Chapter 7 Lecture Presentation
... set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE Optional: congestion control, segmentation & reassembly, security ...
... set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE Optional: congestion control, segmentation & reassembly, security ...
Packet-Switching Networks
... set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE Optional: congestion control, segmentation & reassembly, security ...
... set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE Optional: congestion control, segmentation & reassembly, security ...
Chap 18 - The University of Tulsa
... In a connection-oriented service (also called virtualcircuit approach), there is a relationship between all packets belonging to a message. ...
... In a connection-oriented service (also called virtualcircuit approach), there is a relationship between all packets belonging to a message. ...
Traffic Engineering in IP over Optical Area Environments
... Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Catalan R&A Network, October 2004, 25-31 ............. 12 Figure 5: ASON Reference network model............................................ ...
... Figure 3: Weekly incoming/outgoing traffic from the Catalan R&A Network, November 2004, 8-15 ........... 12 Figure 4: Weekly incoming/outgoing traffic from the Catalan R&A Network, October 2004, 25-31 ............. 12 Figure 5: ASON Reference network model............................................ ...
Firewall
... consist of a pair of filtering routers and one or more proxy servers running on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to break security (IP address spoofing, source routing, packet fragments), while ...
... consist of a pair of filtering routers and one or more proxy servers running on one or more bastion hosts, all connected to a small, dedicated LAN between the two routers. The external router blocks attacks that use IP to break security (IP address spoofing, source routing, packet fragments), while ...
product catalog 02-17 v1 - SM
... infrastructure, the activities to be carried out will depend on the network state, the products deployed, type of services running and new services to be introduced. The first step is to consolidate the existing infrstructure resulting in a solid transport network to base the future innovation on. M ...
... infrastructure, the activities to be carried out will depend on the network state, the products deployed, type of services running and new services to be introduced. The first step is to consolidate the existing infrstructure resulting in a solid transport network to base the future innovation on. M ...
artially Connected Operation
... For example, even though AFS [Howard 1988] caches aggressively and has good support for low-speed networking in the transport protocol [Bachmann et al. 19941, the latency that accompanies many operations can make AFS over a low-speed network a trying experience. This affects user satisfaction when i ...
... For example, even though AFS [Howard 1988] caches aggressively and has good support for low-speed networking in the transport protocol [Bachmann et al. 19941, the latency that accompanies many operations can make AFS over a low-speed network a trying experience. This affects user satisfaction when i ...
The Effect of Different Queuing Regimes on a Switched Ethernet
... equal priority) can also be investigated. These two special cases are important for two reasons: With many different types of traffic streams potentially being transported through the fronthaul, there may be cases where two streams have equal (or approximately equal) weight definitions. Additionally ...
... equal priority) can also be investigated. These two special cases are important for two reasons: With many different types of traffic streams potentially being transported through the fronthaul, there may be cases where two streams have equal (or approximately equal) weight definitions. Additionally ...
IMS Presentation
... • Selects the MGCF in the network in which the interworking with PSTN/CS domain is to occur and forwards the SIP signalling to that MGCF. ...
... • Selects the MGCF in the network in which the interworking with PSTN/CS domain is to occur and forwards the SIP signalling to that MGCF. ...
trial_lecture
... • 4G network: Universal wireless access with much higher data rates than today ”Anytime, Anywhere” ...
... • 4G network: Universal wireless access with much higher data rates than today ”Anytime, Anywhere” ...
PDF file - The Open University of Hong Kong
... Computers have been connected to the Internet since the 1970s, and data exchange between networked computers has been around for just as long. However, the launch of the World Wide Web in the early 1990s offered the prospect of something totally new. It allowed the entire Internet to be viewed as a ...
... Computers have been connected to the Internet since the 1970s, and data exchange between networked computers has been around for just as long. However, the launch of the World Wide Web in the early 1990s offered the prospect of something totally new. It allowed the entire Internet to be viewed as a ...
A(t)
... The links are assumed to be expensive and scarce. Packet switching allows many, bursty flows to share the same link efficiently. “Circuit switching is rarely used for data networks, ... because of very inefficient use of the links” - Gallager ...
... The links are assumed to be expensive and scarce. Packet switching allows many, bursty flows to share the same link efficiently. “Circuit switching is rarely used for data networks, ... because of very inefficient use of the links” - Gallager ...
semestr 3 - final
... VLANs can not be deleted until all ports have been removed from the VLAN assignment. VLANs can only be deleted by the user that created them. VLAN 1 can not be deleted until another VLAN has been assigned its duties. *** VLAN1 is the management VLAN by default and can not be deleted. The command was ...
... VLANs can not be deleted until all ports have been removed from the VLAN assignment. VLANs can only be deleted by the user that created them. VLAN 1 can not be deleted until another VLAN has been assigned its duties. *** VLAN1 is the management VLAN by default and can not be deleted. The command was ...
nsa08 - Princeton University
... consistent with all link load statistics – Tomo-gravity: find the tomography solution that is closest to the output of the gravity model ...
... consistent with all link load statistics – Tomo-gravity: find the tomography solution that is closest to the output of the gravity model ...
ppt - Course Website Directory
... each new LSA packet sent. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against these pairs. If the received packet is new, it is forwarded on all the links except the one it arrived on. (Thus old LSA packets are dropped) Th ...
... each new LSA packet sent. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against these pairs. If the received packet is new, it is forwarded on all the links except the one it arrived on. (Thus old LSA packets are dropped) Th ...
r for A Building
... Korea and South Korea- In this case, it refers to a screened-subnet where semi-trusted net-visible servers are placed. ...
... Korea and South Korea- In this case, it refers to a screened-subnet where semi-trusted net-visible servers are placed. ...
Latest Developments in the IETF Routing Area
... Some functions are easier to achieve than others! Starting with simple use cases that can be achieved easily and ...
... Some functions are easier to achieve than others! Starting with simple use cases that can be achieved easily and ...
Source Routing
... Some functions are easier to achieve than others! Starting with simple use cases that can be achieved easily and ...
... Some functions are easier to achieve than others! Starting with simple use cases that can be achieved easily and ...
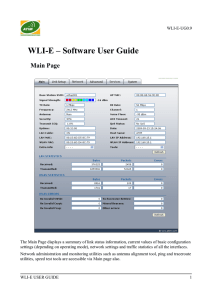
WLI-E – Software User Guide
... of LAN (Ethernet) interface. This statistics represents the total amount of data and packets transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while address ...
... of LAN (Ethernet) interface. This statistics represents the total amount of data and packets transferred between devices through the Ethernet interface either way. Both unicast IP traffic (conversations between two hosts using HTTP, SMTP, SSH and other protocols) and broadcast traffic (while address ...
Evaluating Design Approaches For Smart Building Systems
... communication bandwidth and memory. Questions such as; which communication protocol is more energy efficient, needs less overhead and is more feasible, need to be answered. We present two different approaches using different communication schemes. The main aim of both approaches remains the same; to ...
... communication bandwidth and memory. Questions such as; which communication protocol is more energy efficient, needs less overhead and is more feasible, need to be answered. We present two different approaches using different communication schemes. The main aim of both approaches remains the same; to ...
Dan's slide set
... • Receive window can’t slide if receiving process isn’t ready to read from buffer • Send advertised window size with ACK – Sender limits send window size based on advertised window size ...
... • Receive window can’t slide if receiving process isn’t ready to read from buffer • Send advertised window size with ACK – Sender limits send window size based on advertised window size ...
Securing Cyber Space: Safeguarding Access to Critical Resources Peter Hager, CEO
... We have found applications transmitting USERID and PASSWORD as User Data, of which many of them were of privileged users / administrators. In a conference call, network team assured that this was just inside their own network. Closer analysis of recordings revealed that USERIDs and PASSWORDs were di ...
... We have found applications transmitting USERID and PASSWORD as User Data, of which many of them were of privileged users / administrators. In a conference call, network team assured that this was just inside their own network. Closer analysis of recordings revealed that USERIDs and PASSWORDs were di ...