A Second Edition: Verification of a Cryptographic Primitive: SHA-256 ANDREW W. APPEL
... In this paper I present a first step: a formal verification of the functional correctness of the SHA-256 implementation from the OpenSSL open-source distribution. Formal verification is not necessarily a substitute for many-eyes assurance. For example, in this case, I present only the assurance of f ...
... In this paper I present a first step: a formal verification of the functional correctness of the SHA-256 implementation from the OpenSSL open-source distribution. Formal verification is not necessarily a substitute for many-eyes assurance. For example, in this case, I present only the assurance of f ...
Short Introduction to the Lambda
... In functional programming languages functions are treated as any other object. Hence they can be given as argument to other functions or be the result of a function. Function that can have functions as argument or result are called higher-order functions. This enables us to introduce the notion of c ...
... In functional programming languages functions are treated as any other object. Hence they can be given as argument to other functions or be the result of a function. Function that can have functions as argument or result are called higher-order functions. This enables us to introduce the notion of c ...
Apache Hadoop Community Spotlight: Apache Pig
... built to work in the Hadoop world, where data may or may not be structured or have known schemas. The Pig platform is built to provide a pipeline of operations. It is often used to do extract, transform, load (ETL) operations by pulling data from various sources and then doing the transformations in ...
... built to work in the Hadoop world, where data may or may not be structured or have known schemas. The Pig platform is built to provide a pipeline of operations. It is often used to do extract, transform, load (ETL) operations by pulling data from various sources and then doing the transformations in ...
Text files
... new FileInputStream("numbers.dat"); DataInputStream inputStream = new DataInputSteam(middleman); Java: an Introduction to Computer Science & Programming - Walter Savitch ...
... new FileInputStream("numbers.dat"); DataInputStream inputStream = new DataInputSteam(middleman); Java: an Introduction to Computer Science & Programming - Walter Savitch ...
Programming with Java
... The Swing components in JFC contain a list as well as a combo box. You will find Swing lists(JList and JComboBox) have significant advantages over the AWT lists (List and Choice). ...
... The Swing components in JFC contain a list as well as a combo box. You will find Swing lists(JList and JComboBox) have significant advantages over the AWT lists (List and Choice). ...
CategoriesAndAlgebras
... A F-CoAlgebra, g, is Final if for any other FCoAlgebra, f, there is a unique F-CoAlgebra homomorphism, h, from f to g. We can show its existence be building a function that computes it from the CoAlgebra, f. ana :: Functor f => (CoAlgebra f seed) -> seed -> (Final f) ana (CoAlgebra phi) seed = Final ...
... A F-CoAlgebra, g, is Final if for any other FCoAlgebra, f, there is a unique F-CoAlgebra homomorphism, h, from f to g. We can show its existence be building a function that computes it from the CoAlgebra, f. ana :: Functor f => (CoAlgebra f seed) -> seed -> (Final f) ana (CoAlgebra phi) seed = Final ...
Lambda Calculus and Functional Programming
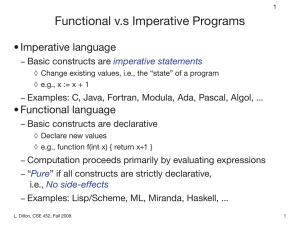
... If there is no data dependency between two pure expressions, then their order can be reversed, or they can be performed in parallel and they cannot interfere with one another (in other terms, the evaluation of any pure expression is thread-safe). If the entire language does not allow side-effects, ...
... If there is no data dependency between two pure expressions, then their order can be reversed, or they can be performed in parallel and they cannot interfere with one another (in other terms, the evaluation of any pure expression is thread-safe). If the entire language does not allow side-effects, ...
Praktikum Bahasa Pemrograman (Functional Programming)
... • However, any statement, not just (define …) statements, can be executed from the Definitions window ...
... • However, any statement, not just (define …) statements, can be executed from the Definitions window ...
PDF - 4up
... this chapter are lists, stacks, queues, and binary trees. A list is a collection of data stored sequentially. It supports insertion and deletion anywhere in the list. A stack can be perceived as a special type of the list where insertions and deletions take place only at the one end, referred to as ...
... this chapter are lists, stacks, queues, and binary trees. A list is a collection of data stored sequentially. It supports insertion and deletion anywhere in the list. A stack can be perceived as a special type of the list where insertions and deletions take place only at the one end, referred to as ...
A Simple and Efficient Compiler for a Minimal
... Mini-Scheme interpreter in Scheme, Mini-ML interpreter in OCaml, Othello/Reversi competition in OCaml, etc. Parsing, intermediate representations, register allocation, garbage collection, ... ...
... Mini-Scheme interpreter in Scheme, Mini-ML interpreter in OCaml, Othello/Reversi competition in OCaml, etc. Parsing, intermediate representations, register allocation, garbage collection, ... ...
GWT - Meetup
... • If you plan on mixing GWT with some HTML code, use RootPanel.get(stringID) otherwise your whole page will be a GWT App • An good example of an embedded GWT Module could be Google Maps ...
... • If you plan on mixing GWT with some HTML code, use RootPanel.get(stringID) otherwise your whole page will be a GWT App • An good example of an embedded GWT Module could be Google Maps ...
Temporal Logic with “Until”, Functional Reactive Programming with
... time what values inhabit a certain FRP type. If objects A and B model FRP types τ1 and τ2 , a morphism f : A → B denotes an operation that turns any value that inhabits τ1 at some time into a value that inhabits τ2 at the same time. Finite products, finite sums, and functions spaces in FRP are model ...
... time what values inhabit a certain FRP type. If objects A and B model FRP types τ1 and τ2 , a morphism f : A → B denotes an operation that turns any value that inhabits τ1 at some time into a value that inhabits τ2 at the same time. Finite products, finite sums, and functions spaces in FRP are model ...
On Feature Orientation and Functional Programming
... Specifically, we found module-level crosscutting to be the most frequent form of crosscutting. The reason is that modules are coarse-grained building blocks and that they impose an hierarchical block structure on the program that does not align with crosscutting concerns. Algebraic Data Types. A pro ...
... Specifically, we found module-level crosscutting to be the most frequent form of crosscutting. The reason is that modules are coarse-grained building blocks and that they impose an hierarchical block structure on the program that does not align with crosscutting concerns. Algebraic Data Types. A pro ...
A Survey on SDN Programming Languages: Toward a Taxonomy
... configurable black boxes until the emergence of software-defined networking (SDN). SDN enables the networks to be programmed according to the user requirements; furthermore, it allows the network to be easily modified to suit transient demands. However, how do we program the network? SDN-compliant s ...
... configurable black boxes until the emergence of software-defined networking (SDN). SDN enables the networks to be programmed according to the user requirements; furthermore, it allows the network to be easily modified to suit transient demands. However, how do we program the network? SDN-compliant s ...
C Sharp (programming language)
C# (pronounced as see sharp) is a multi-paradigm programming language encompassing strong typing, imperative, declarative, functional, generic, object-oriented (class-based), and component-oriented programming disciplines. It was developed by Microsoft within its .NET initiative and later approved as a standard by Ecma (ECMA-334) and ISO (ISO/IEC 23270:2006). C# is one of the programming languages designed for the Common Language Infrastructure.C# is intended to be a simple, modern, general-purpose, object-oriented programming language. Its development team is led by Anders Hejlsberg. The most recent version is C# 6.0, which was released on July 20, 2015.