ViaSat LinkWay S2 Broadband VSAT System
... provide quasi-error free communications with minimal carrier power requirements and maximum efficiency. The newly added 8PSK modulation feature provides dramatically improved spectral efficiency, while the inclusion of BPSK modulation offers support for ultra-small, sub 1-meter antennas for fixed, a ...
... provide quasi-error free communications with minimal carrier power requirements and maximum efficiency. The newly added 8PSK modulation feature provides dramatically improved spectral efficiency, while the inclusion of BPSK modulation offers support for ultra-small, sub 1-meter antennas for fixed, a ...
Chapter1-Intro - Communications Systems Center (CSC)
... 1.3 Network core Network access and physical media Internet structure and ISPs 1.4 Delay & loss in packet-switched networks 1.5 Protocol layers, service models ...
... 1.3 Network core Network access and physical media Internet structure and ISPs 1.4 Delay & loss in packet-switched networks 1.5 Protocol layers, service models ...
02-design
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
... • Yes, but only to improve performance • If network is highly unreliable • Adding some level of reliability helps performance, not correctness • Don’t try to achieve perfect reliability! • Implementing a functionality at a lower level should have minimum performance impact on the applications that d ...
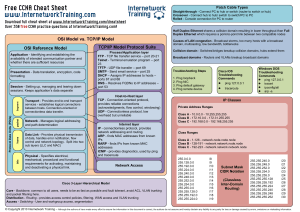
CCNA cheat sheet - Internetwork Training
... Application - Identifying and establishing the availability of intended communication partner and whether there are sufficient resources Presentation - Data translation, encryption, code formatting ...
... Application - Identifying and establishing the availability of intended communication partner and whether there are sufficient resources Presentation - Data translation, encryption, code formatting ...
ACCESS NETWORKING - CERN Computing Seminars
... • QOS is a measure of how quickly and reliably the data is transferred from source to the destination. (data : Time sensitive financial transactions, still images, larger data files, voice, video) • How to quantify and measure QOS • Each service may require different types of QOS • Subscriber Lease ...
... • QOS is a measure of how quickly and reliably the data is transferred from source to the destination. (data : Time sensitive financial transactions, still images, larger data files, voice, video) • How to quantify and measure QOS • Each service may require different types of QOS • Subscriber Lease ...
Network Neutrality: A Survey of the Economic Literature
... Roughly speaking, network neutrality refers to the principle that all data packets on an information network are treated equally. While the Internet had traditionally functioned more or less according to this principle, recent technological and legal developments have opened up the possibility for n ...
... Roughly speaking, network neutrality refers to the principle that all data packets on an information network are treated equally. While the Internet had traditionally functioned more or less according to this principle, recent technological and legal developments have opened up the possibility for n ...
End-to-end arguments: The Internet and beyond David P. Reed
... technique for the multiplexed utilization of existing interconnected networks. ... the top level assumption was that the top layer of interconnection would be provided by a layer of Internet packet switches, which were called gateways” Clark, Reed, Pogran, An Introduction to Local Area Networks. “Th ...
... technique for the multiplexed utilization of existing interconnected networks. ... the top level assumption was that the top layer of interconnection would be provided by a layer of Internet packet switches, which were called gateways” Clark, Reed, Pogran, An Introduction to Local Area Networks. “Th ...
Why Fiber Optic?
... Value added “service” Economic Development tool More/better broadband service potential in an emerging global economy • Foster competition among providers ...
... Value added “service” Economic Development tool More/better broadband service potential in an emerging global economy • Foster competition among providers ...
Computer Networks & The Internet
... • It is owned by everyone. • It is the key platform for all kinds of services like entertainment, business etc. • It evolved from ARPANET – a research network developed by United States Defense Department in 1969. Initially created to help academic and government researchers to use e-mail and share ...
... • It is owned by everyone. • It is the key platform for all kinds of services like entertainment, business etc. • It evolved from ARPANET – a research network developed by United States Defense Department in 1969. Initially created to help academic and government researchers to use e-mail and share ...
Slideshow - VCE IT Lecture Notes
... limited coverage; can be black spots with no signal. • Uses same technology as mobile phone internet connection ...
... limited coverage; can be black spots with no signal. • Uses same technology as mobile phone internet connection ...
eCommerce – Workshop #1
... • e-B infrastructure: H/W, S/W & its architecture necessary to achieve electronic information exchange within an organization or with its partners. • Coverage: – Technical infrastructure • Net • How this work – Communication standard: TCP/IP, EDI – Publishing standard: HTML, XML – Management issue • ...
... • e-B infrastructure: H/W, S/W & its architecture necessary to achieve electronic information exchange within an organization or with its partners. • Coverage: – Technical infrastructure • Net • How this work – Communication standard: TCP/IP, EDI – Publishing standard: HTML, XML – Management issue • ...
IP Convergence
... pricing based on cost of supply, not value of service service delivery skill specialization service innovation continuous industry response to meet current user needs ...
... pricing based on cost of supply, not value of service service delivery skill specialization service innovation continuous industry response to meet current user needs ...
Internet Protocol, IP Addressing and Datagrams
... smaller fragments • Each datagram contains a fragment • Header fields indicate when the data is a fragment and also where it belongs MTUs for Some Networks ...
... smaller fragments • Each datagram contains a fragment • Header fields indicate when the data is a fragment and also where it belongs MTUs for Some Networks ...
Event Based Routing In Delay Tolerant Networks
... This information would enable each router to estimate the number of matching subscribers that are expected to be reached (directly or through other routers) in the next Tx time Units, given an event E. These statistics are used for several important purposes such as: • deciding whether it is feasibl ...
... This information would enable each router to estimate the number of matching subscribers that are expected to be reached (directly or through other routers) in the next Tx time Units, given an event E. These statistics are used for several important purposes such as: • deciding whether it is feasibl ...
Network Layer (Congestion and QoS)
... - There is a setup phase, this cases delay in starting data flow. - Routers need to maintain per-flow state. This approach is flow-based and not very scalable. - Complex router-to-router exchange of flow information. A simpler and approach was then designed by the IETF called, Differentiated Service ...
... - There is a setup phase, this cases delay in starting data flow. - Routers need to maintain per-flow state. This approach is flow-based and not very scalable. - Complex router-to-router exchange of flow information. A simpler and approach was then designed by the IETF called, Differentiated Service ...
15-441 Computer Networking Lecture 2 - Protocol Stacks
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
Networking
... • Adobe PDF reader used to deliver malicious payloads which evade malware and intrusion detection software, prior to version 9. • Linksys/Cisco “Moon” worm connects to port 8080, loads a worm 2MB in size, scans for 670 different networks, try to infect other systems, new code for fix, disable remote ...
... • Adobe PDF reader used to deliver malicious payloads which evade malware and intrusion detection software, prior to version 9. • Linksys/Cisco “Moon” worm connects to port 8080, loads a worm 2MB in size, scans for 670 different networks, try to infect other systems, new code for fix, disable remote ...
How Others Compromise Your Location Privacy
... • Users reveal their locations to Location-Based Services (LBS) in exchange for context-aware services • Non-LBS service providers rely on IP – location • i.e., determining a location from an IP address ...
... • Users reveal their locations to Location-Based Services (LBS) in exchange for context-aware services • Non-LBS service providers rely on IP – location • i.e., determining a location from an IP address ...
CIMARRON TELEPHONE COMPANY BROADBAND
... video chat applications, gaming, and Internet video. If users or developers have questions about particular real-time applications, please contact us at [email protected]. Specialized Services. Specialized services offered to end users. We offer several managed services over our network, sharing netw ...
... video chat applications, gaming, and Internet video. If users or developers have questions about particular real-time applications, please contact us at [email protected]. Specialized Services. Specialized services offered to end users. We offer several managed services over our network, sharing netw ...
chapter1
... • NET1, NET2, . . ., NETn are network protocols, usually implemented by a combination of hardware (e.g., a network adapter) and software (e.g., a device driver). ...
... • NET1, NET2, . . ., NETn are network protocols, usually implemented by a combination of hardware (e.g., a network adapter) and software (e.g., a device driver). ...
Slaid_05 - narod.ru
... 1. Domain. Every country is assigned a certain code marking two-three Latin letters long, which is called first level domain. If the address ends with letters "ru", then corresponding site is situated in the Russia’s domain. There are also first level domains, which are related not with geography, b ...
... 1. Domain. Every country is assigned a certain code marking two-three Latin letters long, which is called first level domain. If the address ends with letters "ru", then corresponding site is situated in the Russia’s domain. There are also first level domains, which are related not with geography, b ...
Using a Single IPv4 Global Address in DSTM
... – WiBro (Wireless Broadband), Korea effort is also based on the ...
... – WiBro (Wireless Broadband), Korea effort is also based on the ...
No Slide Title - Institute of Technology Sligo
... The overall goal of WAN design is to minimize cost based on these elements while delivering service that does not compromise established availability requirements. The first step in the design process is to understand the business requirements. The chief components of application availability are re ...
... The overall goal of WAN design is to minimize cost based on these elements while delivering service that does not compromise established availability requirements. The first step in the design process is to understand the business requirements. The chief components of application availability are re ...
Visualisation and Analysis of Real Time Application Behaviour in a
... • Demand for real time applications is increasing • Network simulation is the most efficient means of developing and testing new protocols and network schemes • Evaluation of the behaviour of real time applications would benefit from an ability to assess the “quality of reproduction” when subjected ...
... • Demand for real time applications is increasing • Network simulation is the most efficient means of developing and testing new protocols and network schemes • Evaluation of the behaviour of real time applications would benefit from an ability to assess the “quality of reproduction” when subjected ...
3-4-1_QoS Intro adap..
... – PCF -> Hybrid CF (HCF): can “poll” nodes also in contention free period • 802.11e is mainly directed to infrastucture LANs • In ad hoc, multihop network one can use some of the EDCF features • Another problem in ad hoc nets is the simultaneous scheduling of multiple transmissions (spatial reuse) • ...
... – PCF -> Hybrid CF (HCF): can “poll” nodes also in contention free period • 802.11e is mainly directed to infrastucture LANs • In ad hoc, multihop network one can use some of the EDCF features • Another problem in ad hoc nets is the simultaneous scheduling of multiple transmissions (spatial reuse) • ...