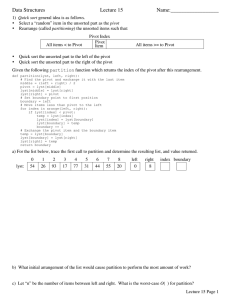
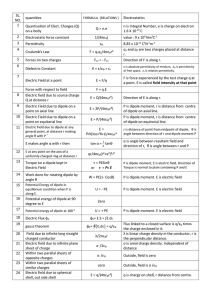
Who`s doing what?
... tabulation. The paper by L. Zayatz also addresses other SDC research areas at the USBC like synthetic micro data generation (also used to protect frequency tabular data) and a remote microdata analysis system. L. Cox (US NCHS) compares properties of two methods for Controlled Tabular Adjustment, one ...
... tabulation. The paper by L. Zayatz also addresses other SDC research areas at the USBC like synthetic micro data generation (also used to protect frequency tabular data) and a remote microdata analysis system. L. Cox (US NCHS) compares properties of two methods for Controlled Tabular Adjustment, one ...
Problem 1212. A Rare, if Obtuse, Ratio Find an obtuse triangle with
... below follow the solution of William Pierce (Pi Mu Epsilon Journal, Problem 971, 11:3 Fall 2000, 159-160). These notes start with an elementary solution to the problem, and then discuss a more sophisticated approach uses Chebyshev polynomials (David Broadhurst, Russ Gordon); there is also an approac ...
... below follow the solution of William Pierce (Pi Mu Epsilon Journal, Problem 971, 11:3 Fall 2000, 159-160). These notes start with an elementary solution to the problem, and then discuss a more sophisticated approach uses Chebyshev polynomials (David Broadhurst, Russ Gordon); there is also an approac ...
General setting of the interpolation problem (with respect to the
... Particular cases: Lagrange interpolation/control polygion Taylor interpolation/control polygon Hermite interpolation/control polygon Fast change of another functional basis to a respective interpolation basis: a general property. Existence and uniqueness of the solution of the interpolation problem ...
... Particular cases: Lagrange interpolation/control polygion Taylor interpolation/control polygon Hermite interpolation/control polygon Fast change of another functional basis to a respective interpolation basis: a general property. Existence and uniqueness of the solution of the interpolation problem ...
JavaCloak: Reflecting on Java Typing for Class Reuse using Proxies
... Another problem is the forwarding of method calls from the proxy to the real object. In JavaCloak, all invocations on the public methods of an object are forwarded, including hashCode and equals. This means it is not possible to call these methods on the proxies themselves. Therefore, at the JavaClo ...
... Another problem is the forwarding of method calls from the proxy to the real object. In JavaCloak, all invocations on the public methods of an object are forwarded, including hashCode and equals. This means it is not possible to call these methods on the proxies themselves. Therefore, at the JavaClo ...