Overview and History
... an interpreter is a program that reads and executes each language statement in sequence Java programs are first compiled into a virtual machine language (Java byte code) then the byte code is executed by an interpreter (Java Virtual Machine) ...
... an interpreter is a program that reads and executes each language statement in sequence Java programs are first compiled into a virtual machine language (Java byte code) then the byte code is executed by an interpreter (Java Virtual Machine) ...
CM033 : ADVANCED PROGRAMMING MODELS
... containing useful links : – ~daveh/links – Notably, the GNU PROLOG home page. – Versions of GNU PROLOG are available for Linux and Windows machines. It’s free. ...
... containing useful links : – ~daveh/links – Notably, the GNU PROLOG home page. – Versions of GNU PROLOG are available for Linux and Windows machines. It’s free. ...
History of computers 1
... The objective during it's design was to create a programming language that would be: simple to learn, suitable for a wide variety of applications, machine independent, and would allow complex mathematical expressions to be stated similarly to regular algebraic notation. While still being almost as e ...
... The objective during it's design was to create a programming language that would be: simple to learn, suitable for a wide variety of applications, machine independent, and would allow complex mathematical expressions to be stated similarly to regular algebraic notation. While still being almost as e ...
GUIs - DCU School of Computing
... Interfaces, subclasses, and abstract classes not only facilitate re-use of code we write ourselves, but also facilitate code re-use on a large scale by making it easier to write libraries of related and interacting classes. Two important examples are libraries for (i) collections, and (ii) GUIs (gra ...
... Interfaces, subclasses, and abstract classes not only facilitate re-use of code we write ourselves, but also facilitate code re-use on a large scale by making it easier to write libraries of related and interacting classes. Two important examples are libraries for (i) collections, and (ii) GUIs (gra ...
Programming Languages
... 1. Using the primitives and functionals, define concat, a function that concatenates two lists. 2. Using the primitives and functionals, define reverse, a function that produces a list in the reverse order from its argument 3. Install LispWorks 6.1.1 Personal Edition from lispworks.org 4. Explore Li ...
... 1. Using the primitives and functionals, define concat, a function that concatenates two lists. 2. Using the primitives and functionals, define reverse, a function that produces a list in the reverse order from its argument 3. Install LispWorks 6.1.1 Personal Edition from lispworks.org 4. Explore Li ...
Laboratory - Master de Bioinformatique
... bioinformatics biostatistics computer science mathematics biology ...
... bioinformatics biostatistics computer science mathematics biology ...
Chapter 2 Lecture Notes - Austin Community College
... series of zeros and ones – All instructions telling the computer what to do are stored as a series of zeros and ones ...
... series of zeros and ones – All instructions telling the computer what to do are stored as a series of zeros and ones ...
Classification of Program Languages
... on the processor, giving high levels of control. • Used in embedded systems with low memory and processing power. • Real time applications that require quick reponse times to inputs might also use assembly • Device drivers will also use assembly for more control over access to hardware ...
... on the processor, giving high levels of control. • Used in embedded systems with low memory and processing power. • Real time applications that require quick reponse times to inputs might also use assembly • Device drivers will also use assembly for more control over access to hardware ...
Chapter 1 – Introduction to Computers and C++
... 1.8 The C Standard Library • C programs consist of pieces/modules called functions – A programmer can create his own functions • Advantage: the programmer knows exactly how it works • Disadvantage: time consuming ...
... 1.8 The C Standard Library • C programs consist of pieces/modules called functions – A programmer can create his own functions • Advantage: the programmer knows exactly how it works • Disadvantage: time consuming ...
High Level Synthesis Overview.
... graphs • Computed by visiting hierarchy bottom-up. • Area estimate: • Sum of the area attributes of all vertices. • Worst-case - no sharing. ...
... graphs • Computed by visiting hierarchy bottom-up. • Area estimate: • Sum of the area attributes of all vertices. • Worst-case - no sharing. ...
Overview
... before being executed by the computer. Note that each assembly language instruction is translated into one machine language instruction. It is easy to see that programming in assembly language is preferred to programming in machine language; however programming in assembly language can also be very ...
... before being executed by the computer. Note that each assembly language instruction is translated into one machine language instruction. It is easy to see that programming in assembly language is preferred to programming in machine language; however programming in assembly language can also be very ...
Prog4IntLecture2Java
... • A way to get the computer to ignore certain parts of a computer program. • Useful for: – Identifying the function of certain lines of code – Temporarily removing parts of programs – Leaving notes for yourself and others ...
... • A way to get the computer to ignore certain parts of a computer program. • Useful for: – Identifying the function of certain lines of code – Temporarily removing parts of programs – Leaving notes for yourself and others ...
Principles of Program Design
... granted such as “substituting equals for equals”. If a method uses mutation, it can potentially modify any accessible object. Hence, it is difficult to determine if calling such a method can break a given program invariant. In the absence of mutation, objects can safely be shared (rather than copied ...
... granted such as “substituting equals for equals”. If a method uses mutation, it can potentially modify any accessible object. Hence, it is difficult to determine if calling such a method can break a given program invariant. In the absence of mutation, objects can safely be shared (rather than copied ...
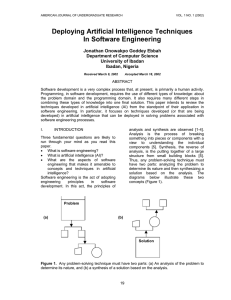
Deploying Artificial Intelligence Techniques in Software Engineering
... Software development is a very complex process that, at present, is primarily a human activity. Programming, in software development, requires the use of different types of knowledge: about the problem domain and the programming domain. It also requires many different steps in combining these types ...
... Software development is a very complex process that, at present, is primarily a human activity. Programming, in software development, requires the use of different types of knowledge: about the problem domain and the programming domain. It also requires many different steps in combining these types ...
Slides
... Memento provides the ability to restore an object to its previous state (undo). Observer is a publish/subscribe pattern that allows a number of observer objects to see an event. State allows an object to alter its behavior when its internal state changes. Strategy allows one of a family of algorithm ...
... Memento provides the ability to restore an object to its previous state (undo). Observer is a publish/subscribe pattern that allows a number of observer objects to see an event. State allows an object to alter its behavior when its internal state changes. Strategy allows one of a family of algorithm ...
A first look at Vanilla
... • language - programming in the huge, composition operators, how known features mutate in new circumstances • trust management - security, authentication, webs of trust • tools - component repositories, code selection • the balance between control and expressiveness ...
... • language - programming in the huge, composition operators, how known features mutate in new circumstances • trust management - security, authentication, webs of trust • tools - component repositories, code selection • the balance between control and expressiveness ...
Typical Questions asked by Wipro and Accenture in Previous
... . What do you mean by atomicity and aggregation? . What is a Phantom Deadlock? . What do you mean by flat file database? . What is a query? . What do you mean by Correlated subquery? . What are the primitive operations common to all record management systems? . What is RDBMS KERNEL? . How do you com ...
... . What do you mean by atomicity and aggregation? . What is a Phantom Deadlock? . What do you mean by flat file database? . What is a query? . What do you mean by Correlated subquery? . What are the primitive operations common to all record management systems? . What is RDBMS KERNEL? . How do you com ...
Software Fundamentals
... for personal computers was Microsoft DOS. Currently, the most popular family of operating systems is the Windows family: Windows 95, Windows 98 and Windows NT. Other popular operating systems include the MacOS (used on all Apple computers), Linux, Unix, Solaris and BeOS. Application software (someti ...
... for personal computers was Microsoft DOS. Currently, the most popular family of operating systems is the Windows family: Windows 95, Windows 98 and Windows NT. Other popular operating systems include the MacOS (used on all Apple computers), Linux, Unix, Solaris and BeOS. Application software (someti ...
Bioinformatics_Curriculum1 - BioQUEST Curriculum Consortium
... How much do we expect biologists to become programmers or programmers to become biologists? How much biology should be included in the course? How does one find “good” data? What is the target audience? ...
... How much do we expect biologists to become programmers or programmers to become biologists? How much biology should be included in the course? How does one find “good” data? What is the target audience? ...
CSC 221: Introduction to Programming Fall 2011
... smaller, faster, more reliable, cheaper to mass produce invented by Bardeen, Brattain, & Shockley in 1948 (won 1956 Nobel Prize in physics) ...
... smaller, faster, more reliable, cheaper to mass produce invented by Bardeen, Brattain, & Shockley in 1948 (won 1956 Nobel Prize in physics) ...
Overview and History
... smaller, faster, more reliable, cheaper to mass produce invented by Bardeen, Brattain, & Shockley in 1948 (won 1956 Nobel Prize in physics) ...
... smaller, faster, more reliable, cheaper to mass produce invented by Bardeen, Brattain, & Shockley in 1948 (won 1956 Nobel Prize in physics) ...
Homework 2
... 2. How does the distinguishing between upper- and lowercase in identifiers affect the three criteria? The affect to readability can be positive when it is used in conjunction with a cohesive programming technique. The use of upper case letters to help certain types of identifiers stand out in the co ...
... 2. How does the distinguishing between upper- and lowercase in identifiers affect the three criteria? The affect to readability can be positive when it is used in conjunction with a cohesive programming technique. The use of upper case letters to help certain types of identifiers stand out in the co ...
Programming Development Environment
... A computer is a physical device that can read input, compute, and produce corresponding output It “understands” a small set of machine instructions, which it can execute, one at a time (for a uni-processor) It is possible, but very tedious, to write a program in such machine instructions An Assemble ...
... A computer is a physical device that can read input, compute, and produce corresponding output It “understands” a small set of machine instructions, which it can execute, one at a time (for a uni-processor) It is possible, but very tedious, to write a program in such machine instructions An Assemble ...