Distributed Programming
... ▪ Is there an IDL for RMI? › No because RMI uses Java code on both the client and server, only requiring serialization of Java objects ...
... ▪ Is there an IDL for RMI? › No because RMI uses Java code on both the client and server, only requiring serialization of Java objects ...
Kennesaw State University: AP Computer Science A
... College Board’s Advanced Placement Computer Science A exam. Every module in the course is designed to be completed in two weeks. Every module has an assignment dealing with the GridWorld case study, a hands-on lab, and a programming assignment. The computer language that will be used is Java, which ...
... College Board’s Advanced Placement Computer Science A exam. Every module in the course is designed to be completed in two weeks. Every module has an assignment dealing with the GridWorld case study, a hands-on lab, and a programming assignment. The computer language that will be used is Java, which ...
Separate Classes for Event Handling
... Separate Classes for Event Handling The above method for event handling works well if there are only a few possible events that can occur. However, consider an application that might have dozens of buttons, or other components which might cause events (such as checkboxes, drop-down lists, etc.). In ...
... Separate Classes for Event Handling The above method for event handling works well if there are only a few possible events that can occur. However, consider an application that might have dozens of buttons, or other components which might cause events (such as checkboxes, drop-down lists, etc.). In ...
Enhancing Student Learning of Programming via Gaming Technology
... 3. Inheritance: defines relationships among classes. For example, in Java, the methods from “java.lang.Object” are inherited and implemented by its subclasses, namely every class in the Java API libraries. In addition, each class adds its own set of fields and methods to what it inherits from its su ...
... 3. Inheritance: defines relationships among classes. For example, in Java, the methods from “java.lang.Object” are inherited and implemented by its subclasses, namely every class in the Java API libraries. In addition, each class adds its own set of fields and methods to what it inherits from its su ...
04-support
... patterns are very well supported Understanding the low-level details behind these structures is important for effectively using them Describing these structures as patterns provides guidance for implementing them from scratch Combine patterns in different ways to meet the needs of a particular probl ...
... patterns are very well supported Understanding the low-level details behind these structures is important for effectively using them Describing these structures as patterns provides guidance for implementing them from scratch Combine patterns in different ways to meet the needs of a particular probl ...
Client-Side Web Programming (Part 1) Robert M. Dondero, Ph.D.
... Ways to reference an object within the DOM ...
... Ways to reference an object within the DOM ...
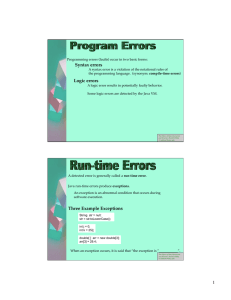
1 Syntax errors Logic errors Three Example Exceptions
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
CSC 8560 Computer Networks Project
... GIOP-derived protocols such as IIOP. These protocols, in turn, rest on top of TCP/IP, DCE, or whatever underlying transport protocol the network uses. CORBA applications aren't limited to using only one of these protocols; an application architecture can be designed to use a bridge that would interc ...
... GIOP-derived protocols such as IIOP. These protocols, in turn, rest on top of TCP/IP, DCE, or whatever underlying transport protocol the network uses. CORBA applications aren't limited to using only one of these protocols; an application architecture can be designed to use a bridge that would interc ...
exceptions
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
exceptions
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
... System.out.println( ”udder: before exception" ); throw( new ArithmeticException() ); System.out.println( ”udder: after exception" ); ...
PowerPoint
... • Compiling miniTAJS takes 35 seconds – 4500 lines of code – 113 classes + 40 objects = 580 .class files ...
... • Compiling miniTAJS takes 35 seconds – 4500 lines of code – 113 classes + 40 objects = 580 .class files ...
CITS2210 Object-Oriented Programming Topic 16 C++: Templates
... Summary: This topic shows C++ templates in detail, and compares them to Java generics. It also considers the much used C++ standard template library, which includes templates for containers, similar to the Java collections framework. ...
... Summary: This topic shows C++ templates in detail, and compares them to Java generics. It also considers the much used C++ standard template library, which includes templates for containers, similar to the Java collections framework. ...
CS 108 Teaching Staff CS - 108
... String and Rectangle objects using the operator new. The statement below creates a new Rectangle object and passes it to the println() method which is a method of the pre-defined PrintStream class. System.out.println(new Rectangle(10,5,20,30)) This method prints the details of the Rectangle object t ...
... String and Rectangle objects using the operator new. The statement below creates a new Rectangle object and passes it to the println() method which is a method of the pre-defined PrintStream class. System.out.println(new Rectangle(10,5,20,30)) This method prints the details of the Rectangle object t ...
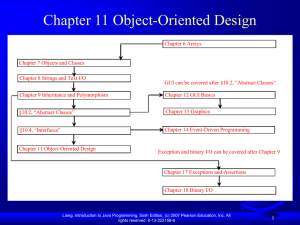
Chapter 9: Object-Oriented Software Development
... Each class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The ...
... Each class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The ...
lecture01a_03_04
... – Data describes what the object is – Methods describes what the object can do ...
... – Data describes what the object is – Methods describes what the object can do ...
Chapter 19 Java Data Structures
... is a collection of data stored sequentially. It supports insertion and deletion anywhere in the list. A stack can be perceived as a special type of the list where insertions and deletions take place only at the one end, referred to as the top of a stack. A queue represents a waiting list, where inse ...
... is a collection of data stored sequentially. It supports insertion and deletion anywhere in the list. A stack can be perceived as a special type of the list where insertions and deletions take place only at the one end, referred to as the top of a stack. A queue represents a waiting list, where inse ...
Programming in Java - UCL Computer Science
... classes classes & & arrays arrays Instances Instances of of derived derived types types handled handled by by reference reference •• primitive primitive types types handled handled by by value. value. ...
... classes classes & & arrays arrays Instances Instances of of derived derived types types handled handled by by reference reference •• primitive primitive types types handled handled by by value. value. ...
Describe three differences between Object Oriented and Traditional
... Object-oriented programming may be seen as a collection of cooperating objects, as opposed to a traditional view in which a program may be seen as a group of tasks to compute ("subroutines"). In OOP, each object is capable of receiving messages, processing data, and sending messages to other objects ...
... Object-oriented programming may be seen as a collection of cooperating objects, as opposed to a traditional view in which a program may be seen as a group of tasks to compute ("subroutines"). In OOP, each object is capable of receiving messages, processing data, and sending messages to other objects ...
BIT 115: Introduction To Programming - Canvas
... you can start with a base (or parent) class that contains shared characteristics among several classes. That base class can then be extended by other classes (children) that are similar but are meant for slightly different purposes. Any changes in the parent class will automatically cascade to its c ...
... you can start with a base (or parent) class that contains shared characteristics among several classes. That base class can then be extended by other classes (children) that are similar but are meant for slightly different purposes. Any changes in the parent class will automatically cascade to its c ...
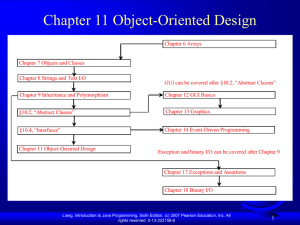
Chapter 9: Object-Oriented Software Development
... Each class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The ...
... Each class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The ...
[PDF]
... systems has encouraged the use of automated software tools [10, 11, 12, 13] that facilitate the development process from analysis through coding. There are two major approaches used for object-oriented model based code generation, namely structural and behavioral. The structural approach is based on ...
... systems has encouraged the use of automated software tools [10, 11, 12, 13] that facilitate the development process from analysis through coding. There are two major approaches used for object-oriented model based code generation, namely structural and behavioral. The structural approach is based on ...
Programming Language Pragmatics
... appearence determined the host window system • AWT components are tied directly to the local platform's GUI capabilities • unfortunately, the behaviour of native components differs in annoying respects, even if only minimum common capabilities are used – "write once, test everywhere" • AWT component ...
... appearence determined the host window system • AWT components are tied directly to the local platform's GUI capabilities • unfortunately, the behaviour of native components differs in annoying respects, even if only minimum common capabilities are used – "write once, test everywhere" • AWT component ...
Chapter 10 slides
... class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The contr ...
... class can present two contracts – one for the users of the class and one for the extenders of the class. Make the fields private and accessor methods public if they are intended for the users of the class. Make the fields or method protected if they are intended for extenders of the class. The contr ...
PDF - 4up
... a collection object. To define a data structure is essentially to declare a class. The class for a data structure should use data fields to store data and provide methods to support operations such as insertion and deletion. To create a data structure is therefore to create an instance from the clas ...
... a collection object. To define a data structure is essentially to declare a class. The class for a data structure should use data fields to store data and provide methods to support operations such as insertion and deletion. To create a data structure is therefore to create an instance from the clas ...
















![[PDF]](http://s1.studyres.com/store/data/008804302_1-ea1badad5407649bdcfcefcf2161ea31-300x300.png)