computer_network_basics
... institutional link to ISP (Internet) institutional router Ethernet switch ...
... institutional link to ISP (Internet) institutional router Ethernet switch ...
(Uas) SIP Proxy SIP Registar SIP Redirect Server
... Voice over Internet Protocol. Two or more people can speak with each other over internet using their computers. Skype is the first peer-to-peer based IP telephony. ...
... Voice over Internet Protocol. Two or more people can speak with each other over internet using their computers. Skype is the first peer-to-peer based IP telephony. ...
IPAddressing
... – 1. Express the subnetwork IP address in binary form. – 2. Replace the network and subnet portion of the address with all 1s. – 3. Replace the host portion of the address with all 0s. – 4. Convert the binary expression back to dotted-decimal notation. ...
... – 1. Express the subnetwork IP address in binary form. – 2. Replace the network and subnet portion of the address with all 1s. – 3. Replace the host portion of the address with all 0s. – 4. Convert the binary expression back to dotted-decimal notation. ...
Slide 1
... Collision Detection and Recovery It is possible that two transmitters send data simultaneously and collision happens. Each transceiver monitors the cable to see if there is a coliision. When it detects collision it aborts transmission and remain idle before trying again. They use a binary e ...
... Collision Detection and Recovery It is possible that two transmitters send data simultaneously and collision happens. Each transceiver monitors the cable to see if there is a coliision. When it detects collision it aborts transmission and remain idle before trying again. They use a binary e ...
Module 2 Transport Layer Protocols
... We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
Course Computer Communications Study Period 2, 2012
... Addressing, sockets socket: Internet application programming interface – 2 processes communicate by sending data into socket, reading data out of socket (like sending out, receiving in via doors) ...
... Addressing, sockets socket: Internet application programming interface – 2 processes communicate by sending data into socket, reading data out of socket (like sending out, receiving in via doors) ...
LoadBalancing - Indico
... OSI Layer 4 (the Transport Layer – TCP/UDP) switching Cluster is hidden by a switch behind a single virtual IP address Switch role also includes: Monitoring of all nodes in the cluster Keep track of the network flow Forwarding of packets according to policies ...
... OSI Layer 4 (the Transport Layer – TCP/UDP) switching Cluster is hidden by a switch behind a single virtual IP address Switch role also includes: Monitoring of all nodes in the cluster Keep track of the network flow Forwarding of packets according to policies ...
How Network Address Translation Works
... at the HowStuffWorks Web site. There's a very good chance that you are using Network Address Translation (NAT) right now. The Internet has grown larger than anyone ever imagined it could be. Although the exact size is unknown, the current estimate is that there are about 100 million hosts and more t ...
... at the HowStuffWorks Web site. There's a very good chance that you are using Network Address Translation (NAT) right now. The Internet has grown larger than anyone ever imagined it could be. Although the exact size is unknown, the current estimate is that there are about 100 million hosts and more t ...
Setup Wizard
... To connect to a hub or PC, use a RJ45 cable. You can connect the router to up to four LAN devices. The ports are auto-sensing MDI/X and either straight-through cable or crossover cable can be used. Connection to USB port Connect the USB port to a PC with a standard USB cable. Connection to (PWR) Pow ...
... To connect to a hub or PC, use a RJ45 cable. You can connect the router to up to four LAN devices. The ports are auto-sensing MDI/X and either straight-through cable or crossover cable can be used. Connection to USB port Connect the USB port to a PC with a standard USB cable. Connection to (PWR) Pow ...
Autonomic Response to Distributed Denial of Service Attacks*
... to the edge of the CITRA system. This technique is immune to address spoofing because it relies on empirical (audit) data rather than the contents of IP source address fields to determine whether a boundary controller is on the attack path. At each CITRA component along the attack path, responses are ...
... to the edge of the CITRA system. This technique is immune to address spoofing because it relies on empirical (audit) data rather than the contents of IP source address fields to determine whether a boundary controller is on the attack path. At each CITRA component along the attack path, responses are ...
IPv6
... • When multiple extension headers are used in an IPv6 packet, their order must be as follows: • Basic IPv6 header • Hop-by-Hop Options • Destination Options (if the Routing header is used) • Routing • Fragment • Authentication • Encapsulating Security Payload • Destination Options • Upper-layer (TCP ...
... • When multiple extension headers are used in an IPv6 packet, their order must be as follows: • Basic IPv6 header • Hop-by-Hop Options • Destination Options (if the Routing header is used) • Routing • Fragment • Authentication • Encapsulating Security Payload • Destination Options • Upper-layer (TCP ...
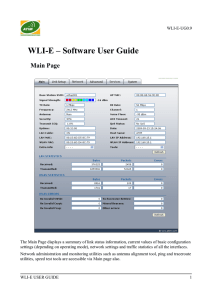
WLI-E – Software User Guide
... transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while addressing all hosts in a given network range with a single destination IP address) is accounted. As ...
... transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while addressing all hosts in a given network range with a single destination IP address) is accounted. As ...
How Network Address Translation Works
... A computer on the stub domain attempts to connect to a computer outside the network, such as a Web server. The router receives the packet from the computer on the stub domain. The router saves the computer's non-routable IP address to an address translation table. The router replaces the sending com ...
... A computer on the stub domain attempts to connect to a computer outside the network, such as a Web server. The router receives the packet from the computer on the stub domain. The router saves the computer's non-routable IP address to an address translation table. The router replaces the sending com ...
Chapter 1. Introduction to Data Communications
... Programs for Dynamic Addressing • Bootstrap Protocol (bootp) ...
... Programs for Dynamic Addressing • Bootstrap Protocol (bootp) ...
Chapter 1. Introduction to Data Communications
... Programs for Dynamic Addressing • Bootstrap Protocol (bootp) ...
... Programs for Dynamic Addressing • Bootstrap Protocol (bootp) ...
Chap 18 - The University of Tulsa
... 18.4.4 DHCP Address assignment can be done manually or automatically using the Dynamic Host Configuration Protocol (DHCP). DHCP is an application-layer program, using the client-server paradigm, that helps TCP/IP at the network layer. ...
... 18.4.4 DHCP Address assignment can be done manually or automatically using the Dynamic Host Configuration Protocol (DHCP). DHCP is an application-layer program, using the client-server paradigm, that helps TCP/IP at the network layer. ...
File transfer Protocol (FTP)
... •An internet protocol that enables the transfer of files from one computer to another. •When downloading files to a computer using Web browser, you often use FTP without even knowing it. •Evitech has a FTP server program which can be accessed with a client program (e.g. WSFTP). ...
... •An internet protocol that enables the transfer of files from one computer to another. •When downloading files to a computer using Web browser, you often use FTP without even knowing it. •Evitech has a FTP server program which can be accessed with a client program (e.g. WSFTP). ...
chapter 10 - University of Windsor
... All hosts & routers at the site agree to honor the site’s addressing scheme Other sites on the internet can treat addresses as in the original scheme Large population of Networks will lead to Immense administrative overhead for managing the netid’s Routing tables of routers may become very l ...
... All hosts & routers at the site agree to honor the site’s addressing scheme Other sites on the internet can treat addresses as in the original scheme Large population of Networks will lead to Immense administrative overhead for managing the netid’s Routing tables of routers may become very l ...
USB2.0 NAS Dongle User`s Manual
... By default, the “IP config” is set to “Automatic IP”. This is the recommended setting and will allow NAS Dongle to obtain its IP address automatically. If you prefer setting it manually, select the static IP option, enter your own value and click apply to confirm the new setting. Setting it manually ...
... By default, the “IP config” is set to “Automatic IP”. This is the recommended setting and will allow NAS Dongle to obtain its IP address automatically. If you prefer setting it manually, select the static IP option, enter your own value and click apply to confirm the new setting. Setting it manually ...
ppt - Temple University
... IP address of DNS server encapsulation of DHCP server, frame forwarded to client, demux’ing up to DHCP at client client now knows its IP address, name and IP address of DSN server, IP address of its first-hop ...
... IP address of DNS server encapsulation of DHCP server, frame forwarded to client, demux’ing up to DHCP at client client now knows its IP address, name and IP address of DSN server, IP address of its first-hop ...
IPv6
... • When multiple extension headers are used in an IPv6 packet, their order must be as follows: • Basic IPv6 header • Hop-by-Hop Options • Destination Options (if the Routing header is used) • Routing • Fragment • Authentication • Encapsulating Security Payload • Destination Options • Upper-layer (TCP ...
... • When multiple extension headers are used in an IPv6 packet, their order must be as follows: • Basic IPv6 header • Hop-by-Hop Options • Destination Options (if the Routing header is used) • Routing • Fragment • Authentication • Encapsulating Security Payload • Destination Options • Upper-layer (TCP ...
Network-INT201
... similar to the name of a person in human communication physical address in Ethernet network physically assigned to the host NIC (network interface card) How to send the msg? See Cisco academy chapter 3.3.3.1 Application Layer ...
... similar to the name of a person in human communication physical address in Ethernet network physically assigned to the host NIC (network interface card) How to send the msg? See Cisco academy chapter 3.3.3.1 Application Layer ...
Typical AVL client applications in the control rooms and offices
... • Collects and stores the latest position data of the traced radio terminals in the network • Provides interface for the authorized AVL client applications to access location information of the radio terminals based on the definitions in the network • Manages the parameters of position updates for e ...
... • Collects and stores the latest position data of the traced radio terminals in the network • Provides interface for the authorized AVL client applications to access location information of the radio terminals based on the definitions in the network • Manages the parameters of position updates for e ...
Marina Papatriantafilou – Application layer
... Addressing, sockets socket: Internet application programming interface – 2 processes communicate by sending data into socket, reading data out of socket (like sending out, receiving in via doors) ...
... Addressing, sockets socket: Internet application programming interface – 2 processes communicate by sending data into socket, reading data out of socket (like sending out, receiving in via doors) ...