The Internet and Its Uses - Mt. Hood Community College
... regulates the assignment of OUI numbers. Within the OUI, there are 2 bits that have meaning only when used in the destination address, as follows: –Broadcast or multicast bit: Indicates to the receiving interface that the frame is destined for all or a group of end stations on the LAN segment. –Loca ...
... regulates the assignment of OUI numbers. Within the OUI, there are 2 bits that have meaning only when used in the destination address, as follows: –Broadcast or multicast bit: Indicates to the receiving interface that the frame is destined for all or a group of end stations on the LAN segment. –Loca ...
File
... Returns an array of String objects containing all of the values the given request parameter has, or null if the parameter does not exist. ...
... Returns an array of String objects containing all of the values the given request parameter has, or null if the parameter does not exist. ...
wienet - Wieland Electric Inc.
... Wieland's wienet VPN industrial routers ensure increased efficiency and data security. Whether it is about the control of machines, monitoring of production lines or the coordination of all production areas a permanent communication between devices is needed to complete such a complex task. Access t ...
... Wieland's wienet VPN industrial routers ensure increased efficiency and data security. Whether it is about the control of machines, monitoring of production lines or the coordination of all production areas a permanent communication between devices is needed to complete such a complex task. Access t ...
DSL-300G ADSL Modem User’s Guide
... Any common web browser can be used to configure the Modem using the web configuration management software. The program is designed to work best with more recently released browsers such as Microsoft Internet Explorer® version 5.0, Netscape Navigator® version 4.7, or later versions. The web browser m ...
... Any common web browser can be used to configure the Modem using the web configuration management software. The program is designed to work best with more recently released browsers such as Microsoft Internet Explorer® version 5.0, Netscape Navigator® version 4.7, or later versions. The web browser m ...
Jigsaw: Solving the Puzzle of Enterprise 802.11 Analysis
... “The wireless is being flaky.” “Flaky how?” “Well, my connections got dropped earlier and now things seem very sloooow.” “OK, we will take a look” Employee ...
... “The wireless is being flaky.” “Flaky how?” “Well, my connections got dropped earlier and now things seem very sloooow.” “OK, we will take a look” Employee ...
VMWARE PUBLIC CLOUD INFRASTRUCTURE – Development environment design and implementation
... and distributed resources. When a cluster is formed of two or more hosts, rapid recovery from a host failure is possible with high availability. ESXi hosts are constantly polled by a vCenter Server to ensure they respond, but hosts also communicate among themselves using a heartbeat signal to ensure ...
... and distributed resources. When a cluster is formed of two or more hosts, rapid recovery from a host failure is possible with high availability. ESXi hosts are constantly polled by a vCenter Server to ensure they respond, but hosts also communicate among themselves using a heartbeat signal to ensure ...
Route Optimization
... [process-id] [match route-type] [metric metricvalue] [route-map map-tag] RtrA(config)# router rip RtrA(config-router)# redistribute ospf ? ...
... [process-id] [match route-type] [metric metricvalue] [route-map map-tag] RtrA(config)# router rip RtrA(config-router)# redistribute ospf ? ...
945U-E Ethernet Modem
... • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be operated as supplied by ELPRO Technologies. Any changes or modifications made to the device without the written ...
... • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be operated as supplied by ELPRO Technologies. Any changes or modifications made to the device without the written ...
IxNetwork
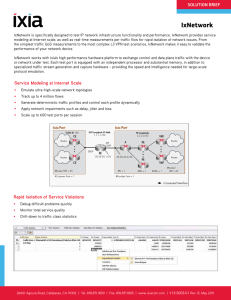
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
... IxNetwork is specifically designed to test IP network infrastructure functionality and performance. IxNetwork provides service modeling at Internet scale, as well as real-time measurements per traffic flow for rapid isolation of network issues. From the simplest traffic QoS measurements to the most ...
Cooper Bussmann 945U-E Wireless Ethernet Modem & Device Server User Manual
... • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be operated as supplied by ELPRO Technologies. Any changes or modifications made to the device without the written ...
... • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be operated as supplied by ELPRO Technologies. Any changes or modifications made to the device without the written ...
SoftRouter Plus User Guide
... this manual we will refer to PPP as the connection method, in each instance you may also use SLIP. The SoftRouter Plus can be used as a Remote Access Server, with password security. For a basic Internet access the SoftRouter Plus configures itself and your client computers automatically, employing a ...
... this manual we will refer to PPP as the connection method, in each instance you may also use SLIP. The SoftRouter Plus can be used as a Remote Access Server, with password security. For a basic Internet access the SoftRouter Plus configures itself and your client computers automatically, employing a ...
MSI RG54SE Wireless 11g Broadband Router
... - Heaters, ferroconcrete, etc. - open computer systems, etc. - Microwave oven, etc, Communication (exchange data) is dependent on the software of the WLAN devices. ...
... - Heaters, ferroconcrete, etc. - open computer systems, etc. - Microwave oven, etc, Communication (exchange data) is dependent on the software of the WLAN devices. ...
COSC4377 TCP vs UDP – Example Statistics
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
IPv6 - DePaul University
... A provider-based unicast address is generally used by a normal host as a unicast address. (Also known as aggregatable global unicast addresses.) Provider identifier - who provides the Internet access, such as an ISP (variable length field but 16 bits recommended). Subscriber identifier - when an org ...
... A provider-based unicast address is generally used by a normal host as a unicast address. (Also known as aggregatable global unicast addresses.) Provider identifier - who provides the Internet access, such as an ISP (variable length field but 16 bits recommended). Subscriber identifier - when an org ...
CS 291 Special Topics on Network Security
... Internet is a complex system lots of jobs Media access, routing, packet forwarding, error detection/correction (reliability), congestion control, etc… Modularization eases maintenance and facilitate deployment Clearly defined interface Change of implementation of layer’s service transparent ...
... Internet is a complex system lots of jobs Media access, routing, packet forwarding, error detection/correction (reliability), congestion control, etc… Modularization eases maintenance and facilitate deployment Clearly defined interface Change of implementation of layer’s service transparent ...
Manual
... Step 4: Select Obtain an IP address automatically and Obtain DNS server address automatically then click OK to complete IP configuring process. ...
... Step 4: Select Obtain an IP address automatically and Obtain DNS server address automatically then click OK to complete IP configuring process. ...
ppt
... – AF_INET (IPv4), AF_INET6 (IPv6), AF_LOCAL (local Unix), – AF_ROUTE (access to routing tables), AF_KEY (new, for encryption) ...
... – AF_INET (IPv4), AF_INET6 (IPv6), AF_LOCAL (local Unix), – AF_ROUTE (access to routing tables), AF_KEY (new, for encryption) ...
ARP Spoofing Prevention ................................44
... D-Link wireless products are based on industry standards to provide high-speed wireless connectivity that is easy to use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the ...
... D-Link wireless products are based on industry standards to provide high-speed wireless connectivity that is easy to use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the ...
5620 SAM SERVICE AWARE MANAGER 14.0 R7 System
... The number of allowed 5620 SAM client sessions on a client delegate server is configurable as a threshold using the 5620 SAM GUI. If a user tries to open a client session that reaches or exceeds the threshold, the session proceeds and the client delegate server raises an alarm. This threshold-crossi ...
... The number of allowed 5620 SAM client sessions on a client delegate server is configurable as a threshold using the 5620 SAM GUI. If a user tries to open a client session that reaches or exceeds the threshold, the session proceeds and the client delegate server raises an alarm. This threshold-crossi ...
Network Protocols Pre.
... 12:02:18.257282 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@1472+) 12:02:18.258498 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@2944+) 12:02:18.258502 IP dhcp-19-115.engr.scu.edu.137 > 129.210.19.255.137: udp 50 12:02:18.259714 IP dhcp-19-211.engr ...
... 12:02:18.257282 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@1472+) 12:02:18.258498 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@2944+) 12:02:18.258502 IP dhcp-19-115.engr.scu.edu.137 > 129.210.19.255.137: udp 50 12:02:18.259714 IP dhcp-19-211.engr ...
COEN 252 Computer Forensics
... 12:02:18.257282 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@1472+) 12:02:18.258498 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@2944+) 12:02:18.258502 IP dhcp-19-115.engr.scu.edu.137 > 129.210.19.255.137: udp 50 12:02:18.259714 IP dhcp-19-211.engr ...
... 12:02:18.257282 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@1472+) 12:02:18.258498 IP dhcp-19-211.engr.scu.edu > Bobadilla.scu.edu: icmp (frag 10712:1472@2944+) 12:02:18.258502 IP dhcp-19-115.engr.scu.edu.137 > 129.210.19.255.137: udp 50 12:02:18.259714 IP dhcp-19-211.engr ...
User`s Manual
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
Ch 8 Lab B
... Modify check box is checked. This option allows CCP to modify the firewall on S0/0/1 to allow IPsec VPN traffic to reach the internal LAN. Click OK to continue. ...
... Modify check box is checked. This option allows CCP to modify the firewall on S0/0/1 to allow IPsec VPN traffic to reach the internal LAN. Click OK to continue. ...