Android - part IV
... – System removes app's files only in particular cases – Best place for files that don't require access restrictions • Files we want to share with other apps • Files the user can access with a computer ...
... – System removes app's files only in particular cases – Best place for files that don't require access restrictions • Files we want to share with other apps • Files the user can access with a computer ...
1 - Hospital for Special Surgery
... accessible only to the principal investigator (Dr.__________), in addition to other IRBapproved study personnel. Each subject will be assigned a unique study number for identification in the study database. This unique study number will not be derived from or related to information about the individ ...
... accessible only to the principal investigator (Dr.__________), in addition to other IRBapproved study personnel. Each subject will be assigned a unique study number for identification in the study database. This unique study number will not be derived from or related to information about the individ ...
CS 368 Introduction to Computer Science
... – “Bioinformatics is the field of science in which biology, computer science, and information technology merge to form a single discipline.” – “The ultimate goal of the field is to enable the discovery of new biological insights as well as to create a global perspective from which unifying principle ...
... – “Bioinformatics is the field of science in which biology, computer science, and information technology merge to form a single discipline.” – “The ultimate goal of the field is to enable the discovery of new biological insights as well as to create a global perspective from which unifying principle ...
Introduction to Objects
... with each branch of the library, just to name a few. You'd have to search at least three tables just to find a book, learn its location, and see whether it's checked in! It's easy to imagine how difficult it could get to find the right book. If you weren't careful, you might even mess something up b ...
... with each branch of the library, just to name a few. You'd have to search at least three tables just to find a book, learn its location, and see whether it's checked in! It's easy to imagine how difficult it could get to find the right book. If you weren't careful, you might even mess something up b ...
DOC - Columbus State University
... of requests each second. The precision of the IDS is paramount in this case. Even a tiny false positive rate of .001%, a level to which the authors make no claim, would could result in a deluge of alerts that could prove an impossible task to address. Proper attention to alerts also requires knowled ...
... of requests each second. The precision of the IDS is paramount in this case. Even a tiny false positive rate of .001%, a level to which the authors make no claim, would could result in a deluge of alerts that could prove an impossible task to address. Proper attention to alerts also requires knowled ...
data extraction from medical records
... The SEASCALE HEALTH CENTRE Practice & its Doctors & Staff, working as part of the NHS, need and want to share data in various ways but we also want to protect your confidential and personal information. Data about health can be used for various reasons, both internally within the practice, and exter ...
... The SEASCALE HEALTH CENTRE Practice & its Doctors & Staff, working as part of the NHS, need and want to share data in various ways but we also want to protect your confidential and personal information. Data about health can be used for various reasons, both internally within the practice, and exter ...
Distributed Data Mining Implementing Data Mining Jobs on Grid
... DM components correspond to a particular algorithm to be executed on a given dataset, provided a certain set of input parameters for the algorithm. We can therefore describe each DM components _ with the triple: A = (A, D, {P}) where A is the data mining algorithm, D is the input dataset, and {P} is ...
... DM components correspond to a particular algorithm to be executed on a given dataset, provided a certain set of input parameters for the algorithm. We can therefore describe each DM components _ with the triple: A = (A, D, {P}) where A is the data mining algorithm, D is the input dataset, and {P} is ...
Ch03 Data Warehouse
... Operational data stores (ODS) A type of database often used as an interim area for a data warehouse Oper marts - an operational data mart. Enterprise data warehouse (EDW) A data warehouse for the enterprise. Metadata: Data about data. In a data warehouse, metadata describe the contents of a data war ...
... Operational data stores (ODS) A type of database often used as an interim area for a data warehouse Oper marts - an operational data mart. Enterprise data warehouse (EDW) A data warehouse for the enterprise. Metadata: Data about data. In a data warehouse, metadata describe the contents of a data war ...
Storage Devices and Media Study Guide
... RAM stands for Random Access Memory, volatile memory or memory that loses its contents when the power is off. Volatile means it can be erased or closed out of easily. ROM stands for Read Only Memory. ROM is non-volatile and does not lose its contents when the power is off. Non-volatile means it can ...
... RAM stands for Random Access Memory, volatile memory or memory that loses its contents when the power is off. Volatile means it can be erased or closed out of easily. ROM stands for Read Only Memory. ROM is non-volatile and does not lose its contents when the power is off. Non-volatile means it can ...
To - Royal Albert Hall jobs
... This new role is pivotal to understanding what is important to the Royal Albert Hall’s customers and exploring their behaviour. The Insight Manager will use the Hall’s CRM system, Tessitura, and channels including the website, social media and surveys to analyse and improve the Hall’s CRM programme ...
... This new role is pivotal to understanding what is important to the Royal Albert Hall’s customers and exploring their behaviour. The Insight Manager will use the Hall’s CRM system, Tessitura, and channels including the website, social media and surveys to analyse and improve the Hall’s CRM programme ...
slides
... The term OLAP („online analytical processing“) was coined in a white paper written for Arbor Software Corp. in 1993 Interactive process of creating, managing, analyzing and reporting on data Analyzing large quantities of data in realtime ...
... The term OLAP („online analytical processing“) was coined in a white paper written for Arbor Software Corp. in 1993 Interactive process of creating, managing, analyzing and reporting on data Analyzing large quantities of data in realtime ...
Irwin/McGraw-Hill
... Hierarchical databases (also called tree databases) organize and search data using the structure of a family tree. Each record of the hierarchical structure may have multiple “child” records that are subordinate to it. See next Slide Choosing which records are superior and which records are subordin ...
... Hierarchical databases (also called tree databases) organize and search data using the structure of a family tree. Each record of the hierarchical structure may have multiple “child” records that are subordinate to it. See next Slide Choosing which records are superior and which records are subordin ...
Data Resource Management
... companies that look at their data as an asset and companies that are highly successful in their respective industries? ...
... companies that look at their data as an asset and companies that are highly successful in their respective industries? ...
Fundamentals of SQL Server Architecture
... There are different ways to organize data in a database but relational databases are one of the most effective. Relational database systems are an application of mathematical set theory to the problem of effectively organizing data. In a relational database, data is collected into tables (called rel ...
... There are different ways to organize data in a database but relational databases are one of the most effective. Relational database systems are an application of mathematical set theory to the problem of effectively organizing data. In a relational database, data is collected into tables (called rel ...
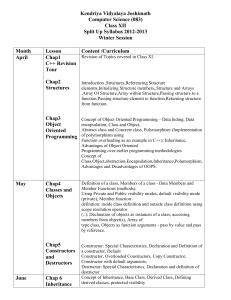
Split Up For Class XII
... Associative Law, Identity law, Inverse law, Principle of Duality, Idem potent Law, Distributive Law, Absorption Law, Involution law, DeMorgan’s Law and their applications; Obtaining Sum of Product (SOP) and Product of Sum (POS) form from the Truth Table, Reducing Boolean Expression (SOP and POS) to ...
... Associative Law, Identity law, Inverse law, Principle of Duality, Idem potent Law, Distributive Law, Absorption Law, Involution law, DeMorgan’s Law and their applications; Obtaining Sum of Product (SOP) and Product of Sum (POS) form from the Truth Table, Reducing Boolean Expression (SOP and POS) to ...
Data warehousing in telecom Industry
... of product and services of any organization. By this we can predict and place the particular item at profitable place .It with the help of data mining tools and techniques, Make us to understand the knowledge of customer and its requirements. Telecom industries have many departmental databases which ...
... of product and services of any organization. By this we can predict and place the particular item at profitable place .It with the help of data mining tools and techniques, Make us to understand the knowledge of customer and its requirements. Telecom industries have many departmental databases which ...
Problem Solving
... • Access is a relational database – A relational database is a collection of data items organized as a set of formally described tables from which data can be accessed easily – In addition to table definitions, there are also relationships between tables ...
... • Access is a relational database – A relational database is a collection of data items organized as a set of formally described tables from which data can be accessed easily – In addition to table definitions, there are also relationships between tables ...
Database Security
... • Protection from malicious attempts to steal (view) or modify data. • The mechanism that protect the database against intentional or accidental threats. ▫ Threat: Any situation or event, whether intentional or accidental, that may adversely affect a system & consequently the organization ...
... • Protection from malicious attempts to steal (view) or modify data. • The mechanism that protect the database against intentional or accidental threats. ▫ Threat: Any situation or event, whether intentional or accidental, that may adversely affect a system & consequently the organization ...
3C_Li
... for advertising and discovering services; the process model, which gives a detailed description of a service’s operation; and the grounding, which provides details on how to interoperate with a service With OWL-S markup of services, the knowledge necessary for service discovery could be specified as ...
... for advertising and discovering services; the process model, which gives a detailed description of a service’s operation; and the grounding, which provides details on how to interoperate with a service With OWL-S markup of services, the knowledge necessary for service discovery could be specified as ...
TCP_IP_Part3_BigPicture_Part2
... messages to determine DL of R in the past, and now have the DL address of R in their respective address tables. Similarly, R has the DL address of A and D in its address tables. ...
... messages to determine DL of R in the past, and now have the DL address of R in their respective address tables. Similarly, R has the DL address of A and D in its address tables. ...
Lecture 7 - IGLI TAFA
... maintain those files such that changes in programs require changes to the data ...
... maintain those files such that changes in programs require changes to the data ...
DATABASE SECURITY , INTEGRITY AND RECOVERY
... Availability is often thought of as a continuity of service assuring that database is available. Denial of service attacks are attempts to block authorized users ability to access and use the system when needed. It has number of aspects. ...
... Availability is often thought of as a continuity of service assuring that database is available. Denial of service attacks are attempts to block authorized users ability to access and use the system when needed. It has number of aspects. ...
Report for Data Mining
... Limited Information A database is often designed for purposes different from data mining and sometimes the properties or attributes that would simplify the learning task are ...
... Limited Information A database is often designed for purposes different from data mining and sometimes the properties or attributes that would simplify the learning task are ...
Tutorial 8 - Fredonia.edu
... Click the top left cell where the data will reside, click Data on the menu bar, point to Get External Data, and then New Database Query, then MS Access Database*. You will then be able to Browse and select the MthSales.mdb. You will be asked to select which fields of the database you want to include ...
... Click the top left cell where the data will reside, click Data on the menu bar, point to Get External Data, and then New Database Query, then MS Access Database*. You will then be able to Browse and select the MthSales.mdb. You will be asked to select which fields of the database you want to include ...