Powerpoint
... Normally done by flooding a PC with (useless) requests in order to cut CPU time for the other running processes including GUI. The PC seems to be frozen although he’s only trying to cope with the incoming data and so he’s no ...
... Normally done by flooding a PC with (useless) requests in order to cut CPU time for the other running processes including GUI. The PC seems to be frozen although he’s only trying to cope with the incoming data and so he’s no ...
S - Fitz and Dennis TB ch05 File
... (14) TCP includes a sequence number so that the packets can be reassembled at the destination in the correct order. (15) The latest version of IP is IPv7, which increases the address space from 128 bits to 256 bits. (16) IPX/SPX is the primary network protocol uses by Microsoft networks. (17) IPX is ...
... (14) TCP includes a sequence number so that the packets can be reassembled at the destination in the correct order. (15) The latest version of IP is IPv7, which increases the address space from 128 bits to 256 bits. (16) IPX/SPX is the primary network protocol uses by Microsoft networks. (17) IPX is ...
DL34689693
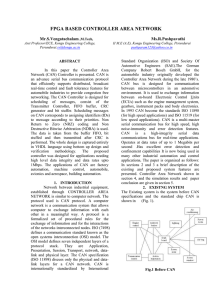
... M.E. Student, E& Ec Department, PEC University of Technology, Chandigarh Supervisor and Head, E& Ec Department, PEC University of Technology, Chandigarh ...
... M.E. Student, E& Ec Department, PEC University of Technology, Chandigarh Supervisor and Head, E& Ec Department, PEC University of Technology, Chandigarh ...
as a PDF
... devising a routing information update protocol, it is necessary to keep in mind that excessive routing information update can be wasteful for network resources, while not enough routing information leads to non-optimal routing. This is especially important in a mobile network, as the host mobility ...
... devising a routing information update protocol, it is necessary to keep in mind that excessive routing information update can be wasteful for network resources, while not enough routing information leads to non-optimal routing. This is especially important in a mobile network, as the host mobility ...
IEEE 802.15 - Survey of Scatternet Formation
... No loops possible Unique paths Therefore simple routing Idea: nodes have unique addresses based upon their position in the tree Mapping from IP to these adresses using ARP (a node returns its scatternet address in response to ARP query) With this identifier, packet forwarding protocol work ...
... No loops possible Unique paths Therefore simple routing Idea: nodes have unique addresses based upon their position in the tree Mapping from IP to these adresses using ARP (a node returns its scatternet address in response to ARP query) With this identifier, packet forwarding protocol work ...
Fundamentals of Computer Networks ECE 478/578
... Congestion control to handle network overloading Running of multiple application processes at the same host ...
... Congestion control to handle network overloading Running of multiple application processes at the same host ...
Analysis of Denial-of-Service attacks on Wireless Sensor Networks
... In the wormhole attacks, a malevolent node excavates the messages it receives at one end of the network over a separate low-latency channel. Then it repeats messages at a different point in the sensor network. For example, when a source node is passing on data to a destination node then there can be ...
... In the wormhole attacks, a malevolent node excavates the messages it receives at one end of the network over a separate low-latency channel. Then it repeats messages at a different point in the sensor network. For example, when a source node is passing on data to a destination node then there can be ...
15-744: Computer Networking
... • Why would IP routing not give good performance? • Policy routing – limits selection/advertisement of routes • Early exit/hot-potato routing – local not global incentives • Lack of performance based metrics – AS hop count is the wide area metric ...
... • Why would IP routing not give good performance? • Policy routing – limits selection/advertisement of routes • Early exit/hot-potato routing – local not global incentives • Lack of performance based metrics – AS hop count is the wide area metric ...
FSR: Formal Analysis and Implementation Toolkit for
... solver determines whether it is possible to jointly satisfy the policy configuration and the safety requirement of “strict monotonicity” (the rightmost input in Figure 1, drawn from previous work [7] on sufficient conditions for safety). If all constraints can be satisfied, the routing system is pr ...
... solver determines whether it is possible to jointly satisfy the policy configuration and the safety requirement of “strict monotonicity” (the rightmost input in Figure 1, drawn from previous work [7] on sufficient conditions for safety). If all constraints can be satisfied, the routing system is pr ...
Chapter 1: Introduction
... (K0,K1,…Ki,…Kn) and publishes the keys in reverse order from generation The sender picks Ki which will still be secret at the time the receiver receives the packet When a receiver receives a packet, it first verifies Ki is still secret, then it buffers the packet and waits for the sender to publish ...
... (K0,K1,…Ki,…Kn) and publishes the keys in reverse order from generation The sender picks Ki which will still be secret at the time the receiver receives the packet When a receiver receives a packet, it first verifies Ki is still secret, then it buffers the packet and waits for the sender to publish ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... LAN has taken its position at various places.According to the consequences obtained by recent research it has ben observed that wireless technology is gaining popularity in world of communication. Now a days people like to stay connected with each other all over the world and also share resources of ...
... LAN has taken its position at various places.According to the consequences obtained by recent research it has ben observed that wireless technology is gaining popularity in world of communication. Now a days people like to stay connected with each other all over the world and also share resources of ...
CAN_Basics_1 - Renesas e
... Basic CAN: CAN peripheral with no hardware filtering. Typically two receive buffers act as a FIFO and accept all bus traffic. Usually one transmit buffer. Bit Time: Nominal time of one bit on the CAN bus. Made up of multiple segments that allow each node to synchronize to the received bus traffic. A ...
... Basic CAN: CAN peripheral with no hardware filtering. Typically two receive buffers act as a FIFO and accept all bus traffic. Usually one transmit buffer. Bit Time: Nominal time of one bit on the CAN bus. Made up of multiple segments that allow each node to synchronize to the received bus traffic. A ...
A Modular Network Layer for Sensornets
... this is too coarse-grained, as it enables little code reuse. Of the two components, the control plane is typically far more complex than the data plane, as it needs to implement non-trivial functionalities such as topology discovery and routing. To facilitate further reuse, we split the control plan ...
... this is too coarse-grained, as it enables little code reuse. Of the two components, the control plane is typically far more complex than the data plane, as it needs to implement non-trivial functionalities such as topology discovery and routing. To facilitate further reuse, we split the control plan ...
ppt
... Headers with errors Headers with IP options Datagrams that require fragmentation Multicast datagrams ...
... Headers with errors Headers with IP options Datagrams that require fragmentation Multicast datagrams ...
Exam Paper Stationery - University of East Anglia
... the role and contents of each data structure you identify. Explain in detail how v2 routes a packet it receives from v5. ...
... the role and contents of each data structure you identify. Explain in detail how v2 routes a packet it receives from v5. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... properly, or sometimes may not work at all, if the packet loss exceeds a specified number, or rate. For example, the video streaming may become waste , after certain streaming video frames are lost. This number may be zero in certain cases. Therefore, certain assurances on the number of rate of lost ...
... properly, or sometimes may not work at all, if the packet loss exceeds a specified number, or rate. For example, the video streaming may become waste , after certain streaming video frames are lost. This number may be zero in certain cases. Therefore, certain assurances on the number of rate of lost ...
Quiz-3 Review - Communications Systems Center
... base station typically connected to wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers 802.11 access points ...
... base station typically connected to wired network relay - responsible for sending packets between wired network and wireless host(s) in its “area” e.g., cell towers 802.11 access points ...
The Impact of SDN On MPLS Networks
... • Retain information about provisioned LSPs • New extensions to PCEP • Allow explicit activation of LSPs from the PCE • Receive information from network about LSPs • Provides key components for bandwidth callendaring ...
... • Retain information about provisioned LSPs • New extensions to PCEP • Allow explicit activation of LSPs from the PCE • Receive information from network about LSPs • Provides key components for bandwidth callendaring ...
Chapter 13
... This picture illustrates why the early system of core routers did not allow default routes. With default routes, a local router would check for an explicit route and if it did not have one, it would use the default route. To ensure global consistency, the chain of default routes must reach every ro ...
... This picture illustrates why the early system of core routers did not allow default routes. With default routes, a local router would check for an explicit route and if it did not have one, it would use the default route. To ensure global consistency, the chain of default routes must reach every ro ...