Statistical Database
... The integrity constraints are kept in catalog. Advantages and disadvantages are similar to security constraint. Wei-Pang Yang, Information Management, NDHU ...
... The integrity constraints are kept in catalog. Advantages and disadvantages are similar to security constraint. Wei-Pang Yang, Information Management, NDHU ...
a. Database
... models: a logical and a physical. A “Logical” model is a representation, often graphical in nature, of the information requirements of a business area, it is not a database. Its main purpose is to ensure that its structure and content can represent and support the business requirements of an area of ...
... models: a logical and a physical. A “Logical” model is a representation, often graphical in nature, of the information requirements of a business area, it is not a database. Its main purpose is to ensure that its structure and content can represent and support the business requirements of an area of ...
How to convert from Visual Fox Pro Database to PostGreSQL
... Computers are used both in our domestic homes and at the industries for different reasons but it cogent purpose is to store and retrieve our data at any point on request. It is a surprising fact though that as much as the world has embraced the computer systems in this present technological era, mos ...
... Computers are used both in our domestic homes and at the industries for different reasons but it cogent purpose is to store and retrieve our data at any point on request. It is a surprising fact though that as much as the world has embraced the computer systems in this present technological era, mos ...
ppt - Avi Silberschatz
... insert into borrower (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account ...
... insert into borrower (select customer-name,account-number from depositor, inserted where inserted.account-number = depositor.account-number) insert into loan values (inserted.account-number, inserted.branch-name, – inserted.balance) update account set balance = 0 from account, inserted where account ...
Elmasri/Navathe, Fundamentals of Database Systems, Fourth Edition
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
Rack servers: Database price performance
... and the number of files per filegroup. We allowed for approximately 40 percent free space in our database files to ensure that filegrowth activity did not occur during the testing. We followed Microsoft’s recommendation of having 0.25 to 1 file per filegroup per core. Both servers under test have fo ...
... and the number of files per filegroup. We allowed for approximately 40 percent free space in our database files to ensure that filegrowth activity did not occur during the testing. We followed Microsoft’s recommendation of having 0.25 to 1 file per filegroup per core. Both servers under test have fo ...
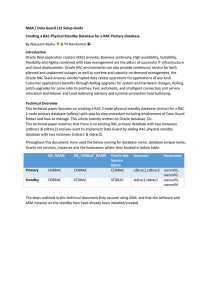
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
... 13. Start Recovery on RAC Physical Standby Database After successful RMAN duplicate and the configuration related to cluster, We can start the MRP (Media Recovery Process) on any one node of the RAC physical standby database. ...
... 13. Start Recovery on RAC Physical Standby Database After successful RMAN duplicate and the configuration related to cluster, We can start the MRP (Media Recovery Process) on any one node of the RAC physical standby database. ...
Elmasri/Navathe, Fundamentals of Database Systems, Fourth Edition
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
Virtual Private Databases
... – Say, we have a table T and many views are based on T. – Suppose we want to restrict access to some information in T. – Without VPD, all view definitions have to be changed. – Using VPD, it can be done by attaching a policy function to T; as the policy is enforced in T, the policy is also enforced ...
... – Say, we have a table T and many views are based on T. – Suppose we want to restrict access to some information in T. – Without VPD, all view definitions have to be changed. – Using VPD, it can be done by attaching a policy function to T; as the policy is enforced in T, the policy is also enforced ...
p1c3justenoughsql
... The Structured Query Language, commonly known as SQL, is a language for interacting with a database. You can pronounce it as three separate letters or as "sequel" if you prefer. SQL came from IBM in the late 1970s and early 1980s, but the main version in use today is that defined by the Internationa ...
... The Structured Query Language, commonly known as SQL, is a language for interacting with a database. You can pronounce it as three separate letters or as "sequel" if you prefer. SQL came from IBM in the late 1970s and early 1980s, but the main version in use today is that defined by the Internationa ...
MYCH4
... Query languages: Allow manipulation and retrieval of data from a database. Relational model supports simple, powerful QLs: ...
... Query languages: Allow manipulation and retrieval of data from a database. Relational model supports simple, powerful QLs: ...
UKOUG2013- Streams vs GoldenGate12c - Openlab
... A lot of (good) features inherited from Streams Improved scalability - performance better than Streams Easier deployment, data instantiation and administration Availability of in-database monitoring and reporting More data types supported ...
... A lot of (good) features inherited from Streams Improved scalability - performance better than Streams Easier deployment, data instantiation and administration Availability of in-database monitoring and reporting More data types supported ...
CA ERwin Data Model Validator Implementation guide
... This documentation and any related computer software help programs (hereinafter referred to as the “Documentation”) is for the end user’s informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, m ...
... This documentation and any related computer software help programs (hereinafter referred to as the “Documentation”) is for the end user’s informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, m ...
KorthDB6_ch25
... “current” time), temporal databases model the states of the real world across time. Facts in temporal relations have associated times when they are valid, ...
... “current” time), temporal databases model the states of the real world across time. Facts in temporal relations have associated times when they are valid, ...
Chapter 13 - Emunix Documentation on the Web
... Because dataset data are disconnected from regular database, only optimistic locking can be used when updating the regular database with the dataset In the case of conflict, either the dataset must be reprocessed or the data change must be forced onto the database, causing the lost update proble ...
... Because dataset data are disconnected from regular database, only optimistic locking can be used when updating the regular database with the dataset In the case of conflict, either the dataset must be reprocessed or the data change must be forced onto the database, causing the lost update proble ...
Distributed Databases
... share no physical component Database systems that run on each site are independent of each ...
... share no physical component Database systems that run on each site are independent of each ...
Elmasri/Navathe, Fundamentals of Database Systems, Fourth
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
... Components of SQL/CLI Environment record: keeps track of database connections Connection record: keep tracks of info needed for a particular connection Statement record: keeps track of info needed for one SQL statement Description record: keeps track of tuples Elmasri/Navathe, Fundamentals of D ...
3.1.1 The Structure of JDBC
... Without JDBC, only disparate, proprietary database access solutions exist. These proprietary solutions force the developer to build a layer of abstraction on top of them in order to create database-independent code. Only after that abstraction layer is complete can the developer actually write the a ...
... Without JDBC, only disparate, proprietary database access solutions exist. These proprietary solutions force the developer to build a layer of abstraction on top of them in order to create database-independent code. Only after that abstraction layer is complete can the developer actually write the a ...
Slide 5-9
... Used to add an attribute to one of the base relations The new attribute will have NULLs in all the tuples of the relation right after the command is executed; hence, the NOT NULL constraint is not allowed for such an attribute Example: ALTER TABLE EMPLOYEE ADD JOB VARCHAR(12); The database users mus ...
... Used to add an attribute to one of the base relations The new attribute will have NULLs in all the tuples of the relation right after the command is executed; hence, the NOT NULL constraint is not allowed for such an attribute Example: ALTER TABLE EMPLOYEE ADD JOB VARCHAR(12); The database users mus ...
7. Inconsistency Handling What If the database is inconsistent
... Inconsistencies can be detected, and data can be changed to reach a physical consistent state This kind of data cleaning may be difficult, impossible, nondeterministic, undesirable, unmaintainable, etc. We may have to live with inconsistent data ... The database (the model) is departing from the outsi ...
... Inconsistencies can be detected, and data can be changed to reach a physical consistent state This kind of data cleaning may be difficult, impossible, nondeterministic, undesirable, unmaintainable, etc. We may have to live with inconsistent data ... The database (the model) is departing from the outsi ...
Document
... A Hypothetical Integrity Language (cont.) • When a CREATE INTEGRITY RULE statement is executed: (1) the system check if the current database state satisfied the specified constraint, YES => accept the rule NO => reject the rule (2) the accepted rule is saved in system catalog, (3) DBMS monitor all ...
... A Hypothetical Integrity Language (cont.) • When a CREATE INTEGRITY RULE statement is executed: (1) the system check if the current database state satisfied the specified constraint, YES => accept the rule NO => reject the rule (2) the accepted rule is saved in system catalog, (3) DBMS monitor all ...
Form one
... set of values in a table. For example, a mailing list table might include fields for first name, last name, address, city, state, zip code, and telephone number. • Record: a record in a row in a table and is a set of values defined by fields. In a mailing list table, each record would contain the da ...
... set of values in a table. For example, a mailing list table might include fields for first name, last name, address, city, state, zip code, and telephone number. • Record: a record in a row in a table and is a set of values defined by fields. In a mailing list table, each record would contain the da ...
designing database(updated)
... Must understand the meaning of the data and be prepared to resolve any problems that arise in the process. Synonyms: two different names used for the same attribute. When merging, get agreement from users on a single, standard name. Homonyms: a single attribute name that is used for two or more di ...
... Must understand the meaning of the data and be prepared to resolve any problems that arise in the process. Synonyms: two different names used for the same attribute. When merging, get agreement from users on a single, standard name. Homonyms: a single attribute name that is used for two or more di ...
PowerPoint Chapter 10
... Evaluating Transaction Results • Not all transactions update database • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints ...
... Evaluating Transaction Results • Not all transactions update database • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints ...