \saturated" with 2k incoming links. We account for this implementation detail by noting that provided k = O(1), the fraction of such rejected links is a constant and this only in ates the expected number of hops by a constant. We also assume that all nodes have accurate knowledge of n. The p ...
Pastry: Scalable, Distributed Object Location and Routing for Large-Scale Peer-to-Peer Systems
... unique numeric identi£er (nodeId). When presented with a message and a numeric key, a Pastry node ef£ciently routes the message to the node with a nodeId that is numerically closest to the key, among all currently live Pastry nodes. The expected number of routing steps is O(log N), where N is the nu ...
... unique numeric identi£er (nodeId). When presented with a message and a numeric key, a Pastry node ef£ciently routes the message to the node with a nodeId that is numerically closest to the key, among all currently live Pastry nodes. The expected number of routing steps is O(log N), where N is the nu ...
Pastry: Scalable, decentralized object location and routing for large-scale peer-to-peer systems
... Pastry provides the following capability. Each node in the Pastry network has a unique numeric identifier (nodeId). When presented with a message and a numeric key, a Pastry node efficiently routes the message to the node with a nodeId that is numerically closest to the key, among all currently live ...
... Pastry provides the following capability. Each node in the Pastry network has a unique numeric identifier (nodeId). When presented with a message and a numeric key, a Pastry node efficiently routes the message to the node with a nodeId that is numerically closest to the key, among all currently live ...
Sloppy hashing and self-organizing clusters Michael J. Freedman and David Mazi`eres
... in a normal hash table. Only one value can be stored under a key at any given time. DHTs assume that these keys are uniformly distributed in order to balance load among participating nodes. Additionally, DHTs typically replicate popular key/value pairs after multiple get requests for the same key. ...
... in a normal hash table. Only one value can be stored under a key at any given time. DHTs assume that these keys are uniformly distributed in order to balance load among participating nodes. Additionally, DHTs typically replicate popular key/value pairs after multiple get requests for the same key. ...
RSE-CH4g - wmmhicks.com
... ATM, etc.) while multilayer switches will only have Ethernet interfaces. While routers can be used to segment LAN devices, their major use is as WAN devices. Each devices does have its own advantages. Routers are: The backbone devices of large intranets and of the Internet They operate at ...
... ATM, etc.) while multilayer switches will only have Ethernet interfaces. While routers can be used to segment LAN devices, their major use is as WAN devices. Each devices does have its own advantages. Routers are: The backbone devices of large intranets and of the Internet They operate at ...
An Overview of the Web over Wireless Group
... The Wireless Token Ring Protocol (WTRP) is a medium access control protocol for wireless networks in mission critical systems. It supports quality of service in terms of bounded latency and reserved ...
... The Wireless Token Ring Protocol (WTRP) is a medium access control protocol for wireless networks in mission critical systems. It supports quality of service in terms of bounded latency and reserved ...




![[PDF]](http://s1.studyres.com/store/data/008812144_1-c896fb643c31e300ef7e68c160b2fe7b-300x300.png)