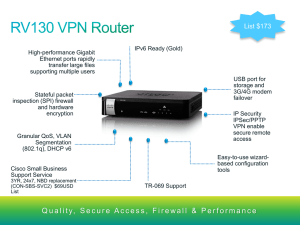
MPLS (Multi-Protocol Label Switching)
... Border Gateway Protocol (BGP) Resource Reservation Protocol (RSVP) ...
... Border Gateway Protocol (BGP) Resource Reservation Protocol (RSVP) ...
The QoSbox: A PC-Router for Quantitative Service Differentiation in IP Networks ∗
... Internet only consisted of network connections between a handful of universities. However, since the late 1980s, these conditions do not hold anymore, for two main reasons. Firstly, an increasing number of different applications, such as real-time video, peer-to-peer networking, or the World-Wide We ...
... Internet only consisted of network connections between a handful of universities. However, since the late 1980s, these conditions do not hold anymore, for two main reasons. Firstly, an increasing number of different applications, such as real-time video, peer-to-peer networking, or the World-Wide We ...
PDF Download(PDF Type,777kbytes)
... transmission speed and optical frequency bandwidth to support diversified services with different types of traffic, such as internet, enterprise line, and mobile services. We demonstrated the reliability of EλAN through a prototype testbed network which utilizes optical path provisioning and switchi ...
... transmission speed and optical frequency bandwidth to support diversified services with different types of traffic, such as internet, enterprise line, and mobile services. We demonstrated the reliability of EλAN through a prototype testbed network which utilizes optical path provisioning and switchi ...
Multimedia Service
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
I.Research of Underwater Wireless Sensor Network
... behavior of ants, swarm intelligence should be relied on and it can succeed through the individual pathfinding without the help of global information. This kind of algorithm is very suitable for the sensor due to its characteristics of strong dynamics, high reliability and strong expansion. This pap ...
... behavior of ants, swarm intelligence should be relied on and it can succeed through the individual pathfinding without the help of global information. This kind of algorithm is very suitable for the sensor due to its characteristics of strong dynamics, high reliability and strong expansion. This pap ...
NOT
... Proposal: General Description of the Mixed Mode Matrices In the new Touchstone format, the modes should be explicitly defined, by giving the voltage and current relationships with the single-ended modes The definition order determines the matrix storage, so the matrix data format is the same fo ...
... Proposal: General Description of the Mixed Mode Matrices In the new Touchstone format, the modes should be explicitly defined, by giving the voltage and current relationships with the single-ended modes The definition order determines the matrix storage, so the matrix data format is the same fo ...
PQ_Unit V
... Loose connections and overheating of conductors Magnetic field strength and electric field strength of conductors Static electricity of sensitive equipment 12. What is meant by online power quality monitoring? On-line power quality data assessment analyzes data as they are captured. The analys ...
... Loose connections and overheating of conductors Magnetic field strength and electric field strength of conductors Static electricity of sensitive equipment 12. What is meant by online power quality monitoring? On-line power quality data assessment analyzes data as they are captured. The analys ...
Network Technology Plan - Working Group
... indicates the passage of fault current, indicating that a fault is located downstream of the CFI's location. Common Information Model (generic term). The CIM is an information model for power systems and related secondary systems and computer applications. It is maintained (in part) by the CIM Users ...
... indicates the passage of fault current, indicating that a fault is located downstream of the CFI's location. Common Information Model (generic term). The CIM is an information model for power systems and related secondary systems and computer applications. It is maintained (in part) by the CIM Users ...
Broadband Wireless Access WISP Cookbook June 2003
... BreezePHONE®, BreezeNET®, WALKair®, WALKnet®, are trade names or trademarks of Alvarion Ltd. Other brand and product names are trade names or trademarks of their respective owners. ...
... BreezePHONE®, BreezeNET®, WALKair®, WALKnet®, are trade names or trademarks of Alvarion Ltd. Other brand and product names are trade names or trademarks of their respective owners. ...
CH3-MPLS-Multiprotocol
... To honor the service level guarantees, the service providers not only have to provide large data pipes (which are also costlier), but also look for architectures which can provide & guarantee QoS guarantees and optimal performance with minimal increase in the cost of network resources. MPLS technolo ...
... To honor the service level guarantees, the service providers not only have to provide large data pipes (which are also costlier), but also look for architectures which can provide & guarantee QoS guarantees and optimal performance with minimal increase in the cost of network resources. MPLS technolo ...
The TCP-Based New AIMD Congestion Control Algorithm
... This network model is quite simple and its assumptions have been evaluated in the Internet for several years. In practice the parameter X goal is the network capacity (i.e. the number of packets that the link and the routers’ buffer can hold – or in-the-fly packets). When the aggregate flows’ rate e ...
... This network model is quite simple and its assumptions have been evaluated in the Internet for several years. In practice the parameter X goal is the network capacity (i.e. the number of packets that the link and the routers’ buffer can hold – or in-the-fly packets). When the aggregate flows’ rate e ...
Faults Detection in Power Systems Using Artificial Neural Network
... control applications in mind, and the theories of the brain and nervous system have used ideas from control system theory [5]. The neural network represents a network with a finite number of layers consisting of solitary elements that are similar to neurons with different types of connection between ...
... control applications in mind, and the theories of the brain and nervous system have used ideas from control system theory [5]. The neural network represents a network with a finite number of layers consisting of solitary elements that are similar to neurons with different types of connection between ...
ready to `software define` your Wide area network?
... The booths in that row weren’t glitzy—no sign of hourly iPad raffles or other crowdpleasing gimmicks. They were populated by vendors that Mulhall, an IT director at SnoIsle Libraries in Washington state, had never encountered before. One of them was a startup called Talari Networks, which back then ...
... The booths in that row weren’t glitzy—no sign of hourly iPad raffles or other crowdpleasing gimmicks. They were populated by vendors that Mulhall, an IT director at SnoIsle Libraries in Washington state, had never encountered before. One of them was a startup called Talari Networks, which back then ...
Optical Network Infrastructure for GRID
... computational resources cannot keep up with the demands generated by some applications. As an example, particle physics experiments [1, 2] produce more data that can be realistically processed and stored in one location (i.e. several Petabytes/year). In such situations where intensive computation an ...
... computational resources cannot keep up with the demands generated by some applications. As an example, particle physics experiments [1, 2] produce more data that can be realistically processed and stored in one location (i.e. several Petabytes/year). In such situations where intensive computation an ...
Evaluation of Signal Processing Resource Management Algorithms
... • Internet only offers a best effort service, which can meet the traditional non-real-time Internet traffics. • For real-time traffic, it needs a new scheme to make reservation for the traffic. • IntServ(Integrated Services) can provide resource allocation to meet the requirement of real-time applic ...
... • Internet only offers a best effort service, which can meet the traditional non-real-time Internet traffics. • For real-time traffic, it needs a new scheme to make reservation for the traffic. • IntServ(Integrated Services) can provide resource allocation to meet the requirement of real-time applic ...
Business Data Communications and Networking
... power they once had. The central data communication network organization should have a written charter that defines its purpose, operational philosophy, and long-range goals. ...
... power they once had. The central data communication network organization should have a written charter that defines its purpose, operational philosophy, and long-range goals. ...
Designing a Rate-based Transport Protocol for
... wireless networks [2]–[9]. Some of these solutions [2], [3] try to maintain the semantics of TCP congestion control by hiding transmission losses from the end hosts by modifying the underlying infrastructure. Techniques like Explicit Loss Notification (ELN) [10] and Explicit Congestion Notification ...
... wireless networks [2]–[9]. Some of these solutions [2], [3] try to maintain the semantics of TCP congestion control by hiding transmission losses from the end hosts by modifying the underlying infrastructure. Techniques like Explicit Loss Notification (ELN) [10] and Explicit Congestion Notification ...
INTERNET 2G - IST TEQUILA
... Dynamic provisioning for trunks TSR Composite Links: bundling of STM16 links Composite link is presented as a single PPP connection to IP and MPLS IP traffic is load balanced over member links based on a hash function Link failures are rerouted over surviving member links in under 45msecs ...
... Dynamic provisioning for trunks TSR Composite Links: bundling of STM16 links Composite link is presented as a single PPP connection to IP and MPLS IP traffic is load balanced over member links based on a hash function Link failures are rerouted over surviving member links in under 45msecs ...
cs591report
... identifies to which group of hosts the machine belongs. Here it gets a little tricky. Given any address, a router likely does not know the definitive group (or subnet) to which the host belongs; however, routing persists in that if the router does have some idea of the destination’s location (i.e. i ...
... identifies to which group of hosts the machine belongs. Here it gets a little tricky. Given any address, a router likely does not know the definitive group (or subnet) to which the host belongs; however, routing persists in that if the router does have some idea of the destination’s location (i.e. i ...
CDD-564/LEN
... Front panel LEDs for unit status, stored event and the status of each of the four receive channels Interoperable with the CDM-570/L-IP , CDM-IP 550, and CDM-IP 300L ...
... Front panel LEDs for unit status, stored event and the status of each of the four receive channels Interoperable with the CDM-570/L-IP , CDM-IP 550, and CDM-IP 300L ...
Liaison Statement to IETF PWE3 WG on MS-PW over T-MPLS
... During the meeting requirements have been identified and agreed to carry a Multi-Segment Pseudowire (MS-PW) across IP/MPLS and T-MPLS networks. Q12/15 would appreciate feedbacks from IETF PWE3 WG on the problem statement and whether this application can be taken into consideration in the on-going wo ...
... During the meeting requirements have been identified and agreed to carry a Multi-Segment Pseudowire (MS-PW) across IP/MPLS and T-MPLS networks. Q12/15 would appreciate feedbacks from IETF PWE3 WG on the problem statement and whether this application can be taken into consideration in the on-going wo ...
15-441: Networking Virtual Circuits, ATM, MPLS Peter Steenkiste Carnegie Mellon University
... – SVCs are more like a phone call » PVCs administratively configured (but not “manually”) » SVCs dynamically set up on a “per-call” basis ...
... – SVCs are more like a phone call » PVCs administratively configured (but not “manually”) » SVCs dynamically set up on a “per-call” basis ...