Isolating Operating System Components with Intel SGX
... the operating system as one compromised operating system component can easily compromise other components of the kernel without the need for further vulnerabilities. To enforce isolation of operating system components even in the event of a partially compromised kernel, trust needs to be rooted, for ...
... the operating system as one compromised operating system component can easily compromise other components of the kernel without the need for further vulnerabilities. To enforce isolation of operating system components even in the event of a partially compromised kernel, trust needs to be rooted, for ...
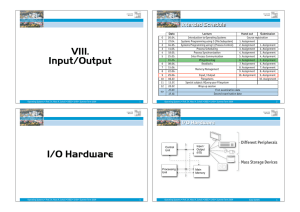
VIII. Input/Output
... To use a disk to hold files, the operating system still needs to record its ...
... To use a disk to hold files, the operating system still needs to record its ...
No Slide Title
... native environment but during development NT was changed to use the Win32 API, reflecting the popularity of Windows 3.0. ...
... native environment but during development NT was changed to use the Win32 API, reflecting the popularity of Windows 3.0. ...
ch22
... native environment but during development NT was changed to use the Win32 API, reflecting the popularity of Windows 3.0. ...
... native environment but during development NT was changed to use the Win32 API, reflecting the popularity of Windows 3.0. ...
Chapter 21 - Linux Operating System
... information to components of the user-mode system software The environment-variable mechanism provides a customization of the ...
... information to components of the user-mode system software The environment-variable mechanism provides a customization of the ...
Hands-On Ethical Hacking and Network Defense Second Edition
... – Some source code is available to the public • Code sharing is not common • Microsoft believed it would increase adoptions Hands-On Ethical Hacking and Network Defense, Second Edition ...
... – Some source code is available to the public • Code sharing is not common • Microsoft believed it would increase adoptions Hands-On Ethical Hacking and Network Defense, Second Edition ...
9781435486096_PPT_ch09
... – Some source code is available to the public • Code sharing is not common • Microsoft believed it would increase adoptions Hands-On Ethical Hacking and Network Defense, Second Edition ...
... – Some source code is available to the public • Code sharing is not common • Microsoft believed it would increase adoptions Hands-On Ethical Hacking and Network Defense, Second Edition ...
Operating Systems, 082
... file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, all from argv, and uses execvp() (or a similar system call) to run the grep executable On foreground execution, the shell would ...
... file_name into argv and their number to argc Next, the shell uses fork() to create a process (same user ID) Now, it takes the executable name grep and the arguments, all from argv, and uses execvp() (or a similar system call) to run the grep executable On foreground execution, the shell would ...
Abstract View of System Components
... • Allows many user level threads to be multiplexed to a smaller or equal number of kernel threads. • Allows the operating system to create a sufficient number of kernel threads. • Solaris 2 • Windows NT/2000 with the ThreadFiber ...
... • Allows many user level threads to be multiplexed to a smaller or equal number of kernel threads. • Allows the operating system to create a sufficient number of kernel threads. • Solaris 2 • Windows NT/2000 with the ThreadFiber ...
Project 1, Linux Kernel Hacking
... – Difference between original source tree and Part 2 kernel. ...
... – Difference between original source tree and Part 2 kernel. ...
Chapter 6: Process/thread Synchronization
... 2. "Progress - If no process is executing in its critical section and there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postponed indefinitely" 3. "Bounded Waiting - A bound must exist on the ...
... 2. "Progress - If no process is executing in its critical section and there exist some processes that wish to enter their critical section, then the selection of the processes that will enter the critical section next cannot be postponed indefinitely" 3. "Bounded Waiting - A bound must exist on the ...
Chapter 1
... Eg When character is finished being printed, interrupt CPU. Allows CPU to do something else while character is being printed Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0-13-6006639 ...
... Eg When character is finished being printed, interrupt CPU. Allows CPU to do something else while character is being printed Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0-13-6006639 ...
I/O Speculation for the Microsecond Era
... of microsecond-scale I/O devices, and attempt to quantify the performance gains that speculation has to offer. We then explore several techniques for speculation, which includes exploring existing software-based checkpointing techniques. We also propose new techniques which exploit the semantics of ...
... of microsecond-scale I/O devices, and attempt to quantify the performance gains that speculation has to offer. We then explore several techniques for speculation, which includes exploring existing software-based checkpointing techniques. We also propose new techniques which exploit the semantics of ...
Concurrency
... Binds the algorithm to Process name Sender explicitly names the received or receiver explicitly names the sender ...
... Binds the algorithm to Process name Sender explicitly names the received or receiver explicitly names the sender ...
Notes
... • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (direct hardware a ...
... • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (direct hardware a ...
ch4-v2
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
ppt
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space of the parent ...
ch21
... developed for other operating system. 2000 uses the Win32 subsystem as the main operating environment; Win32 is used to start all processes. It also provides all the keyboard, mouse and graphical display ...
... developed for other operating system. 2000 uses the Win32 subsystem as the main operating environment; Win32 is used to start all processes. It also provides all the keyboard, mouse and graphical display ...
Higher National Unit specification: general information Unit title
... reading, and opportunities for individual or group research should be provided. The most important overall emphasis should be on the relevance and currency of content in such a rapidly-evolving field. The following notes assume that the Unit will be delivered using a Microsoft operating system. Howe ...
... reading, and opportunities for individual or group research should be provided. The most important overall emphasis should be on the relevance and currency of content in such a rapidly-evolving field. The following notes assume that the Unit will be delivered using a Microsoft operating system. Howe ...
Windows 2000
... developed for other operating system. 2000 uses the Win32 subsystem as the main operating environment; Win32 is used to start all processes. It also provides all the keyboard, mouse and graphical display ...
... developed for other operating system. 2000 uses the Win32 subsystem as the main operating environment; Win32 is used to start all processes. It also provides all the keyboard, mouse and graphical display ...
Structures - IDA.LiU.se - Linköpings universitet
... § OS functions supporting the efficient operation of the system itself: • Resource allocation – When multiple users or multiple jobs are running concurrently, resources must be allocated to each of them > Types of resources: CPU time, main memory, file storage, I/O dev. • Accounting > keep track of ...
... § OS functions supporting the efficient operation of the system itself: • Resource allocation – When multiple users or multiple jobs are running concurrently, resources must be allocated to each of them > Types of resources: CPU time, main memory, file storage, I/O dev. • Accounting > keep track of ...
WOSI-CRK-Description
... scaleable to multiple academic levels and can be used by faculty staff in whole or in part for teaching OS courses in academic institutions. The basic modules provide materials to incorporate into a complete undergraduate level OS course of one semester in length. This covers the Windows operating s ...
... scaleable to multiple academic levels and can be used by faculty staff in whole or in part for teaching OS courses in academic institutions. The basic modules provide materials to incorporate into a complete undergraduate level OS course of one semester in length. This covers the Windows operating s ...
ppt
... that forms the basis of multithreaded computer systems To discuss the APIs for the Pthreads, Win32, and Java thread libraries To examine issues related to multithreaded programming ...
... that forms the basis of multithreaded computer systems To discuss the APIs for the Pthreads, Win32, and Java thread libraries To examine issues related to multithreaded programming ...
9 - PSNA College of Engineering and Technology
... minimum overhead. Usually, the sensor and monitoring instruments communicate with the rest of the system in interrupt mode. Device drivers are specifically tuned to service these inputs. In Section 8.2 we shall discuss the related design issues for micro-kernels and RTOS. Why not use Unix or Windows ...
... minimum overhead. Usually, the sensor and monitoring instruments communicate with the rest of the system in interrupt mode. Device drivers are specifically tuned to service these inputs. In Section 8.2 we shall discuss the related design issues for micro-kernels and RTOS. Why not use Unix or Windows ...