3-Tier Architecture
... – Input/output was text-based, GUI, and/or with files – Ran locally—that is, they had to be downloaded to the machine on which you (or your T.A.) ran them – The data had to be on the same machine as your program – Were not able to be run simultaneously by more than one person. – Had no interaction w ...
... – Input/output was text-based, GUI, and/or with files – Ran locally—that is, they had to be downloaded to the machine on which you (or your T.A.) ran them – The data had to be on the same machine as your program – Were not able to be run simultaneously by more than one person. – Had no interaction w ...
Advanced Databases Introduction
... some courses from other universities that look interesting to me. Perhaps the lecturers could take a look at those. − When (re-)constructing the course last year other universities’ ADB courses were surveyed. Many of the interesting topics are already handled in other courses (Data Mining, Informati ...
... some courses from other universities that look interesting to me. Perhaps the lecturers could take a look at those. − When (re-)constructing the course last year other universities’ ADB courses were surveyed. Many of the interesting topics are already handled in other courses (Data Mining, Informati ...
Advanced Databases Introduction
... some courses from other universities that look interesting to me. Perhaps the lecturers could take a look at those. − When (re-)constructing the course last year other universities’ ADB courses were surveyed. Many of the interesting topics are already handled in other courses (Data Mining, Informati ...
... some courses from other universities that look interesting to me. Perhaps the lecturers could take a look at those. − When (re-)constructing the course last year other universities’ ADB courses were surveyed. Many of the interesting topics are already handled in other courses (Data Mining, Informati ...
Supply Chain Enterprise Resources Planning and Business
... Copyright 2001 John Wiley & Sons, Incorporated. All rights reserved. Reproduction or translation of this work beyond that permitted in Section 117 of the 1976 United States Copyright Act without the express written permission of the copyright owner in unlawful. Request for further information shou ...
... Copyright 2001 John Wiley & Sons, Incorporated. All rights reserved. Reproduction or translation of this work beyond that permitted in Section 117 of the 1976 United States Copyright Act without the express written permission of the copyright owner in unlawful. Request for further information shou ...
Entities and Attributes
... value does not uniquely identify a row, but two values do, where we'd combine two column values to create a unique Primary Key. It sounds a little weird, so let me give you an example. Let's imagine I've got a publishing company and part of what I do is deal with Yearbooks for high schools. So, I ha ...
... value does not uniquely identify a row, but two values do, where we'd combine two column values to create a unique Primary Key. It sounds a little weird, so let me give you an example. Let's imagine I've got a publishing company and part of what I do is deal with Yearbooks for high schools. So, I ha ...
LECTURE_ONE_Introduction_to_databases
... Avoid making the same mistakes in databases Easily convert a file-based system to a database system ...
... Avoid making the same mistakes in databases Easily convert a file-based system to a database system ...
ENCh01 - Department of Computer Engineering
... Types of Databases and Database Applications Numeric and Textual Databases Multimedia Databases Geographic Information Systems (GIS) Data Warehouses Real-time and Active Databases A number of these databases and applications are described later in the book (see Chapters 24,28,29) Elmasri and N ...
... Types of Databases and Database Applications Numeric and Textual Databases Multimedia Databases Geographic Information Systems (GIS) Data Warehouses Real-time and Active Databases A number of these databases and applications are described later in the book (see Chapters 24,28,29) Elmasri and N ...
Chapter 3 Slide 4 - McGraw Hill Higher Education
... The word relation here is in reference to the collection of the data within one specific table. ...
... The word relation here is in reference to the collection of the data within one specific table. ...
Student Outline
... 5 Use MS Access database objects, Queries forms, reports and Macros to resolve database performance issues Assessment Guidelines Students must pass each assessment task as outlined to obtain a pass in this a Unit of Study If all assessment tasks are not passed, a final grade of U [ungraded fail] wil ...
... 5 Use MS Access database objects, Queries forms, reports and Macros to resolve database performance issues Assessment Guidelines Students must pass each assessment task as outlined to obtain a pass in this a Unit of Study If all assessment tasks are not passed, a final grade of U [ungraded fail] wil ...
Introduction to Databases
... Database Design: Basic Steps • Step 1: Determine the entities involved and create a separate table for each type of entity (thing, concept, event, theme) and name it. • Step 2: Determine the Primary Key for each table. • Step 3: Determine the properties for each entity (the non-key attributes). • S ...
... Database Design: Basic Steps • Step 1: Determine the entities involved and create a separate table for each type of entity (thing, concept, event, theme) and name it. • Step 2: Determine the Primary Key for each table. • Step 3: Determine the properties for each entity (the non-key attributes). • S ...
Keywords: Database, Deadlock, Distributed
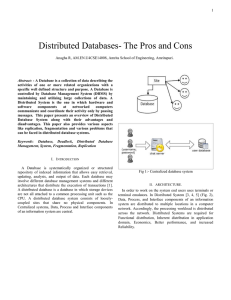
... In order to work on the system end users uses terminals or terminal emulators. In Distributed System [3, 4, 5] (Fig. 2), Data, Process, and Interface components of an information system are distributed to multiple locations in a computer network. Accordingly, the processing workload is distributed a ...
... In order to work on the system end users uses terminals or terminal emulators. In Distributed System [3, 4, 5] (Fig. 2), Data, Process, and Interface components of an information system are distributed to multiple locations in a computer network. Accordingly, the processing workload is distributed a ...
slides - Jim Paterson
... A well-designed database helps to make sure that the data stored is accurate and consistent and can be retrieved easily What do we mean by inconsistencies? It would, for example, be inconsistent to store a booking without storing the details of the customer making the booking With careful design, we ...
... A well-designed database helps to make sure that the data stored is accurate and consistent and can be retrieved easily What do we mean by inconsistencies? It would, for example, be inconsistent to store a booking without storing the details of the customer making the booking With careful design, we ...
Slide 1 - Pass4Sure
... A. Add Lisa Conrad to the Agent Proxy role in the ACL of the database. B. Include Lisa Conrad in the ACL of any database the agent will access. C. Include Lisa Conrad in the Agent Access field in the server document on the server in which the agent will run D. Include Lisa Conrad in the Run restrict ...
... A. Add Lisa Conrad to the Agent Proxy role in the ACL of the database. B. Include Lisa Conrad in the ACL of any database the agent will access. C. Include Lisa Conrad in the Agent Access field in the server document on the server in which the agent will run D. Include Lisa Conrad in the Run restrict ...
What Is a Shape Object?
... as specialized fields in tables. Oracle uses Oracle Spatial, PostgreSQL uses PostGIS, MySQL and DB2 use Spatial Extensions, SQL Server 2008 provides spatial support, and so on. There is enough similarity in how these structures store spatial components and their georeference that the geodata layers ...
... as specialized fields in tables. Oracle uses Oracle Spatial, PostgreSQL uses PostGIS, MySQL and DB2 use Spatial Extensions, SQL Server 2008 provides spatial support, and so on. There is enough similarity in how these structures store spatial components and their georeference that the geodata layers ...
TYPES OF DBMS 5.1 INTRODUCTION: There are four main types of
... Integrated Data Store (IDS) IDMS (Integrated Database Management System) RDM Embedded RDM Server TurboIMAGE Univac DMS-1100 ...
... Integrated Data Store (IDS) IDMS (Integrated Database Management System) RDM Embedded RDM Server TurboIMAGE Univac DMS-1100 ...
database_design
... Database Design: Basic Steps • Step 1: Determine the entities involved and create a separate table for each type of entity (thing, concept, event, theme) and name it. • Step 2: Determine the Primary Key for each table. • Step 3: Determine the properties for each entity (the non-key attributes). • S ...
... Database Design: Basic Steps • Step 1: Determine the entities involved and create a separate table for each type of entity (thing, concept, event, theme) and name it. • Step 2: Determine the Primary Key for each table. • Step 3: Determine the properties for each entity (the non-key attributes). • S ...
Database Fundamentals
... Figure 1-12 Three-schema architecture Different people have different views of the database…these are the external schema ...
... Figure 1-12 Three-schema architecture Different people have different views of the database…these are the external schema ...
read more (click here) - Galera Cluster for MySQL
... their Oracle database as their business grew. They wanted a real-‐‑time replica of their production database in their facility in case of disaster, but they werenʼ’t able to have this under the existing MySQL database license terms they had with Oracle. The inflexible approach to MySQL database lice ...
... their Oracle database as their business grew. They wanted a real-‐‑time replica of their production database in their facility in case of disaster, but they werenʼ’t able to have this under the existing MySQL database license terms they had with Oracle. The inflexible approach to MySQL database lice ...
Chapter 1
... If the database and applications are simple, well defined, and not expected to change. If there are stringent real-time requirements that may not be met because of DBMS overhead. If access to data by multiple users is not required. ...
... If the database and applications are simple, well defined, and not expected to change. If there are stringent real-time requirements that may not be met because of DBMS overhead. If access to data by multiple users is not required. ...
Knowing Just Enough about Relational Databases
... Understanding basic database terminology A database consists of tables and columns, as described in the preceding section. There are some other terms you need to know in order to understand how databases work. A database is built in two stages. First you create a logical data model to lay out the de ...
... Understanding basic database terminology A database consists of tables and columns, as described in the preceding section. There are some other terms you need to know in order to understand how databases work. A database is built in two stages. First you create a logical data model to lay out the de ...
File - BS-IT UOS
... Analytic databases (a.k.a. OLAP- On Line Analytical Processing) are primarily static, read-only databases which store archived, historical data used for analysis. For example, a company might store sales records over the last ten years in an analytic database and use that database to analyze marketi ...
... Analytic databases (a.k.a. OLAP- On Line Analytical Processing) are primarily static, read-only databases which store archived, historical data used for analysis. For example, a company might store sales records over the last ten years in an analytic database and use that database to analyze marketi ...
Slides
... – Track customers and their artist interests – Record gallery's purchases – Record customers' art purchases – List the artists and works that have appeared in the gallery – Report how fast an artist's works have sold and at what margin – Show current inventory in a Web page DAVID M. KROENKE’S DATABA ...
... – Track customers and their artist interests – Record gallery's purchases – Record customers' art purchases – List the artists and works that have appeared in the gallery – Report how fast an artist's works have sold and at what margin – Show current inventory in a Web page DAVID M. KROENKE’S DATABA ...
Materialy/32/Lectures ClientServer
... Information systems security. C. TDBSSI (Information Systems Security Trend Chart) An ISS trend chart is a management tool used at various levels of decision-making, management, and operations to provide an analytical overview of the security situation, from both a technical and functional viewpoin ...
... Information systems security. C. TDBSSI (Information Systems Security Trend Chart) An ISS trend chart is a management tool used at various levels of decision-making, management, and operations to provide an analytical overview of the security situation, from both a technical and functional viewpoin ...
CS chit-chat - ERI people pages
... Query translation • Gazetteer is an instance of a much more general problem • To wit: – how to describe the automatic translation of dynamic queries written in an abstract query language to SQL – in an easy, powerful, flexible way – making as few assumptions as possible about the underlying schema ...
... Query translation • Gazetteer is an instance of a much more general problem • To wit: – how to describe the automatic translation of dynamic queries written in an abstract query language to SQL – in an easy, powerful, flexible way – making as few assumptions as possible about the underlying schema ...