5. big data analysis on medical insurance dataset abstract
... Data analysis is important to businesses will be an understatement. In fact, no business can survive without analyzing available data. Merely analyzing data isn't sufficient from the point of view of making a decision. How does one interpret from the analyzed data is more important. Unleashing the v ...
... Data analysis is important to businesses will be an understatement. In fact, no business can survive without analyzing available data. Merely analyzing data isn't sufficient from the point of view of making a decision. How does one interpret from the analyzed data is more important. Unleashing the v ...
SQL Business Intelligence
... Developing end-to-end BI prototype for Plan International Extensive project experience with Reporting Services Books, courses, exams and played Developed numerous reporting apps that should have been BI solutions! ...
... Developing end-to-end BI prototype for Plan International Extensive project experience with Reporting Services Books, courses, exams and played Developed numerous reporting apps that should have been BI solutions! ...
How Business Intelligence Software Works and a Brief Review of
... huge problem for the BI • Limited SQL functionality in some casessubqueries, multipass SQL, new functions like RANK • Proprietary methods are sometimes slow and inefficient ...
... huge problem for the BI • Limited SQL functionality in some casessubqueries, multipass SQL, new functions like RANK • Proprietary methods are sometimes slow and inefficient ...
CSCI 491/595: Mining Big Data Spring 2016
... Recognize real-world sources of information for automated knowledge discovery. Investigate large data sets with the ability to identify and take informed corrective actions for non-standard/missing data. Understand the implications of different methods for cleaning data. Become proficient in the use ...
... Recognize real-world sources of information for automated knowledge discovery. Investigate large data sets with the ability to identify and take informed corrective actions for non-standard/missing data. Understand the implications of different methods for cleaning data. Become proficient in the use ...
Answers to End-of-Chapter Materials
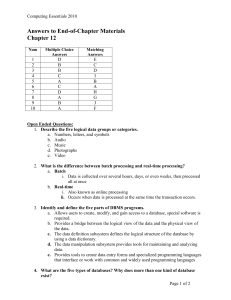
... 5. What are some of the benefits and limitations of databases? Why is security a concern? Sharing- information from one department can be readily shared with others. Security - Users are given passwords or access only to the kind of information they need. Less data redundancy - having access to one ...
... 5. What are some of the benefits and limitations of databases? Why is security a concern? Sharing- information from one department can be readily shared with others. Security - Users are given passwords or access only to the kind of information they need. Less data redundancy - having access to one ...
Minimum Security Procedure for Handling Physical University Data
... Classification Policy) and to protect the privacy of members of the University community. Scope This standard applies to all individuals who handle physical data containing sensitive or internal University data. Standard Granting Access or Sharing Access shall be limited to authorized University off ...
... Classification Policy) and to protect the privacy of members of the University community. Scope This standard applies to all individuals who handle physical data containing sensitive or internal University data. Standard Granting Access or Sharing Access shall be limited to authorized University off ...
Introduction to NACOR NACOR is a data warehouse that will
... Our participants range from pen-and-paper practices to the most wired academic centers. You do not need an AIMS systems or electronic health records (EHR) to participate. AQI will help facilitate contribution of data that is readily available in electronic form, beginning with your billing data and ...
... Our participants range from pen-and-paper practices to the most wired academic centers. You do not need an AIMS systems or electronic health records (EHR) to participate. AQI will help facilitate contribution of data that is readily available in electronic form, beginning with your billing data and ...
Ran_Wolff
... mining and to the emergence of important markets (e.g., homeland security, cross company production chain data .mining) for this type of applications This area of research is rapidly maturing. Unfortunately, recent studies all point to one major deficiency -- the lack of a well defined way of modeli ...
... mining and to the emergence of important markets (e.g., homeland security, cross company production chain data .mining) for this type of applications This area of research is rapidly maturing. Unfortunately, recent studies all point to one major deficiency -- the lack of a well defined way of modeli ...
Session 7 Solution
... Business intelligence (BI) refers to technologies, applications and practices for the collection, integration, analysis, and presentation of business information and sometimes to the information itself. The purpose of business intelligence--a term that dates at least back to 1958--is to support bett ...
... Business intelligence (BI) refers to technologies, applications and practices for the collection, integration, analysis, and presentation of business information and sometimes to the information itself. The purpose of business intelligence--a term that dates at least back to 1958--is to support bett ...
Document
... Exchanges may place a text file on their server that we can access on a nightly basis Exchanges may load a text file containing the contents of their database to our server. For each Exchange, we’ll build an automated process that acquires their updates nightly (or on an agreed-upon frequency) autom ...
... Exchanges may place a text file on their server that we can access on a nightly basis Exchanges may load a text file containing the contents of their database to our server. For each Exchange, we’ll build an automated process that acquires their updates nightly (or on an agreed-upon frequency) autom ...
Letter of Permission for Use of Data or Samples
... the content of this letter, please contact Rebecca Novak at [email protected] or Dr. Laura Mitchell at ...
... the content of this letter, please contact Rebecca Novak at [email protected] or Dr. Laura Mitchell at ...
CLASS API Prototype Summary
... The SNAAP API Query Language can be used by a remote client to request catalog and inventory-level metadata, subset the data and deliver data granules from each supported data source. The data source output structure is described by a Common Data Model, which is compatible with the Unidata NetCDF 4 ...
... The SNAAP API Query Language can be used by a remote client to request catalog and inventory-level metadata, subset the data and deliver data granules from each supported data source. The data source output structure is described by a Common Data Model, which is compatible with the Unidata NetCDF 4 ...
Algebra 2 Name: Date: What is the science of statistics? The science
... The science of statistics deals with the collection, analysis, interpretation, and presentation of data. 2. Describe descriptive statistics? Organizing and summarizing data is called descriptive data. 3. What are the two ways to summarize data? Two ways to summarize data are by graphing and numbers. ...
... The science of statistics deals with the collection, analysis, interpretation, and presentation of data. 2. Describe descriptive statistics? Organizing and summarizing data is called descriptive data. 3. What are the two ways to summarize data? Two ways to summarize data are by graphing and numbers. ...
Business Performance Management Master Deck
... Web-based administration, publishing, scheduling, and delivery — Single management environment reduces administration time — Logging mechanism provides continuous system performance tuning — Enables Intelligence and SQR to benefit from common functionality ...
... Web-based administration, publishing, scheduling, and delivery — Single management environment reduces administration time — Logging mechanism provides continuous system performance tuning — Enables Intelligence and SQR to benefit from common functionality ...
Data Analytics for Evidence-based Healthcare (DAEBH 2015)
... more. In order to successfully transform the healthcare system into a more efficient system, some interdependent challenges need to be overcome, such as prevalence of tightly coupled applications and data; inadequate data and knowledge standards; insufficient analytics capabilities; unsatisfactory s ...
... more. In order to successfully transform the healthcare system into a more efficient system, some interdependent challenges need to be overcome, such as prevalence of tightly coupled applications and data; inadequate data and knowledge standards; insufficient analytics capabilities; unsatisfactory s ...
The Sixth IEEE International Workshop on Data Integration and
... services due to the large-scale generation of social, sensor, mobile, networking, and other types of data stored in various data repositories, such as databases, data warehouses, and Web. However, how to integrate those data resources with different structures or ontologies to enable effective learn ...
... services due to the large-scale generation of social, sensor, mobile, networking, and other types of data stored in various data repositories, such as databases, data warehouses, and Web. However, how to integrate those data resources with different structures or ontologies to enable effective learn ...
The CUAHSI Observations Data Model
... – Standardization of investigator data management in environmental observatories ...
... – Standardization of investigator data management in environmental observatories ...
Responses to questions
... e.g. results of drug trials might inform future drug development in the pharmaceutical industry In such a highly regulated industry, the ability to get back to raw data to ensure authenticity is very important! ...
... e.g. results of drug trials might inform future drug development in the pharmaceutical industry In such a highly regulated industry, the ability to get back to raw data to ensure authenticity is very important! ...
Abstract
... important task is to identify groups of related genes that are combinatorially involved in such biological processes, mainly through gene set enrichment analysis (GSEA). In the past, many statistical methods have been developed for GSEA. However, there is very limited literature in its integrative a ...
... important task is to identify groups of related genes that are combinatorially involved in such biological processes, mainly through gene set enrichment analysis (GSEA). In the past, many statistical methods have been developed for GSEA. However, there is very limited literature in its integrative a ...
P1(10)_Farhi_Israel
... Handles up to 64 Input’s channels. Communicate with Smart Sensors via RS232C, RS485, USB and TCP/IP. Microsoft SQL Server local data base. Enhanced QA tools by range and digital monitor status checking. User definable alerts and immediate transmission to the Central by using ASCII or Binary messages ...
... Handles up to 64 Input’s channels. Communicate with Smart Sensors via RS232C, RS485, USB and TCP/IP. Microsoft SQL Server local data base. Enhanced QA tools by range and digital monitor status checking. User definable alerts and immediate transmission to the Central by using ASCII or Binary messages ...
Monitoring the Data Tsunami (Johannes Gehrke)
... By 2020, we will live in a world where small-scale sensors will be ubiquitous and pervasive, and where they will have the computational power to sense and monitor every corner of the world. Monitoring and understanding this flood of data is a grand research challenge. I will discuss two approaches f ...
... By 2020, we will live in a world where small-scale sensors will be ubiquitous and pervasive, and where they will have the computational power to sense and monitor every corner of the world. Monitoring and understanding this flood of data is a grand research challenge. I will discuss two approaches f ...
for machine learning on genomic data
... Genetic variation identification from high-throughput genomic data is becoming increasingly prevalent in the field of medical research with ever larger cohorts of samples. However, traditional computing hardware and software are inadequate to cater for large-cohort analysis, with the finite resource ...
... Genetic variation identification from high-throughput genomic data is becoming increasingly prevalent in the field of medical research with ever larger cohorts of samples. However, traditional computing hardware and software are inadequate to cater for large-cohort analysis, with the finite resource ...
GEOGRAPHIC INFORMATION SYSTEMS
... two types of database management systems? How do they differ? What are the three data models used and which one does ArcGIS prefer? How does the relational data model work? What is the difference between data and information? Information systems have four principle components: what are they? Which o ...
... two types of database management systems? How do they differ? What are the three data models used and which one does ArcGIS prefer? How does the relational data model work? What is the difference between data and information? Information systems have four principle components: what are they? Which o ...
CS 161: Chapter 7 Data Structures
... • An ADT is a data structure together with the operations that are allowed on the data structure. • STACK: FILO structure, top, Push, Pop • QUEUE: FIFO structure, head, tail (front, back), Enqueue, Dequeue • LIST: head, tail, current, Insert, Delete, Next ...
... • An ADT is a data structure together with the operations that are allowed on the data structure. • STACK: FILO structure, top, Push, Pop • QUEUE: FIFO structure, head, tail (front, back), Enqueue, Dequeue • LIST: head, tail, current, Insert, Delete, Next ...
Data analysis

Analysis of data is a process of inspecting, cleaning, transforming, and modeling data with the goal of discovering useful information, suggesting conclusions, and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, in different business, science, and social science domains.Data mining is a particular data analysis technique that focuses on modeling and knowledge discovery for predictive rather than purely descriptive purposes. Business intelligence covers data analysis that relies heavily on aggregation, focusing on business information. In statistical applications, some people divide data analysis into descriptive statistics, exploratory data analysis (EDA), and confirmatory data analysis (CDA). EDA focuses on discovering new features in the data and CDA on confirming or falsifying existing hypotheses. Predictive analytics focuses on application of statistical models for predictive forecasting or classification, while text analytics applies statistical, linguistic, and structural techniques to extract and classify information from textual sources, a species of unstructured data. All are varieties of data analysis.Data integration is a precursor to data analysis, and data analysis is closely linked to data visualization and data dissemination. The term data analysis is sometimes used as a synonym for data modeling.