function
... • Cells in the list have a right and a left – Right part points to next cell in list – Left part points to value of the cell ...
... • Cells in the list have a right and a left – Right part points to next cell in list – Left part points to value of the cell ...
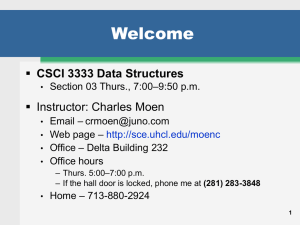
CSCI 3333 Data Structures Today`s Objectives
... Accomplished by keeping the instance variables private The user of an object in your program can change its data, but cannot change it directly Data members are manipulated only by accessor methods ...
... Accomplished by keeping the instance variables private The user of an object in your program can change its data, but cannot change it directly Data members are manipulated only by accessor methods ...
Powerpoint ()
... • Like a mixin in Ruby • Think Java interfaces, but they can have methods defined on them ...
... • Like a mixin in Ruby • Think Java interfaces, but they can have methods defined on them ...
DS | 1. Introduction To Data Structure
... some value, or a set of values, as input and produces some value, or a set of values, as output. • It can also be defined as sequence of computational steps that transform the input into the output. • An algorithm can be expressed in three ways:• (i) in any natural language such as English, called p ...
... some value, or a set of values, as input and produces some value, or a set of values, as output. • It can also be defined as sequence of computational steps that transform the input into the output. • An algorithm can be expressed in three ways:• (i) in any natural language such as English, called p ...
PL , OS and OOPS Concept - Banking Solutions , Nagpur
... Once a process is executed for given time period. Process is preempted and other process executes for given time period. Context switching is used to save states of ...
... Once a process is executed for given time period. Process is preempted and other process executes for given time period. Context switching is used to save states of ...
My research interests include object
... I have been designing and implementing a new object-oriented language named FlexibO. This language supports a few new features such as resource control, on-line collaboration, colourful variables and ownership control. In this workshop, I will discuss about its flexible binding mechanism by the way ...
... I have been designing and implementing a new object-oriented language named FlexibO. This language supports a few new features such as resource control, on-line collaboration, colourful variables and ownership control. In this workshop, I will discuss about its flexible binding mechanism by the way ...
Introduction to Programming in Python
... • Text characters are translated into numbers by using the ASCII or Unicode standards. Across computer systems, the word “Python” is seen as the sequence: 80 121 116 104 111 110, one number for each letter. • Likewise, a digital image is divided into many rows and columns, and each cell is a pixel. ...
... • Text characters are translated into numbers by using the ASCII or Unicode standards. Across computer systems, the word “Python” is seen as the sequence: 80 121 116 104 111 110, one number for each letter. • Likewise, a digital image is divided into many rows and columns, and each cell is a pixel. ...
A Lesson on Instruction Set Architectures (ISAs)
... Does the hardware need to change? Change nand instruction to and Add a new mul (multiply) instruction New piece of hardware that can add faster New operating system that is better at multitasking ...
... Does the hardware need to change? Change nand instruction to and Add a new mul (multiply) instruction New piece of hardware that can add faster New operating system that is better at multitasking ...
ppt
... The Java compiler translates the program into bytecode, a sort of intermediate language. When the Java program is run, the Java Virtual Machine compiles/translates the bytecode into machine code, and then the program runs. The machine code produced is different depending on the computer. The bytecod ...
... The Java compiler translates the program into bytecode, a sort of intermediate language. When the Java program is run, the Java Virtual Machine compiles/translates the bytecode into machine code, and then the program runs. The machine code produced is different depending on the computer. The bytecod ...
First day handout
... Naturally, you may discuss assignments with others, but the discussion should not extend to writing actual code, picking variable names, agreeing on specifications or comments, etc. If you do an assignment with another person (in a Group), you must both sit at the computer together, working together ...
... Naturally, you may discuss assignments with others, but the discussion should not extend to writing actual code, picking variable names, agreeing on specifications or comments, etc. If you do an assignment with another person (in a Group), you must both sit at the computer together, working together ...
View File - UET Taxila
... Java does provide support for I/O as it relates to files and networks. I/O in java is performed through streams. A stream is nothing but an abstraction that either reads data from a device or displays it on some output device. I/O classes and methods are applied to any type of input, output device. ...
... Java does provide support for I/O as it relates to files and networks. I/O in java is performed through streams. A stream is nothing but an abstraction that either reads data from a device or displays it on some output device. I/O classes and methods are applied to any type of input, output device. ...
Readable, writable, both, or neither? A programming language that
... A programming language that has an relatively small number of features and constructs, has a large number predefined data types tailored for use in a particular programming domain, statements and constructs that are not very intuitive but that are extremely powerful and complex when employed within ...
... A programming language that has an relatively small number of features and constructs, has a large number predefined data types tailored for use in a particular programming domain, statements and constructs that are not very intuitive but that are extremely powerful and complex when employed within ...
pptx
... – And various optimizations are possible • [Also use a much better data structure for looking up variables than a list] Spring 2017 ...
... – And various optimizations are possible • [Also use a much better data structure for looking up variables than a list] Spring 2017 ...
Low-Level Programming Languages
... • List the operations that a computer can perform • Discuss the relationship between levels of abstraction and the determination of concrete algorithm steps • Describe the important features of the Pep/7 virtual machine • Distinguish between immediate mode addressing and ...
... • List the operations that a computer can perform • Discuss the relationship between levels of abstraction and the determination of concrete algorithm steps • Describe the important features of the Pep/7 virtual machine • Distinguish between immediate mode addressing and ...
Chapter 4
... Ask the computer questions in English-like sentences (aka database query languages) Structured Query Language (SQL) Standardized query language used to perform database queries & manipulations Most modern database management system applications use or support SQL ...
... Ask the computer questions in English-like sentences (aka database query languages) Structured Query Language (SQL) Standardized query language used to perform database queries & manipulations Most modern database management system applications use or support SQL ...
JavaIO
... println() the data may not actually be written to the underlying output stream right away • You can call flush() at any time to force any data lounging around to be written through • This is important in network programming! Always remember to flush() if you hope to see the data actually be sent acr ...
... println() the data may not actually be written to the underlying output stream right away • You can call flush() at any time to force any data lounging around to be written through • This is important in network programming! Always remember to flush() if you hope to see the data actually be sent acr ...
Introduction: chap. 1 - NYU Computer Science Department
... The C Programming Language C was originally created in 1972 by Dennis Ritchie at Bell Labs= C is a relatively low-level high-level language; i.e. deals with numbers, characters, and memory addresses ...
... The C Programming Language C was originally created in 1972 by Dennis Ritchie at Bell Labs= C is a relatively low-level high-level language; i.e. deals with numbers, characters, and memory addresses ...
Programming “Safety” - The Software Enterprise at ASU
... If your code is intended to be used in a particular way, write it so that the code cannot be used in any other way. • If a member is not intended to be used by other functions, enforce this by making it private or protected etc. • Use qualifiers such as final and abstract etc. to enforce intention ...
... If your code is intended to be used in a particular way, write it so that the code cannot be used in any other way. • If a member is not intended to be used by other functions, enforce this by making it private or protected etc. • Use qualifiers such as final and abstract etc. to enforce intention ...
Fundamentals
... statements for a program. These statements are known as source code. A text editor is used to edit and save a Java source code file. Source code files have a .java file extension. A compiler is a program that translates source code into an executable form. ...
... statements for a program. These statements are known as source code. A text editor is used to edit and save a Java source code file. Source code files have a .java file extension. A compiler is a program that translates source code into an executable form. ...
- gidnepal.com
... each module is composed of one or more procedures (also called as functions or subroutines) The key principle of structured programming technique is modularity with single entry and sings exit point. For each procedure, there must be one starting point and one ending point. Structured programming is ...
... each module is composed of one or more procedures (also called as functions or subroutines) The key principle of structured programming technique is modularity with single entry and sings exit point. For each procedure, there must be one starting point and one ending point. Structured programming is ...
Programming
... • Information system includes: – Data – People – Procedures – Hardware – Software ...
... • Information system includes: – Data – People – Procedures – Hardware – Software ...
9.26 Reusable biodiversity informatics tools
... However when operating on large datasets, network communication often becomes a bottleneck. In such cases, using software installed on the client side can significantly improve processing times. During the development of some Global Names Architecture (GNA) applications such as Global Names Inde ...
... However when operating on large datasets, network communication often becomes a bottleneck. In such cases, using software installed on the client side can significantly improve processing times. During the development of some Global Names Architecture (GNA) applications such as Global Names Inde ...
Problem Set 2
... natural subrecursive class are the elementary functions. An interesting issue is whether there is a subrecursive PL for the polynomial time computable functions. There are several, and they are more complex to define. We obtain a nice definition by introducing step counting in subrecursive languages ...
... natural subrecursive class are the elementary functions. An interesting issue is whether there is a subrecursive PL for the polynomial time computable functions. There are several, and they are more complex to define. We obtain a nice definition by introducing step counting in subrecursive languages ...
Lecture-1
... Machine code or machine language is a set of instructions executed directly by a computer's Central Processing Unit (CPU). While easily understood by computers, machine languages are almost impossible for humans to use because they consist entirely of numbers. ...
... Machine code or machine language is a set of instructions executed directly by a computer's Central Processing Unit (CPU). While easily understood by computers, machine languages are almost impossible for humans to use because they consist entirely of numbers. ...