using System.Collections.Generic
... So using the notation with colons is possible to derive a class from another. In C # inheritance is single and not multiple such as C + + or Python. In order to circumvent this limitation you can use, as we shall see later, the interfaces. The three key words of object-oriented programming are: 1. I ...
... So using the notation with colons is possible to derive a class from another. In C # inheritance is single and not multiple such as C + + or Python. In order to circumvent this limitation you can use, as we shall see later, the interfaces. The three key words of object-oriented programming are: 1. I ...
COS 217: Introduction to Programming Systems Goals for Today’s Class
... – Your own PC, secure shell to “hats.princeton.edu” (Linux) – Why: common environment, and access to lab TAs ...
... – Your own PC, secure shell to “hats.princeton.edu” (Linux) – Why: common environment, and access to lab TAs ...
Computer Science Homework 1
... It's just about 5MB. After downloading that software, install it by double-clicking on the downloaded program and follow (again) the instruction. This time it should finish quickly and place a link to the BlueJ IDE on your desktop. Now you should have the necessary software to start developing your ...
... It's just about 5MB. After downloading that software, install it by double-clicking on the downloaded program and follow (again) the instruction. This time it should finish quickly and place a link to the BlueJ IDE on your desktop. Now you should have the necessary software to start developing your ...
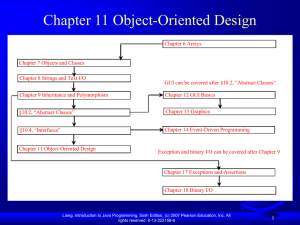
Chapter 9: Object-Oriented Software Development
... Classes, cont. For example, since an orange is a fruit, their relationship should be modeled using class inheritance. A weak is-anextension-of relationship, also known as an is-kind-of relationship, indicates that an object possesses a certain property. A weak is-an-extension-of relationship can be ...
... Classes, cont. For example, since an orange is a fruit, their relationship should be modeled using class inheritance. A weak is-anextension-of relationship, also known as an is-kind-of relationship, indicates that an object possesses a certain property. A weak is-an-extension-of relationship can be ...
A Malay Language-based Visual Programming Language for
... size limits the number of objects that can be displayed on the screen. Figure 12(a) shows an example of program in MaVi Environment created by user, while Figure 12(b) shows the similar program but after the user uses the ...
... size limits the number of objects that can be displayed on the screen. Figure 12(a) shows an example of program in MaVi Environment created by user, while Figure 12(b) shows the similar program but after the user uses the ...
CSE 142 Python Slides - Building Java Programs
... their behavior as interactions between objects. – abstraction: Separation between concepts and details. Objects provide abstraction in programming. ...
... their behavior as interactions between objects. – abstraction: Separation between concepts and details. Objects provide abstraction in programming. ...
Assignment No
... What is event driven programming? All GUIs (Graphical User Interfaces) and graphical games, like Counter-Strike, Halo, are written in as event driven programs. Event-driven programs break from the traditional programming structure. In traditional programming languages, the application, rather than a ...
... What is event driven programming? All GUIs (Graphical User Interfaces) and graphical games, like Counter-Strike, Halo, are written in as event driven programs. Event-driven programs break from the traditional programming structure. In traditional programming languages, the application, rather than a ...
Fundamentals of JAVA Chapter 1 PowerPoint Background
... Instance variables (data resources) Methods (rules of behavior) ...
... Instance variables (data resources) Methods (rules of behavior) ...
Functional Programming Languages and Dataflow Principles
... Instruction Store: holds coding of the dataflow graph (equivalent to object code/machine code) Processor Bank: a number of processors – all holding zero state from one execution to next! Token Queue: buffering (and the place to insert any input data) ...
... Instruction Store: holds coding of the dataflow graph (equivalent to object code/machine code) Processor Bank: a number of processors – all holding zero state from one execution to next! Token Queue: buffering (and the place to insert any input data) ...
What is a Concurrent Program?
... The emphasis on principles and concepts provides a thorough understanding of both the problems and the solution techniques. Modelling provides insight into concurrent behaviour and aids reasoning about particular designs. After the course the student should understand the problems that are specific ...
... The emphasis on principles and concepts provides a thorough understanding of both the problems and the solution techniques. Modelling provides insight into concurrent behaviour and aids reasoning about particular designs. After the course the student should understand the problems that are specific ...
Kennesaw State University: AP Computer Science A
... boolean operators and variables. While Loops – In this module students will learn how to write programs using while loops to repeatedly execute one or more statements. Be able to program loops ...
... boolean operators and variables. While Loops – In this module students will learn how to write programs using while loops to repeatedly execute one or more statements. Be able to program loops ...
Functional Programming: Introduction Introduction (Cont.)
... – Semantics (meaning) based on λ-calculus. • The λ-calculus is a theoretical model of computation – Functions operate on lists or atomic symbols. • Programs consist of "S-expressions" • Five basic functions: cons, car, cdr, equal, atom ...
... – Semantics (meaning) based on λ-calculus. • The λ-calculus is a theoretical model of computation – Functions operate on lists or atomic symbols. • Programs consist of "S-expressions" • Five basic functions: cons, car, cdr, equal, atom ...
Parts vs. the whole in the procedural logic hierarchy.
... method. (See below.) Some programming languages allow a separately compiled/assembled module to be programmed in such as way that either the module can be invoked from a program’s main or other modules; or it can be started and stopped as an independent program or main module. --------->named modul ...
... method. (See below.) Some programming languages allow a separately compiled/assembled module to be programmed in such as way that either the module can be invoked from a program’s main or other modules; or it can be started and stopped as an independent program or main module. --------->named modul ...
Introduction to Software Engineering
... 3. The private modifier prevents access from outside the enclosing class. 4. The most restrictive modification applies ...
... 3. The private modifier prevents access from outside the enclosing class. 4. The most restrictive modification applies ...
ppt
... High-Level Languages • look more like human languages • programs called compilers convert high-level code into machine language • structured & object-oriented – structured: Pascal, C – structured & object-oriented: Java, C++ ...
... High-Level Languages • look more like human languages • programs called compilers convert high-level code into machine language • structured & object-oriented – structured: Pascal, C – structured & object-oriented: Java, C++ ...
View File - UET Taxila
... does not follow these rules has one or more syntax errors. Software Development Kit (SDK) that contains the following: Libraries: also known as Application Programming Interface (API), these files are previously written classes and methods that contain some common functionality. Compiler: the progra ...
... does not follow these rules has one or more syntax errors. Software Development Kit (SDK) that contains the following: Libraries: also known as Application Programming Interface (API), these files are previously written classes and methods that contain some common functionality. Compiler: the progra ...
Security in Java: Real or Decaf? - University of Virginia, Department
... 1. Sees everything a program is about to do before it does it 2. Can instantly and completely stop program execution (or prevent action) 3. Has no other effect on the program or ...
... 1. Sees everything a program is about to do before it does it 2. Can instantly and completely stop program execution (or prevent action) 3. Has no other effect on the program or ...
Binary Search
... the position of a search key K in an ordered array A[0:n1] of distinct keys arranged in ascending order: A[0] < A[1] < … < A[n-1]. • The algorithm chooses the key in the middle of A[0:n1], which is located at A[Middle], where Middle=(0+(n-1))/2, and compares the search key K and A[Middle]. • If K==A ...
... the position of a search key K in an ordered array A[0:n1] of distinct keys arranged in ascending order: A[0] < A[1] < … < A[n-1]. • The algorithm chooses the key in the middle of A[0:n1], which is located at A[Middle], where Middle=(0+(n-1))/2, and compares the search key K and A[Middle]. • If K==A ...
Functional_Languages_Intro
... Functional Programming Concepts • So how do you get anything done in a functional ...
... Functional Programming Concepts • So how do you get anything done in a functional ...
9781285081953_PPT_ch14
... • When you create a class that descends from the JFrame class: – You can set the JFrame’s properties within your object’s constructor – Then, when the JFrame child object is created, it is automatically endowed with the features you specified ...
... • When you create a class that descends from the JFrame class: – You can set the JFrame’s properties within your object’s constructor – Then, when the JFrame child object is created, it is automatically endowed with the features you specified ...
1.6 SETS
... A predicate over a well-defined set can specify any subcollection within that set. (Warning: This “set-builder” method can lead to non-sets.) Example 1.6.6: {x ∈ Z : P (x)} where P (x) is TRUE if x is prime. Example 1.6.7: ...
... A predicate over a well-defined set can specify any subcollection within that set. (Warning: This “set-builder” method can lead to non-sets.) Example 1.6.6: {x ∈ Z : P (x)} where P (x) is TRUE if x is prime. Example 1.6.7: ...
COS 217: Introduction to Programming Systems Goals for Today’s Class
... – Your own PC, secure shell to “hats.princeton.edu” (Linux) – Why: common environment, and access to lab TAs ...
... – Your own PC, secure shell to “hats.princeton.edu” (Linux) – Why: common environment, and access to lab TAs ...