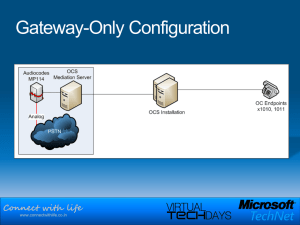
week8-1
... 4. NIC-A modulates the packet send out 5. After a while, NIC-1 will receive the m-carrier 6. NIC-1 demodulates the m-carrier and put the packet into a queue 7. P-S checks this packet and find destination is “C” 8. NIC-3 modulates the packet send out 9. After a while, NIC-C will receive the m-car ...
... 4. NIC-A modulates the packet send out 5. After a while, NIC-1 will receive the m-carrier 6. NIC-1 demodulates the m-carrier and put the packet into a queue 7. P-S checks this packet and find destination is “C” 8. NIC-3 modulates the packet send out 9. After a while, NIC-C will receive the m-car ...
Document
... • End systems and routers maintain routing tables — Indicate next router to which datagram should be sent — Static • May contain alternative routes ...
... • End systems and routers maintain routing tables — Indicate next router to which datagram should be sent — Static • May contain alternative routes ...
Connect with life
... Type of usage is important when planning Media Stack adjusts to available bandwidth every 5 seconds Consider the whole path end-to-end Connect with life www.connectwithlife.co.in ...
... Type of usage is important when planning Media Stack adjusts to available bandwidth every 5 seconds Consider the whole path end-to-end Connect with life www.connectwithlife.co.in ...
Chapter 07.ppt
... • Define the terms used when describing a network and its components • List the differences among circuitswitching, message-switching, packetswitching, and cell-switching networks • List the types of routing techniques used to move data through a network ...
... • Define the terms used when describing a network and its components • List the differences among circuitswitching, message-switching, packetswitching, and cell-switching networks • List the types of routing techniques used to move data through a network ...
Lecture3-wireless
... • Combination of Two Standards Groups – ZigBee Alliance: “an association of companies working together to enable reliable, costeffective, low-power, wirelessly networked, monitoring and control products based on an ...
... • Combination of Two Standards Groups – ZigBee Alliance: “an association of companies working together to enable reliable, costeffective, low-power, wirelessly networked, monitoring and control products based on an ...
Chp. 6 - Cisco Networking Academy
... The client uses the IP address of the DNS server configured in the DNS settings of the host's IP configuration. When the DNS server receives the request, it checks its table to determine the IP address associated with that web server. If the local DNS server does not have an entry for the requested ...
... The client uses the IP address of the DNS server configured in the DNS settings of the host's IP configuration. When the DNS server receives the request, it checks its table to determine the IP address associated with that web server. If the local DNS server does not have an entry for the requested ...
PDF
... Measurement and prediction of network resources are crucial so that adaptive applications can make use of Grid environments. Although a large number of systems and tools have been developed to provide such measurement services, the diversity of Grid resources and lack of central control prevent the ...
... Measurement and prediction of network resources are crucial so that adaptive applications can make use of Grid environments. Although a large number of systems and tools have been developed to provide such measurement services, the diversity of Grid resources and lack of central control prevent the ...
r02-review-transport..
... • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
... • No explicit feedback from network • Congestion inferred from end-system observed loss, delay • Approach taken by TCP ...
Measuring BGP - Geoff Huston
... deployment structure is more theoretic than real these days i.e. provider based route aggregation is leaking like a sieve! ...
... deployment structure is more theoretic than real these days i.e. provider based route aggregation is leaking like a sieve! ...
Network Connect - Juniper Networks
... Network Connect takes all traffic to and from the client and transmits over the secure Network Connect tunnel. The only exception is for traffic initiated by other IVE-enabled features, such as Web browsing, file browsing, and telnet/SSH. If you do not want to enable other IVE features for certain u ...
... Network Connect takes all traffic to and from the client and transmits over the secure Network Connect tunnel. The only exception is for traffic initiated by other IVE-enabled features, such as Web browsing, file browsing, and telnet/SSH. If you do not want to enable other IVE features for certain u ...
OSI
... in connection with IP and operates at the transport layer. IP is the set of convention used to pass packets from one host to another. ...
... in connection with IP and operates at the transport layer. IP is the set of convention used to pass packets from one host to another. ...
Firewall - theodoros christophides site
... – firewall designed to prevent outsiders from accessing sensitive data – many attacks would not need to use the firewall ...
... – firewall designed to prevent outsiders from accessing sensitive data – many attacks would not need to use the firewall ...
Overlay networks
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
Internet Routing Protocols
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
Service Clouds: A Distributed Infrastructure for Constructing Autonomic Communication Services
... paths between nodes enables intermediate processing of data streams, without modifying the underlying network protocols or router software. Designing systems involving both vertical and horizontal cooperation is challenging due to the dynamic nature of adaptive software, uncertainty in the execution ...
... paths between nodes enables intermediate processing of data streams, without modifying the underlying network protocols or router software. Designing systems involving both vertical and horizontal cooperation is challenging due to the dynamic nature of adaptive software, uncertainty in the execution ...
A Performance and Power Analysis of WK
... modularity, which in turn provides a standard interface for easier component reuse and better interoperability. Overall performance and scalability increase since the networking resources are shared. Scheduling of traffic on shared resources prevents latency increases on critical signals. Power effi ...
... modularity, which in turn provides a standard interface for easier component reuse and better interoperability. Overall performance and scalability increase since the networking resources are shared. Scheduling of traffic on shared resources prevents latency increases on critical signals. Power effi ...
netwoking - WordPress.com
... "header" with information necessary for routing the packet from source to destination. Each packet in a data stream is independent. The main advantage of packet-switching is that the packets from many different sources can share a line, allowing for very efficient use of the communication medium. Wi ...
... "header" with information necessary for routing the packet from source to destination. Each packet in a data stream is independent. The main advantage of packet-switching is that the packets from many different sources can share a line, allowing for very efficient use of the communication medium. Wi ...
Computer Network - GPW Morni, Panchkula
... single point of failure. However, this type of system would not be able to protect data in some cases, such as in accidental deletions. 26) What does 10Base-T mean? The 10 refers to the data transfer rate, in this case is 10Mbps. The word Base refers to base band, as oppose to broad band. T means tw ...
... single point of failure. However, this type of system would not be able to protect data in some cases, such as in accidental deletions. 26) What does 10Base-T mean? The 10 refers to the data transfer rate, in this case is 10Mbps. The word Base refers to base band, as oppose to broad band. T means tw ...
Chapter 1
... in order to be delivered to the correct destination. • The packet passes from exchange to exchange for delivery through the provider network. • Packet Switched describes the type of network in which relatively small units of data called packets are routed through a network based on the destination a ...
... in order to be delivered to the correct destination. • The packet passes from exchange to exchange for delivery through the provider network. • Packet Switched describes the type of network in which relatively small units of data called packets are routed through a network based on the destination a ...
CCNA4E_CH8_STUDY_GUIDE_KEY
... between remote locations. Consequently, higher bandwidth is crucial because it allows more data to be transmitted in a given time. When bandwidth is inadequate, competition ...
... between remote locations. Consequently, higher bandwidth is crucial because it allows more data to be transmitted in a given time. When bandwidth is inadequate, competition ...
II. Fast Cell Site Selection - Communications and signal processing
... Abstract—As mobile cellular networks evolve to carry both traditional voice and new data services, an all-IP based radio access network akin to the Internet is the most favorable approach for future radio access networks. The main characteristic of such an architecture is that a lot of the radio net ...
... Abstract—As mobile cellular networks evolve to carry both traditional voice and new data services, an all-IP based radio access network akin to the Internet is the most favorable approach for future radio access networks. The main characteristic of such an architecture is that a lot of the radio net ...
IP Basics
... Generally, TCP/IP (Transmission Control Protocol/Internet Protocol) is described using three to five functional layers. We have chosen the common DoD reference model, which is also known as the Internet reference model. • Process/Application Layer consists of applications and processes that use the ...
... Generally, TCP/IP (Transmission Control Protocol/Internet Protocol) is described using three to five functional layers. We have chosen the common DoD reference model, which is also known as the Internet reference model. • Process/Application Layer consists of applications and processes that use the ...