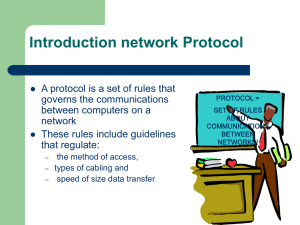
Networking and Internetworking
... whereas the latency is determined primarily by software overheads, routing delays and delay of accessing to transmission channels – In distributed systems, messages are always small in size, so the latency is more significant than data transfer rate – total system bandwidth : the total volume of tra ...
... whereas the latency is determined primarily by software overheads, routing delays and delay of accessing to transmission channels – In distributed systems, messages are always small in size, so the latency is more significant than data transfer rate – total system bandwidth : the total volume of tra ...
Latihan Pertemuan 5 (Network Defenses) Subnetting . splits the
... 2. A virtual LAN (VLAN) allows devices to be grouped _____________. A. logically B. based on subnets C. only around core switches D. directly to routers 3. Convergence combines voice, data, and video traffic ____________. A. over a single IP network B. through hubs C. one stream at a time D. only on ...
... 2. A virtual LAN (VLAN) allows devices to be grouped _____________. A. logically B. based on subnets C. only around core switches D. directly to routers 3. Convergence combines voice, data, and video traffic ____________. A. over a single IP network B. through hubs C. one stream at a time D. only on ...
csci5211: Computer Networks and Data Communications
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
csci5211: Computer Networks and Data Communications
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
... According to [Saltzer84]: “…sometimes an incomplete version of the function provided by the communication system (lower levels) may be useful as a performance enhancement…” ...
internet_and_WWW
... • The World Wide Web is an information service that uses the Internet as its communication medium • It is based on the technology called hypertext • Hypertext is a method of presenting information • Selected words in a text can be "expanded" – to provide other information about the word – These word ...
... • The World Wide Web is an information service that uses the Internet as its communication medium • It is based on the technology called hypertext • Hypertext is a method of presenting information • Selected words in a text can be "expanded" – to provide other information about the word – These word ...
TDMoIP - dspcsp
... so this issue is orthogonal to that of the previous slides RTP can be used to transport timing across IP networks It does this by providing: a 16 bit sequence number 1 32 bit timestamp at the expense of 12 additional overhead bytes per packet Accurate timing is important in telephony and IP netw ...
... so this issue is orthogonal to that of the previous slides RTP can be used to transport timing across IP networks It does this by providing: a 16 bit sequence number 1 32 bit timestamp at the expense of 12 additional overhead bytes per packet Accurate timing is important in telephony and IP netw ...
Document
... allows their employees to exchange files, hence freeing the company up from maintaining a network for this purpose. ...
... allows their employees to exchange files, hence freeing the company up from maintaining a network for this purpose. ...
Reading Organizer Instructor Version
... A form of information theft where personal information is stolen for the purpose of takeing over someone’s identity. Using this information an individual can obtain legal documents, apply for credit and make unauthorized online purchases. Idnetity theft is a growing problem costing billions of dolla ...
... A form of information theft where personal information is stolen for the purpose of takeing over someone’s identity. Using this information an individual can obtain legal documents, apply for credit and make unauthorized online purchases. Idnetity theft is a growing problem costing billions of dolla ...
CS 105 - HMC Computer Science
... service in the United States Congress, I took the initiative in creating the Internet” Fact: Dave Farber, Vint Cerf, and Bob Metcalfe have all supported the statement Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial on ...
... service in the United States Congress, I took the initiative in creating the Internet” Fact: Dave Farber, Vint Cerf, and Bob Metcalfe have all supported the statement Fact: Al Gore introduced and supported many bills funding the shift from a primarily US research network to a worldwide commercial on ...
Lesson 7
... Packet Filtering – Also called packet screening: decide to allow or reject specific packets as they enter your network Stateful Inspection – looks at contents of packet not just header Application Level Gateway -- also known as proxy gateways, used to forward service-specific traffic (e.g. email). – ...
... Packet Filtering – Also called packet screening: decide to allow or reject specific packets as they enter your network Stateful Inspection – looks at contents of packet not just header Application Level Gateway -- also known as proxy gateways, used to forward service-specific traffic (e.g. email). – ...
best-effort service!
... • The capability to control traffic handling mechanisms in the network such that the network meets the service needs of certain applications and users subject to network policies. • Applications – Elastic (delay-tolerant) • Tolerate delays and losses • Can adapt to congestion ...
... • The capability to control traffic handling mechanisms in the network such that the network meets the service needs of certain applications and users subject to network policies. • Applications – Elastic (delay-tolerant) • Tolerate delays and losses • Can adapt to congestion ...
Review Questions
... 2. A virtual LAN (VLAN) allows devices to be grouped _____________. A. logically B. based on subnets C. only around core switches D. directly to routers 3. Convergence combines voice, data, and video traffic ____________. A. over a single IP network B. through hubs C. one stream at a time D. only on ...
... 2. A virtual LAN (VLAN) allows devices to be grouped _____________. A. logically B. based on subnets C. only around core switches D. directly to routers 3. Convergence combines voice, data, and video traffic ____________. A. over a single IP network B. through hubs C. one stream at a time D. only on ...
NEMO-Enabled Localized Mobility Support for Internet
... N-PMIPv6 Architecture • The key idea of N-PMIPv6 consists in extending the PMIPv6 domain to also include mobile networks. – Both the fixed infrastructure (i.e., MAGs) and the mobile networks (i.e., MRs=mMAGs) belong to the same network operator. • MRs require functionality to extend the PMIPv6 doma ...
... N-PMIPv6 Architecture • The key idea of N-PMIPv6 consists in extending the PMIPv6 domain to also include mobile networks. – Both the fixed infrastructure (i.e., MAGs) and the mobile networks (i.e., MRs=mMAGs) belong to the same network operator. • MRs require functionality to extend the PMIPv6 doma ...
pdf
... network bandwidth consumed only when sending packets are routed independently packetizing may reduce delays (using parallelism) ...
... network bandwidth consumed only when sending packets are routed independently packetizing may reduce delays (using parallelism) ...
CS 105 - HMC Computer Science
... Well-known port: Associated with some service provided by a server (e.g., port 80 is associated with Web servers) ...
... Well-known port: Associated with some service provided by a server (e.g., port 80 is associated with Web servers) ...
Lecture4_Networking_..
... Some require short packets others require longer packets E.g. satellite – longer packets Local LAN – shorter packets ...
... Some require short packets others require longer packets E.g. satellite – longer packets Local LAN – shorter packets ...
No Slide Title - Ed Lazowska
... Using TCP/IP and lower layers, we can get multipacket messages delivered reliably from address space A on machine B to address space C on machine D, where machines B and D are many heterogeneous network hops apart, without knowing any of the ...
... Using TCP/IP and lower layers, we can get multipacket messages delivered reliably from address space A on machine B to address space C on machine D, where machines B and D are many heterogeneous network hops apart, without knowing any of the ...
Presentation
... Maintenance, Backups and Software Updates can all be done much more cost effectively from the central administrative building. Schools are able to explore new high-end applications such as video conference & Voice over IP. ...
... Maintenance, Backups and Software Updates can all be done much more cost effectively from the central administrative building. Schools are able to explore new high-end applications such as video conference & Voice over IP. ...
Multimedia Data Streaming - Indian Institute of Science
... Receiver heterogeneity means that receivers have different or even varying latency requirements, visual quality requirements, and/or processing capability. ...
... Receiver heterogeneity means that receivers have different or even varying latency requirements, visual quality requirements, and/or processing capability. ...
Lecture #3
... = L/R, significant for low-speed links dprop = propagation delay a few microsecs to hundreds of msecs ...
... = L/R, significant for low-speed links dprop = propagation delay a few microsecs to hundreds of msecs ...
Defense - Northwestern Networks Group
... • The Bad: Datacenters are growing faster than commodity Ethernet devices • Our fat-tree solution • Is better: technically infeasible 27k node cluster using 10 ...
... • The Bad: Datacenters are growing faster than commodity Ethernet devices • Our fat-tree solution • Is better: technically infeasible 27k node cluster using 10 ...
Document
... GPRS or EDGE, but will in reality co-exist with them, and can share one common core network. ...
... GPRS or EDGE, but will in reality co-exist with them, and can share one common core network. ...