4th Edition: Chapter 1 - UF CISE
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 7), virtual circuit ...
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 7), virtual circuit ...
TCP Trunking
... Technical challenges • Lack of guarantees in terms of BW, packet loss, delay and jitter - Quality of Voice over Internet suffers. IP is only best effort!! ...
... Technical challenges • Lack of guarantees in terms of BW, packet loss, delay and jitter - Quality of Voice over Internet suffers. IP is only best effort!! ...
TN9210-TB2 - Tehuti Networks
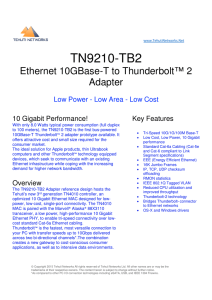
... The TN9210-TB2 Adapter reference design hosts the Tehuti's new 3rd generation TN4010 controller, an optimized 10 Gigabit Ethernet MAC designed for lowpower, low-cost, single-port connectivity. The TN4010 MAC is paired with the Marvell® Alaska® 88X3110 transceiver, a low power, high-performance 10 Gi ...
... The TN9210-TB2 Adapter reference design hosts the Tehuti's new 3rd generation TN4010 controller, an optimized 10 Gigabit Ethernet MAC designed for lowpower, low-cost, single-port connectivity. The TN4010 MAC is paired with the Marvell® Alaska® 88X3110 transceiver, a low power, high-performance 10 Gi ...
EECC694 - Shaaban
... • A variable “u” is associated by the router to reflect the recent utilization of an output line: u = auold + (1 - a) f • When “u” goes above a given threshold, the corresponding line enters a warning state. ...
... • A variable “u” is associated by the router to reflect the recent utilization of an output line: u = auold + (1 - a) f • When “u” goes above a given threshold, the corresponding line enters a warning state. ...
William Stallings Data and Computer Communications
... Sequence numbers set to zero Packets in transit lost Up to higher level protocol to recover lost packets Triggered by loss of packet, sequence number error, congestion, loss of network internal virtual circuit ...
... Sequence numbers set to zero Packets in transit lost Up to higher level protocol to recover lost packets Triggered by loss of packet, sequence number error, congestion, loss of network internal virtual circuit ...
PDF
... but significant performance reductions usually occur when new features are added or high scale is required. The IoE will consist of many different flows passing through the network, and those flows will have diverse feature requirements. The Cisco nPower X1, with 336 multi-threaded processor cores ( ...
... but significant performance reductions usually occur when new features are added or high scale is required. The IoE will consist of many different flows passing through the network, and those flows will have diverse feature requirements. The Cisco nPower X1, with 336 multi-threaded processor cores ( ...
PPT
... • Real-Time Interactive requirements on delay and its jitter have been satisfied by over-provisioning (providing plenty of bandwidth), what will happen when the load increases?... Lecture 20: 11/13/2001 ...
... • Real-Time Interactive requirements on delay and its jitter have been satisfied by over-provisioning (providing plenty of bandwidth), what will happen when the load increases?... Lecture 20: 11/13/2001 ...
Routing to the MEN`s edge TextStart Investment in Metro Ethernet
... below: High Speed Internet (HSI) generally presents a client-server traffic model. The traffic is carried by the Layer 2 pipe to the BRAS, where service intelligence features are implemented such as authentication, user/service identification, and service policy. Voice service media stream presents ...
... below: High Speed Internet (HSI) generally presents a client-server traffic model. The traffic is carried by the Layer 2 pipe to the BRAS, where service intelligence features are implemented such as authentication, user/service identification, and service policy. Voice service media stream presents ...
Document
... – Determines from a physical address (MAC address) which device a packet is intended for and switches it out toward that device ...
... – Determines from a physical address (MAC address) which device a packet is intended for and switches it out toward that device ...
Application Control
... Analyses the payload and the header information of an IP packet to detect different kind of intrusion attempts • Monitors inbound traffic • Inspects single packets only, not full stream or TCP/IP sequence • System alerts on 31 malicous packets; most common operating system fingerprinting attempts (n ...
... Analyses the payload and the header information of an IP packet to detect different kind of intrusion attempts • Monitors inbound traffic • Inspects single packets only, not full stream or TCP/IP sequence • System alerts on 31 malicous packets; most common operating system fingerprinting attempts (n ...
tech brief - Arrow ECS
... Let’s get a little closer to Extreme’s Policy-Based QoS: Intelligent bandwidth management makes it possible to control the latency and jitter of every packet stream passing through the BlackDiamond. That’s obviously good news for delay-sensitive apps like voice and video. But extending broadcast dom ...
... Let’s get a little closer to Extreme’s Policy-Based QoS: Intelligent bandwidth management makes it possible to control the latency and jitter of every packet stream passing through the BlackDiamond. That’s obviously good news for delay-sensitive apps like voice and video. But extending broadcast dom ...
The performance of circuit switching in the Internet
... response time, QoS, switch capacity, network architecture. Abstract -- This paper studies the performance of an Internet that uses circuit switching instead of, or in addition to, packet switching. On the face of it, this would seem a pointless exercise; the Internet is packet switched, and was deli ...
... response time, QoS, switch capacity, network architecture. Abstract -- This paper studies the performance of an Internet that uses circuit switching instead of, or in addition to, packet switching. On the face of it, this would seem a pointless exercise; the Internet is packet switched, and was deli ...
Congestion Control Outline: Queuing Discipline
... • How to fairly allocate resources (link bandwidths and switch buffers) among users. • Two sides of the same coin: – Resource allocation so as to avoid congestion (difficult with any precision) – Congestion control if (and when) it occurs ...
... • How to fairly allocate resources (link bandwidths and switch buffers) among users. • Two sides of the same coin: – Resource allocation so as to avoid congestion (difficult with any precision) – Congestion control if (and when) it occurs ...
Chapter 19 - William Stallings, Data and Computer
... no special treatment for high priority flow packets large packet can hold up smaller packets greedy connection can crowd out less greedy connection ...
... no special treatment for high priority flow packets large packet can hold up smaller packets greedy connection can crowd out less greedy connection ...
GIG Requirements for Internet Congestion Control
... • For inelastic traffic, a behavioral model to provide “Assured Inelastic Service” is fairly well understood • For the assured elastic service, the behavioral model described in RFC 1633 and elsewhere will need to be extended – Service Model for different elastic application types allows for differe ...
... • For inelastic traffic, a behavioral model to provide “Assured Inelastic Service” is fairly well understood • For the assured elastic service, the behavioral model described in RFC 1633 and elsewhere will need to be extended – Service Model for different elastic application types allows for differe ...
Testing Bandwidth around the world
... Connection Response-Time Analysis Analyze end-user response time of TCP connections by: • Connection setup time • Application processing time • Data transfer time ...
... Connection Response-Time Analysis Analyze end-user response time of TCP connections by: • Connection setup time • Application processing time • Data transfer time ...
- IEEE Mentor
... • Delay and Jitter sensitive • Reliable transmission is not supported (using UDP) • Not support silence suppression function ...
... • Delay and Jitter sensitive • Reliable transmission is not supported (using UDP) • Not support silence suppression function ...
Mobile IP Telephony: A solution to Rural Connectivity
... converted by a gateway to another format-either for interoperation with a different IP-based multimedia scheme or because the call is being placed onto the PSTN. An IP network does not have the same limitations as the traditional telephone system as far as routing is concerned. A circuit switched ne ...
... converted by a gateway to another format-either for interoperation with a different IP-based multimedia scheme or because the call is being placed onto the PSTN. An IP network does not have the same limitations as the traditional telephone system as far as routing is concerned. A circuit switched ne ...
Chapter 19 - William Stallings, Data and Computer
... no special treatment for high priority flow packets large packet can hold up smaller packets greedy connection can crowd out less greedy connection ...
... no special treatment for high priority flow packets large packet can hold up smaller packets greedy connection can crowd out less greedy connection ...
Storage Aware Protocols For heterogeneous networks
... • Use storage to delay data delivery while the network searches for “better” paths Better ϵ {Energy efficient, most storage, fastest, higher probability of success,…} ...
... • Use storage to delay data delivery while the network searches for “better” paths Better ϵ {Energy efficient, most storage, fastest, higher probability of success,…} ...
Performance Analysis of VoMAN using Routing Protocols to Improve
... H.323, etc., and media protocols include Real Time Transport Protocol (RTP), RTP Control Protocol (RTCP). These RTP packets are encapsulated into transport protocols to transmission over IP. UDP is the most preferable protocol for transferring voice over IP network. Quality of Service (QoS) is set o ...
... H.323, etc., and media protocols include Real Time Transport Protocol (RTP), RTP Control Protocol (RTCP). These RTP packets are encapsulated into transport protocols to transmission over IP. UDP is the most preferable protocol for transferring voice over IP network. Quality of Service (QoS) is set o ...
powerpoint - University of Houston
... indicator of performance with sharing – strong correlation between application traffic and performance with low bandwidth links – CPU utilization during normal execution a good indicator of performance with node sharing ...
... indicator of performance with sharing – strong correlation between application traffic and performance with low bandwidth links – CPU utilization during normal execution a good indicator of performance with node sharing ...
Week 1 - DePaul University
... Data formats Signal levels Semantics Control information for coordination Error handling Timing Speed matching (between sender and receiver) Sequencing (the right commands in the right order – closely related to semantics) ...
... Data formats Signal levels Semantics Control information for coordination Error handling Timing Speed matching (between sender and receiver) Sequencing (the right commands in the right order – closely related to semantics) ...