Benefits of an Implementation of H-P2PSIP
... to manage an additional overlay routing table in addition to the regular that peers use to perform queries inside their own domain. The forwarding of queries implies a higher load in terms of CPU and bandwidth consumption in super-peers. An open issue is the management of super-peers. H-P2PSIP suits ...
... to manage an additional overlay routing table in addition to the regular that peers use to perform queries inside their own domain. The forwarding of queries implies a higher load in terms of CPU and bandwidth consumption in super-peers. An open issue is the management of super-peers. H-P2PSIP suits ...
Using Spamhaus BGPf in a production environment
... In 2012, Spamhaus launched a new service to protect internet users from cyber threats and crime being committed through these threats by using so-called Trojan horses - the Spamhaus BGP feed (BGPf ). In the past year, Spamhaus was able to identify thousands of malicious server operated by cybercrimi ...
... In 2012, Spamhaus launched a new service to protect internet users from cyber threats and crime being committed through these threats by using so-called Trojan horses - the Spamhaus BGP feed (BGPf ). In the past year, Spamhaus was able to identify thousands of malicious server operated by cybercrimi ...
Node 1 `s Topology Table
... – Requires explicit acknowledgement for each packet sent reliably – RTP builds transmission list for each neighbor and retransmits up to 16 times or until hold time expires ...
... – Requires explicit acknowledgement for each packet sent reliably – RTP builds transmission list for each neighbor and retransmits up to 16 times or until hold time expires ...
ppt - UW Courses Web Server
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
Primitives for Active Internet Topology Mapping
... Figure 1(a) shows the cumulative fraction of path pairs in Ark and iPlane as a function of ED. The ED is larger for the randomly selected traceroute path pairs than the pairs from within the same BGP prefix, as determined by a contemporaneous Routeviews [21] BGP routing table. Approximately 60% of tr ...
... Figure 1(a) shows the cumulative fraction of path pairs in Ark and iPlane as a function of ED. The ED is larger for the randomly selected traceroute path pairs than the pairs from within the same BGP prefix, as determined by a contemporaneous Routeviews [21] BGP routing table. Approximately 60% of tr ...
Network Layer
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for us ...
GPRS - School of Electrical and Computer Engineering at Georgia
... switch interworks with other networks Serving GPRS support node = packet switch with mobility management capabilities GPRS makes use of existing GSM base stations ...
... switch interworks with other networks Serving GPRS support node = packet switch with mobility management capabilities GPRS makes use of existing GSM base stations ...
Networks
... Generally, TCP/IP (Transmission Control Protocol/Internet Protocol) is described using three to five functional layers. We have chosen the common DoD reference model, which is also known as the Internet reference model. • Process/Application Layer consists of applications and processes that use the ...
... Generally, TCP/IP (Transmission Control Protocol/Internet Protocol) is described using three to five functional layers. We have chosen the common DoD reference model, which is also known as the Internet reference model. • Process/Application Layer consists of applications and processes that use the ...
Chapter_4
... analogous to TCP/UDP connecton-oriented / connectionless transport-layer services, but: service: host-to-host no choice: network provides one or the other implementation: in network core ...
... analogous to TCP/UDP connecton-oriented / connectionless transport-layer services, but: service: host-to-host no choice: network provides one or the other implementation: in network core ...
Information for Work-in-Progress version:This document is subject to
... Implementation of certain elements of this standard or proposed standard may be subject to third party patent rights, including provisional patent rights (herein "patent rights"). DMTF makes no representations to users of the standard as to the existence of such rights, and is not responsible to rec ...
... Implementation of certain elements of this standard or proposed standard may be subject to third party patent rights, including provisional patent rights (herein "patent rights"). DMTF makes no representations to users of the standard as to the existence of such rights, and is not responsible to rec ...
PSN Compliance - East Midlands Councils
... Funding has been obtained from the Yorkshire and Humber RIEP to develop the business case. Project Director appointed to lead the project. Workshops have been held across the region to brief Local Authorities and Health. There is also strong interest across the Police and other Blue Light services. ...
... Funding has been obtained from the Yorkshire and Humber RIEP to develop the business case. Project Director appointed to lead the project. Workshops have been held across the region to brief Local Authorities and Health. There is also strong interest across the Police and other Blue Light services. ...
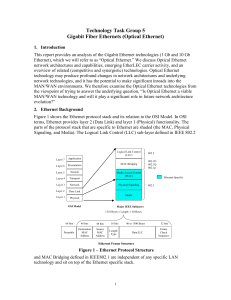
Gigabit Fiber Ethernets (Optical Ethernet)
... being no admission control, except policing of aggregate traffic streams at the network edge. As long as Ethernet technology has a significant cost advantage, it can afford to be somewhat inefficient in its bandwidth usage in order to ensure QoS. However, as the cost differences close, some increase ...
... being no admission control, except policing of aggregate traffic streams at the network edge. As long as Ethernet technology has a significant cost advantage, it can afford to be somewhat inefficient in its bandwidth usage in order to ensure QoS. However, as the cost differences close, some increase ...
Chapter 7
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
telecommunication and information networks the network services
... voice conversation for Internet subscribers with subscribers of telephone network of land phones common usage. – Usability. Skype-client is easy to be set up/fixed/download. Except subscriber’s name choosing, no one else configuration is needed. Unlike programs based on SIP (used, for example by Vo ...
... voice conversation for Internet subscribers with subscribers of telephone network of land phones common usage. – Usability. Skype-client is easy to be set up/fixed/download. Except subscriber’s name choosing, no one else configuration is needed. Unlike programs based on SIP (used, for example by Vo ...
LevelOne WAP-6110 300Mbps Wireless PoE
... Gateway. You will now be able to access the Internet using your high-speed xDSL/Cable modem connection. This User Guide will show you how to connect your Wireless Gateway, and how to customize its configuration to get the most out of your new product. ...
... Gateway. You will now be able to access the Internet using your high-speed xDSL/Cable modem connection. This User Guide will show you how to connect your Wireless Gateway, and how to customize its configuration to get the most out of your new product. ...
Juniper Networks Presentation Template-EMEA
... A Best Effort Experience is achieved by transporting voice over IP networks without special treatment • All packets delivered according to equal prioritization router queuing throughout network Best effort engineered networks require over-provisioning to account for peak traffic bursts associate ...
... A Best Effort Experience is achieved by transporting voice over IP networks without special treatment • All packets delivered according to equal prioritization router queuing throughout network Best effort engineered networks require over-provisioning to account for peak traffic bursts associate ...
Chp7
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
Security in Computer Networks
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
Lecture note 7
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
... Stored streaming: media stored at source transmitted to client streaming: client playout begins before all data has arrived timing constraint for still-to-be ...
Chapter 7 outline
... application-layer header added to each chunk. chunk+header encapsulated into UDP segment. application sends UDP segment into socket every ...
... application-layer header added to each chunk. chunk+header encapsulated into UDP segment. application sends UDP segment into socket every ...
A Security Model for VoIP Steganography
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
Document
... Figure 2.20 shows an example of transport layer communication. Data coming from the upperlayers have port addresses j and k ( j is the address of the sending process, and k is the address of the receiving process). Since the data size is larger than the network layer can handle, the data are split i ...
... Figure 2.20 shows an example of transport layer communication. Data coming from the upperlayers have port addresses j and k ( j is the address of the sending process, and k is the address of the receiving process). Since the data size is larger than the network layer can handle, the data are split i ...
A Security Model for VoIP Steganography
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
... • Use checksum to verify which frame has steganogram. • Must have special hardware which do not discard the frame with wrong checksum. • Very fast(200 Kbs/sec) • Detect: – There are too many corrupted frame. – Detect the differences between the dropped and retransmitted frames. ...
slides
... analogous to TCP/UDP connecton-oriented / connectionless transport-layer services, but: service: host-to-host no choice: network provides one or the other implementation: in network core ...
... analogous to TCP/UDP connecton-oriented / connectionless transport-layer services, but: service: host-to-host no choice: network provides one or the other implementation: in network core ...