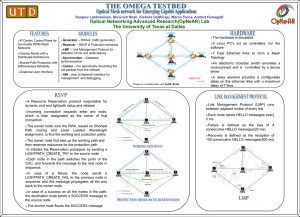
The Next Generation of IP
... The Next Generation of IP Router: This router can store and manage the state information of data flows. ...
... The Next Generation of IP Router: This router can store and manage the state information of data flows. ...
Ad-hoc networks
... Simple routing protocol example Propagation of routing table Routing and transmitting ...
... Simple routing protocol example Propagation of routing table Routing and transmitting ...
An Overlay Network for Forwarding Symbolically Addressed
... the set of ancestor locations, child locations, and the parent location, respectively. Locations of the location model are used to define host positions, and service areas of GRs and GMSs. A benefit of using an overlay network is that our location address space is not restricted by the length limita ...
... the set of ancestor locations, child locations, and the parent location, respectively. Locations of the location model are used to define host positions, and service areas of GRs and GMSs. A benefit of using an overlay network is that our location address space is not restricted by the length limita ...
2. Poison Message Failure Propagation Problem
... • If R1 does not fail, then R1 sends poison LRM to next router R2, and the process repeats at R2. • If any node along the LSP fails, the LSP set-up fails and R0 tries to find another path to Re, and the process continues. • Failed node recovery may initiate LSP reroutes, and rolling instability resu ...
... • If R1 does not fail, then R1 sends poison LRM to next router R2, and the process repeats at R2. • If any node along the LSP fails, the LSP set-up fails and R0 tries to find another path to Re, and the process continues. • Failed node recovery may initiate LSP reroutes, and rolling instability resu ...
Powerpoint
... – Quality of Service at the link level – Quality of Service over multiple paths – Aggregation of flows – Distribution of aggregated flows – Integration of routing and reservations – Transmission of priority packets over multiple paths – CAMP mesh routing ...
... – Quality of Service at the link level – Quality of Service over multiple paths – Aggregation of flows – Distribution of aggregated flows – Integration of routing and reservations – Transmission of priority packets over multiple paths – CAMP mesh routing ...
The Mobile Multi-hop Solution in Ad hoc Networks
... low processing and memory overhead, low network utilization, and determines unicast routes to destinations within the ad hoc network . proactive routing is desirable in a few of situations that only the bandwidth and the energy resources permission. It seams that the bounded improvement are in t ...
... low processing and memory overhead, low network utilization, and determines unicast routes to destinations within the ad hoc network . proactive routing is desirable in a few of situations that only the bandwidth and the energy resources permission. It seams that the bounded improvement are in t ...
Network
... into fixed-length packets which are sent to the destination. Each packet may take a different path through the network. The packets must be reassembled into messages as they arrive. ...
... into fixed-length packets which are sent to the destination. Each packet may take a different path through the network. The packets must be reassembled into messages as they arrive. ...
Document
... • Higher level overlay functionality – Each application designs overlay routing from scratch ...
... • Higher level overlay functionality – Each application designs overlay routing from scratch ...
B.E. Sixth Semester
... Teaching Scheme: Examination Scheme: Lecture: 4 Hours/week Theory: T (U): 80 Marks T (I): 20 Marks Tutorial: 1 Hour/week Duration of University Exam. : 03 Hours ...
... Teaching Scheme: Examination Scheme: Lecture: 4 Hours/week Theory: T (U): 80 Marks T (I): 20 Marks Tutorial: 1 Hour/week Duration of University Exam. : 03 Hours ...
8- Routing
... F detects that link to G has failed F sets distance to G to infinity and sends update to A A sets distance to G to infinity since it uses F to reach G A receives periodic update from C with 2-hop path to G A sets distance to G to 3 and sends update to F F decides it can reach G in 4 hops via A ...
... F detects that link to G has failed F sets distance to G to infinity and sends update to A A sets distance to G to infinity since it uses F to reach G A receives periodic update from C with 2-hop path to G A sets distance to G to 3 and sends update to F F decides it can reach G in 4 hops via A ...
(M1) why are protocols important
... without the agreed connection and transfer instructions provided by protocols Packets of data need to be constructed in the same way and sent across networks in an agreed way otherwise they would not reach their destination Protocols are also essential for the security of data on networks They are n ...
... without the agreed connection and transfer instructions provided by protocols Packets of data need to be constructed in the same way and sent across networks in an agreed way otherwise they would not reach their destination Protocols are also essential for the security of data on networks They are n ...
Week_6
... + Assures in-order execution of all updates Decrease of update frequency Store time between first and best announcement of a path • Inhibit update if it seems to be unstable (based on the stored time values) • + Less traffic • Implemented in Destination Sequenced Distance Vector (DSDV) ...
... + Assures in-order execution of all updates Decrease of update frequency Store time between first and best announcement of a path • Inhibit update if it seems to be unstable (based on the stored time values) • + Less traffic • Implemented in Destination Sequenced Distance Vector (DSDV) ...
You can them from here
... A number of protocols exist Not all protocols have the same features, solve the same problems, or are efficient ...
... A number of protocols exist Not all protocols have the same features, solve the same problems, or are efficient ...
CSC 335 Data Communications and Networking I
... sending Resv messages • Resv messages propagate through internet and is delivered to sender ...
... sending Resv messages • Resv messages propagate through internet and is delivered to sender ...
lecture
... F detects that link to G has failed F sets distance to G to infinity and sends update to A A sets distance to G to infinity since it uses F to reach G A receives periodic update from C with 2-hop path to G A sets distance to G to 3 and sends update to F F decides it can reach G in 4 hops via A ...
... F detects that link to G has failed F sets distance to G to infinity and sends update to A A sets distance to G to infinity since it uses F to reach G A receives periodic update from C with 2-hop path to G A sets distance to G to 3 and sends update to F F decides it can reach G in 4 hops via A ...
mat379.sp05.ExamAnswers
... 10. (10 points) Border Gateway Protocol i. Mention and briefly describe two features of the Border Gateway Protocol (BGP) that make it more suitable for routing in the global Internet than either the Routing Information Protocol (RIP) or the Open Shortest Path First (OSPF) Protocol. BGP allows polic ...
... 10. (10 points) Border Gateway Protocol i. Mention and briefly describe two features of the Border Gateway Protocol (BGP) that make it more suitable for routing in the global Internet than either the Routing Information Protocol (RIP) or the Open Shortest Path First (OSPF) Protocol. BGP allows polic ...
Static Routing Protocols - IT246
... The IP Address of the router in your network where data packets with unknown routes should be forwarded. The purpose is to configure a route for data packets the do not have a destination route configured in the routing table. ip route 0.0.0.0 0.0.0.0 ...
... The IP Address of the router in your network where data packets with unknown routes should be forwarded. The purpose is to configure a route for data packets the do not have a destination route configured in the routing table. ip route 0.0.0.0 0.0.0.0 ...
Study of Geographic Routing Protocols for MANETs
... A node sends packet to one of the reachable intra-domain gateway A route discovery is initiated in the case of reactive domain to find the gateway node which has the route to the destination Once the packet reaches the intra-domain gateway, it checks to see if it is directly connected to the d ...
... A node sends packet to one of the reachable intra-domain gateway A route discovery is initiated in the case of reactive domain to find the gateway node which has the route to the destination Once the packet reaches the intra-domain gateway, it checks to see if it is directly connected to the d ...