has today sent top EU and UK Brexit negotiators* a briefing
... Your adversary has powerful and sophisticated tools to undermine your privacy. ...
... Your adversary has powerful and sophisticated tools to undermine your privacy. ...
Network Security For Distributed Simulation Systems
... Non-repudiation Guarantees of Authenticity and Integrity of data ...
... Non-repudiation Guarantees of Authenticity and Integrity of data ...
Download PDF
... But since many of these get into the grey area of whether faculty or university have the rights, and apparently grey areas can be firmed up by whoever asserts the rights first, which could lead to inconsistent individual instances within the same institution, my thinking is that we should be aiming ...
... But since many of these get into the grey area of whether faculty or university have the rights, and apparently grey areas can be firmed up by whoever asserts the rights first, which could lead to inconsistent individual instances within the same institution, my thinking is that we should be aiming ...
GUI Report Writing
... Let the user concentrate on the report design, we will take care of providing data. ...
... Let the user concentrate on the report design, we will take care of providing data. ...
Mucho Big Data y ¿La Seguridad para cuándo?
... Scalable and Intelligent Architecture Intelligence and ...
... Scalable and Intelligent Architecture Intelligence and ...
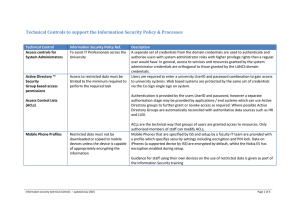
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
BCS Higher Education Qualifications Diploma in IT
... Diploma in IT Candidates must have achieved the Certificate in IT or have an appropriate exemption to be entered for the Diploma in IT. Candidates are required to become a member of BCS, The Chartered Institute for IT to sit and be awarded the qualifications. Candidates may apply for a four year stu ...
... Diploma in IT Candidates must have achieved the Certificate in IT or have an appropriate exemption to be entered for the Diploma in IT. Candidates are required to become a member of BCS, The Chartered Institute for IT to sit and be awarded the qualifications. Candidates may apply for a four year stu ...
Secure Deduplication with Efficient and Reliable
... has been widely used in cloud storage to reduce storage space and upload bandwidth. Promising as it is, an arising challenge is to perform secure Deduplication in cloud Storage. Although convergent encryption has been extensively adopted for secure Deduplication, a critical issue of making convergen ...
... has been widely used in cloud storage to reduce storage space and upload bandwidth. Promising as it is, an arising challenge is to perform secure Deduplication in cloud Storage. Although convergent encryption has been extensively adopted for secure Deduplication, a critical issue of making convergen ...
Six Symptoms of Life Science Companies Suffering from
... another. Worst of all, you lose sleep worrying you’ll miss sales targets because your BI tool works only when it’s connected to the Internet, and it could be unavailable at the exact moment your reps need it reveal best practices—for example, by crunching through years of in-house and outside data t ...
... another. Worst of all, you lose sleep worrying you’ll miss sales targets because your BI tool works only when it’s connected to the Internet, and it could be unavailable at the exact moment your reps need it reveal best practices—for example, by crunching through years of in-house and outside data t ...
Database
... Organisation-specific security classification level or possible restrictions on use. This may contain technicallin~ to security systems. .Related data elements List of closely related data element names when the relation is important. .Field name(s) Field names are the names used for this element in ...
... Organisation-specific security classification level or possible restrictions on use. This may contain technicallin~ to security systems. .Related data elements List of closely related data element names when the relation is important. .Field name(s) Field names are the names used for this element in ...
Judul
... built for a specific purpose • Data is stored hierarchically for easier storage and retrieval • Files: collections of related records • Records: collections of related fields ...
... built for a specific purpose • Data is stored hierarchically for easier storage and retrieval • Files: collections of related records • Records: collections of related fields ...
Judul
... built for a specific purpose • Data is stored hierarchically for easier storage and retrieval • Files: collections of related records • Records: collections of related fields ...
... built for a specific purpose • Data is stored hierarchically for easier storage and retrieval • Files: collections of related records • Records: collections of related fields ...
IDMS Essentials
... Data Dictionaries and the DDS CA-IDMS enables you to build one or more databases using a data dictionary. A data dictionary is itself a CA-IDMS database that contains all the data and system definitions for one or more databases. A data dictionary is divided logically into areas. The information is ...
... Data Dictionaries and the DDS CA-IDMS enables you to build one or more databases using a data dictionary. A data dictionary is itself a CA-IDMS database that contains all the data and system definitions for one or more databases. A data dictionary is divided logically into areas. The information is ...
Computer Security: Principles and Practice, 1/e
... The focus of this chapter is on three fundamental questions: ...
... The focus of this chapter is on three fundamental questions: ...
Chapter 11
... • A database constructed for quick searching, retrieval, ad-hoc queries, and ease of use. • An ERP system could exist without having a data warehouse. The trend, however, is that organizations that are serious about competitive advantage deploy both. The recommended data architecture for an ERP impl ...
... • A database constructed for quick searching, retrieval, ad-hoc queries, and ease of use. • An ERP system could exist without having a data warehouse. The trend, however, is that organizations that are serious about competitive advantage deploy both. The recommended data architecture for an ERP impl ...
Quality Control and Data Mining Techniques Applied to Monitoring
... techniques may help with detecting trends, while the data mining tools may help with identifying (useful) patterns in the data that accompany the scaled scores. In recent years at ETS, researchers considered monitoring the following variables: means and variances of the scaled and raw scores, means ...
... techniques may help with detecting trends, while the data mining tools may help with identifying (useful) patterns in the data that accompany the scaled scores. In recent years at ETS, researchers considered monitoring the following variables: means and variances of the scaled and raw scores, means ...
Decentralized Database
... An example is the Internet Domain Name System (DNS) - a generalpurpose distributed data query service chiefly used on the Internet for translating hostnames into Internet addresses. (Handout on this on the intranet) ...
... An example is the Internet Domain Name System (DNS) - a generalpurpose distributed data query service chiefly used on the Internet for translating hostnames into Internet addresses. (Handout on this on the intranet) ...
RM3G: Next Generation Recovery Manager
... An in-network aggregator combines data from sensors as they are routed through an overlay network ...
... An in-network aggregator combines data from sensors as they are routed through an overlay network ...
Estimation of the Lead-Lag Parameter from Synchronous Data
... dynamics. In practice, what we care about most is the lead-lag parameter, which can be measured at various temporal scales. In our paper, we propose a simple estimation procedure of that parameter. In order to verify the accuracy of the procedure, we construct three pairs of individual stocks, and e ...
... dynamics. In practice, what we care about most is the lead-lag parameter, which can be measured at various temporal scales. In our paper, we propose a simple estimation procedure of that parameter. In order to verify the accuracy of the procedure, we construct three pairs of individual stocks, and e ...
What the Specification Says Describe flat files and relational
... File – a is a collection of sets of similar data called records Table - another name for a file Tuple - another name for a record Item - an item of data within a recorded Field - the area where items are stored Attribute - another name for a field Database - a series of related files, called tables ...
... File – a is a collection of sets of similar data called records Table - another name for a file Tuple - another name for a record Item - an item of data within a recorded Field - the area where items are stored Attribute - another name for a field Database - a series of related files, called tables ...
The Basics of All-Payer Claims Databases
... reporting initiatives. The examples in this paper focus on APCDs that are legally mandated initiatives in which payers are compelled to report by law. At a high level, APCD systems collect data from existing claims transaction systems used by health care providers and payers. The information typical ...
... reporting initiatives. The examples in this paper focus on APCDs that are legally mandated initiatives in which payers are compelled to report by law. At a high level, APCD systems collect data from existing claims transaction systems used by health care providers and payers. The information typical ...
Senior IT Architect
... Contracted, or subcontracted to Computer Sciences Corporation, MITRE Corporation, McLane Advanced Technologies, Future Skies, Inc., and the State of Texas, winning high-profile enterprise data / network architecting and engineering engagements and collaborating among diverse stakeholders, subject-ma ...
... Contracted, or subcontracted to Computer Sciences Corporation, MITRE Corporation, McLane Advanced Technologies, Future Skies, Inc., and the State of Texas, winning high-profile enterprise data / network architecting and engineering engagements and collaborating among diverse stakeholders, subject-ma ...
Best Practice: Enable quality assessment of
... primacy. Work carried out in the European Commission's Open Data Support project suggests seven aspects to consider: Accuracy: is the data correctly representing the real-world entity or event? Consistency: Is the data not containing contradictions? Availability: Can the data be accessed now and ove ...
... primacy. Work carried out in the European Commission's Open Data Support project suggests seven aspects to consider: Accuracy: is the data correctly representing the real-world entity or event? Consistency: Is the data not containing contradictions? Availability: Can the data be accessed now and ove ...
Universiteit Gent
... setting up fixed links with a few selected neighbours, creating a wireless switched ethernet. This allows the introduction of known and well tested ethernet concepts in the WMN domain. • The Sensor and Actuator Network (SANET). Uses IEEE 802.15.4 technology for the MAC layer. ZigBee doesn't support ...
... setting up fixed links with a few selected neighbours, creating a wireless switched ethernet. This allows the introduction of known and well tested ethernet concepts in the WMN domain. • The Sensor and Actuator Network (SANET). Uses IEEE 802.15.4 technology for the MAC layer. ZigBee doesn't support ...
PLANNING INFORMATION SYSTEM FOR MAJLIS PERBANDARAN
... designed to help its planning department in executing development control activities. SIMAP integrates both spatial and nonspatial data using the latest GIS technology. SIMAP is running using ESRI ArcGIS ArcView for its GIS component and screen customized using MS Visual Basic for a user-friendly in ...
... designed to help its planning department in executing development control activities. SIMAP integrates both spatial and nonspatial data using the latest GIS technology. SIMAP is running using ESRI ArcGIS ArcView for its GIS component and screen customized using MS Visual Basic for a user-friendly in ...