- Cal State LA - Instructional Web Server
... L: the likelihood of the pedigree data n:number of people Xi:phenotype of ith person Gi:possible genotype of ith person ...
... L: the likelihood of the pedigree data n:number of people Xi:phenotype of ith person Gi:possible genotype of ith person ...
Galois Field in Cryptography
... AddRoundKey is the most important stage as it is the stage that provides uniqueness to the encryption thus is inevitably a complex operation by itself. The output of AddRoundKey fully depends on the key or the password specified by the user. In this stage a subkey, which is the same size as the stat ...
... AddRoundKey is the most important stage as it is the stage that provides uniqueness to the encryption thus is inevitably a complex operation by itself. The output of AddRoundKey fully depends on the key or the password specified by the user. In this stage a subkey, which is the same size as the stat ...
Section 2.1 – The Definition of a Derivative 1 Section 2.1 The
... We find the instantaneous rate of change when we take the limit of the difference quotient. The derivative of f with respect to x is the function f ' (read “f prime”) defined by f ( x h) f ( x ) . The domain of f ' ( x) is the set of all x for which the limit exists. f '( x) lim ...
... We find the instantaneous rate of change when we take the limit of the difference quotient. The derivative of f with respect to x is the function f ' (read “f prime”) defined by f ( x h) f ( x ) . The domain of f ' ( x) is the set of all x for which the limit exists. f '( x) lim ...
Pseudo Code for Case/Non-Case Version of Heart Failure
... Secondary problem list section of the clinical note for at least one positive mention of one of the heart failure terms. Positive mention is defined using ConText for assigning statuses to each NLP result – positive, probable, and negative 5-7. Thus a positive hit for this requirement equates to a n ...
... Secondary problem list section of the clinical note for at least one positive mention of one of the heart failure terms. Positive mention is defined using ConText for assigning statuses to each NLP result – positive, probable, and negative 5-7. Thus a positive hit for this requirement equates to a n ...
CIS101 week 10
... The computer can only execute one operation at a time When an expression has more than one operator, they have to be carried out in order determined by rule of mathematics known as “operator precedence” ...
... The computer can only execute one operation at a time When an expression has more than one operator, they have to be carried out in order determined by rule of mathematics known as “operator precedence” ...
Slides - Intro to Python File
... Flowcharts Flowcharts are used to plan programs before they are created. The start or end of the program. There may be more than one way to complete the algorithm and there may be more than one end box. A process, that is doing something for example calculating something. An input or output, for ex ...
... Flowcharts Flowcharts are used to plan programs before they are created. The start or end of the program. There may be more than one way to complete the algorithm and there may be more than one end box. A process, that is doing something for example calculating something. An input or output, for ex ...
Readable, writable, both, or neither? A programming language that
... By definition, the first two Fibonacci numbers are 0 and 1, and each remaining number is the sum of the previous two. Some sources omit the initial 0, instead beginning the sequence with two 1s. ...
... By definition, the first two Fibonacci numbers are 0 and 1, and each remaining number is the sum of the previous two. Some sources omit the initial 0, instead beginning the sequence with two 1s. ...
Lesson 1 - Square Roots - Algebra I Keystone Exam Preparation
... and then press the square root key (usually % b) and others require you to press the square root key and then enter the value. You will need to determine which method your calculator uses. ...
... and then press the square root key (usually % b) and others require you to press the square root key and then enter the value. You will need to determine which method your calculator uses. ...
Discussion
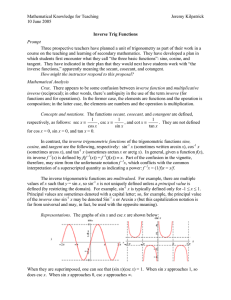
... course on the teaching and learning of secondary mathematics. They have developed a plan in which students first encounter what they call “the three basic functions”: sine, cosine, and tangent. They have indicated in their plan that they would next have students work with “the inverse functions,” ap ...
... course on the teaching and learning of secondary mathematics. They have developed a plan in which students first encounter what they call “the three basic functions”: sine, cosine, and tangent. They have indicated in their plan that they would next have students work with “the inverse functions,” ap ...
Slide 1
... Ideally, N times (number of processors) In practice impossible The problem does not decompose into N equal parts Communication and control overhead < 1 / f, where f is the largest separable fraction of the problem ...
... Ideally, N times (number of processors) In practice impossible The problem does not decompose into N equal parts Communication and control overhead < 1 / f, where f is the largest separable fraction of the problem ...
On Cardinalities of Automorphism Groups of Uniform Binary Relations
... Problem. (Ulam) Can we find, for every natural number n, a binary relation B on a infinite set E (for example, on a set of cardinality continuum) such that the structure (E , B) has precisely n automorphisms? Proposition ( ZFC) (Kharazishvili) If is any infinite cardinal number, and G is a group ...
... Problem. (Ulam) Can we find, for every natural number n, a binary relation B on a infinite set E (for example, on a set of cardinality continuum) such that the structure (E , B) has precisely n automorphisms? Proposition ( ZFC) (Kharazishvili) If is any infinite cardinal number, and G is a group ...
Unit 3: Functions - Connecticut Core Standards
... graph (e.g., where the function is increasing or decreasing, linear or nonlinear). Sketch a graph that exhibits the qualitative features of a function that has been described verbally. A-CED 2. Create equations in two or more variables to represent relationships between quantities; graph equations o ...
... graph (e.g., where the function is increasing or decreasing, linear or nonlinear). Sketch a graph that exhibits the qualitative features of a function that has been described verbally. A-CED 2. Create equations in two or more variables to represent relationships between quantities; graph equations o ...
Dynamic Programming
... the space of sub-problems is “small”, in the sense that a recursive algorithm for the problem solves the same sub-problems over and over, rather than always generating new sub-problems ...
... the space of sub-problems is “small”, in the sense that a recursive algorithm for the problem solves the same sub-problems over and over, rather than always generating new sub-problems ...