Slides
... – Start with random weights ri in range [1,c] – At any point in time wi = ri + ci Run with private • ci is # of times element ai was requested. counter – Arrange elements according to weights – Privacy: from privacy of counters • list depends on counters plus randomness ...
... – Start with random weights ri in range [1,c] – At any point in time wi = ri + ci Run with private • ci is # of times element ai was requested. counter – Arrange elements according to weights – Privacy: from privacy of counters • list depends on counters plus randomness ...
Tower of Hanoi Investigation 11/16/93
... Looking at the numbers, especially the ones you are sure of, do you see a pattern? Is there a formula? If n is the number of rings in the original stack, and H(n) is the minimum number of moves needed to transfer the stack to a different peg, then a formula is: H(n) = ...
... Looking at the numbers, especially the ones you are sure of, do you see a pattern? Is there a formula? If n is the number of rings in the original stack, and H(n) is the minimum number of moves needed to transfer the stack to a different peg, then a formula is: H(n) = ...
File System Examples
... Algorithm to ensure fragments only used for end of file Limit number of fragments per block to 2, 4, or 8 Keep track of free fragments ...
... Algorithm to ensure fragments only used for end of file Limit number of fragments per block to 2, 4, or 8 Keep track of free fragments ...
Java: Primitive Data Types, Variables and Constants Introduction
... Java, primitive data types are used to define variables and constants. A variable's or constant's data type indicates what sort of value it represents, such as whether it is an integer, a floating-point number or a character, and determines the values it may contain and the operations that may be pe ...
... Java, primitive data types are used to define variables and constants. A variable's or constant's data type indicates what sort of value it represents, such as whether it is an integer, a floating-point number or a character, and determines the values it may contain and the operations that may be pe ...
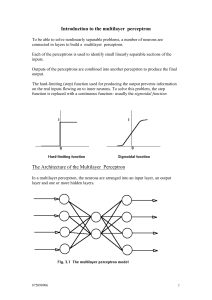
Introduction to the multilayer perceptron
... The energy landscape The behaviour of a neural network as it attempts to arrive at a solution can be visualised in terms of the error or energy function Ep. The energy is a function of the input and the weights. For a given pattern, Ep can be plotted against the weights to give the so called energy ...
... The energy landscape The behaviour of a neural network as it attempts to arrive at a solution can be visualised in terms of the error or energy function Ep. The energy is a function of the input and the weights. For a given pattern, Ep can be plotted against the weights to give the so called energy ...
PPT - Tandy Warnow
... 1.Remove the parsimony uninformative sites 2.Let I be the number of sites that support ((A,B),(C,D)) 3.Let J be the number of sites that support ((A,C),(B,D)) 4.Let K be the number of sites that support ((A,D),(B,C)) 5.Whichever tree is supported by the largest number of sites, return that tree. (Fo ...
... 1.Remove the parsimony uninformative sites 2.Let I be the number of sites that support ((A,B),(C,D)) 3.Let J be the number of sites that support ((A,C),(B,D)) 4.Let K be the number of sites that support ((A,D),(B,C)) 5.Whichever tree is supported by the largest number of sites, return that tree. (Fo ...
Exam and Answers for 1999/00
... c) Genetic algorithms are an example of a population based approach to problem solving. Give your ideas as to other potential population based approaches that could be used. Ideally you should not use the example that was presented in the lectures. The example given in the lectures was an approach b ...
... c) Genetic algorithms are an example of a population based approach to problem solving. Give your ideas as to other potential population based approaches that could be used. Ideally you should not use the example that was presented in the lectures. The example given in the lectures was an approach b ...
Streams
... Since the stream represents a function, we can write operations which work on functions and try to implement them in terms of the coefficients of the series. One such operation is integration. The integral of an infinite polynomial is also an infinite polynomial, but the coefficients will be differe ...
... Since the stream represents a function, we can write operations which work on functions and try to implement them in terms of the coefficients of the series. One such operation is integration. The integral of an infinite polynomial is also an infinite polynomial, but the coefficients will be differe ...
Sockets - cs.wisc.edu
... – Applications use buffers as do protocols • Copies are VERY expensive • Message abstraction enables pointers to be used and minimal copies Fall, 2001 ...
... – Applications use buffers as do protocols • Copies are VERY expensive • Message abstraction enables pointers to be used and minimal copies Fall, 2001 ...
6.037, IAP 2016—Streams 1 MASSACHVSETTS INSTITVTE OF TECHNOLOGY
... Since the stream represents a function, we can write operations which work on functions and try to implement them in terms of the coefficients of the series. One such operation is integration. The integral of an infinite polynomial is also an infinite polynomial, but the coefficients will be differe ...
... Since the stream represents a function, we can write operations which work on functions and try to implement them in terms of the coefficients of the series. One such operation is integration. The integral of an infinite polynomial is also an infinite polynomial, but the coefficients will be differe ...