overlay network - Communications
... persistence, streaming, etc. – HyperCast for mobile ad-hoc networks on handheld devices – Service differentiation for multi-stream delivery – Clustering – Integrity and privacy with distributed key management ...
... persistence, streaming, etc. – HyperCast for mobile ad-hoc networks on handheld devices – Service differentiation for multi-stream delivery – Clustering – Integrity and privacy with distributed key management ...
DistanceVectorRouting
... A link state routing protocol finds out about all the routers in the system and the networks they link to. It builds up a complete picture of the topology It can then work out the best path to any network It puts these best paths in the routing table ...
... A link state routing protocol finds out about all the routers in the system and the networks they link to. It builds up a complete picture of the topology It can then work out the best path to any network It puts these best paths in the routing table ...
Waspmote 802.15.4
... 9.1. Structure used in Node Discovery ...................................................................................................................................... 26 9.2. Searching specific nodes............................................................................................... ...
... 9.1. Structure used in Node Discovery ...................................................................................................................................... 26 9.2. Searching specific nodes............................................................................................... ...
MPLS - 中正大學
... replace the label at the top of the label stack with a new label pop the label stack replace and push one or more new labels data link encapsulation how to encode the label stack other information for properly dispose of the packet 中正資工/黃仁竑 ...
... replace the label at the top of the label stack with a new label pop the label stack replace and push one or more new labels data link encapsulation how to encode the label stack other information for properly dispose of the packet 中正資工/黃仁竑 ...
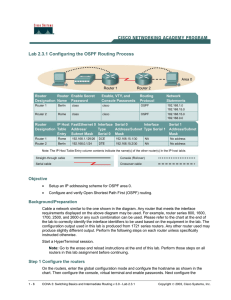
Chp. 3 - Cisco Networking Academy
... When messages are sent between hosts on an Ethernet network, they are sent as frames. The source host formats the messages into the frame format that is specified in the Ethernet standards. Frames are also referred to as Protocol Data Units (PDUs) ...
... When messages are sent between hosts on an Ethernet network, they are sent as frames. The source host formats the messages into the frame format that is specified in the Ethernet standards. Frames are also referred to as Protocol Data Units (PDUs) ...
Trading Structure for Randomness in Wireless Opportunistic Routing
... packets, p1 , but node R is unaware of this fortunate reception. With network coding, node R naturally forwards linear combinations of the received packets. For example, R can send the sum p1 + p2 . The destination retrieves the packet p2 it misses by subtracting from the sum and acks the whole tran ...
... packets, p1 , but node R is unaware of this fortunate reception. With network coding, node R naturally forwards linear combinations of the received packets. For example, R can send the sum p1 + p2 . The destination retrieves the packet p2 it misses by subtracting from the sum and acks the whole tran ...
CDM-625 IEEE 1588v2 Precision Time Protocol (PTP) Performance
... ©2012 Comtech EF Data Corporation ...
... ©2012 Comtech EF Data Corporation ...
EIGRP
... changes are propagated, not the entire routing table, this reduces the load the routing protocol itself places on the network • rapid convergence times for changes in the network topology ...
... changes are propagated, not the entire routing table, this reduces the load the routing protocol itself places on the network • rapid convergence times for changes in the network topology ...
MANETconf: Configuration of Hosts in a Mobile Ad Hoc Network.
... of possible solutions approaches, and discuss their limitations. Then, we present a distributed dynamic host configuration protocol designed to configure nodes in a MANET. We show that the proposed protocol works correctly and does not have the limitations of earlier approaches. Finally, we evaluate ...
... of possible solutions approaches, and discuss their limitations. Then, we present a distributed dynamic host configuration protocol designed to configure nodes in a MANET. We show that the proposed protocol works correctly and does not have the limitations of earlier approaches. Finally, we evaluate ...
PDF Version
... From the preceding discussion, it is clear that treating route failure as congestion and invoking congestion control is not advisable as congestion control and route failure are disparate phenomena which have to be handled independently and separately. Therefore, we propose a scheme by which the sou ...
... From the preceding discussion, it is clear that treating route failure as congestion and invoking congestion control is not advisable as congestion control and route failure are disparate phenomena which have to be handled independently and separately. Therefore, we propose a scheme by which the sou ...
ppt file - University of New Mexico
... reply to a request or, more frequently, an unsolicited regular routing update. In the response packet, a responding system includes all or part of its routing table. Regular routing update messages include the entire routing table. ...
... reply to a request or, more frequently, an unsolicited regular routing update. In the response packet, a responding system includes all or part of its routing table. Regular routing update messages include the entire routing table. ...
3rd Edition: Chapter 4
... range of addresses not needed from ISP: just one IP address for all devices can change addresses of devices in local network ...
... range of addresses not needed from ISP: just one IP address for all devices can change addresses of devices in local network ...
Subnetting & CIDR
... will get one new client with probability 60%, will lose one client with probability 20%, or will maintain the same number with probability 20% ...
... will get one new client with probability 60%, will lose one client with probability 20%, or will maintain the same number with probability 20% ...
Paper - School of Electronic Engineering
... becomes even more important, when one recognizes that the sharing of network resources should be according to flow value (e.g. as quantified through SLA violations) and not necessarily based on flow size solely. To this end, MiceTrap leverages on the OpenFlow group option to handle multiple mice flo ...
... becomes even more important, when one recognizes that the sharing of network resources should be according to flow value (e.g. as quantified through SLA violations) and not necessarily based on flow size solely. To this end, MiceTrap leverages on the OpenFlow group option to handle multiple mice flo ...
ECE544Lec6DR11
... uses meeting places (“rendezvous points”), unidirectional per-group or shared trees, uses unicast routing table (Protocol Independent) ...
... uses meeting places (“rendezvous points”), unidirectional per-group or shared trees, uses unicast routing table (Protocol Independent) ...
ECE544Lec6DR15
... uses meeting places (“rendezvous points”), unidirectional per-group or shared trees, uses unicast routing table (Protocol Independent) ...
... uses meeting places (“rendezvous points”), unidirectional per-group or shared trees, uses unicast routing table (Protocol Independent) ...
Document
... that MN is in fact addressable at its claimed care-of address as well as at its home address Done by testing whether packets addressed to the two claimed addresses are routed to MN MN can pass the test only if it is able to supply proof that it received certain data (the “keygen tokens”) which CN se ...
... that MN is in fact addressable at its claimed care-of address as well as at its home address Done by testing whether packets addressed to the two claimed addresses are routed to MN MN can pass the test only if it is able to supply proof that it received certain data (the “keygen tokens”) which CN se ...
Network Correlated Data Gathering With Explicit
... general case and then we study further a network setting where the entropy conditioning at nodes does not depend on the amount of side information, but only on its availability. We prove that even in this simple case, the optimization problem is NP-hard. We propose some efficient, scalable, and dist ...
... general case and then we study further a network setting where the entropy conditioning at nodes does not depend on the amount of side information, but only on its availability. We prove that even in this simple case, the optimization problem is NP-hard. We propose some efficient, scalable, and dist ...
A Presentation on Design and Implementation of Wavelength
... connects (OXC’s) needed to implement nodes of different designs in a given network. • Discussion on cross-connect and wavelength conversion technologies that could be used at wavelength flexible network nodes. ...
... connects (OXC’s) needed to implement nodes of different designs in a given network. • Discussion on cross-connect and wavelength conversion technologies that could be used at wavelength flexible network nodes. ...