AD4301161166
... information from large amount of available data. This Discount retrieved information & knowledge is used for Step 6: Display results based on discount and based application ranging from market analysis, fraud on Standard Deviation detection, medical systems etc to production control After analyzing ...
... information from large amount of available data. This Discount retrieved information & knowledge is used for Step 6: Display results based on discount and based application ranging from market analysis, fraud on Standard Deviation detection, medical systems etc to production control After analyzing ...
REACH – Annex III
... ECHA’s Annex III Inventory ECHA have published a list of substances on their website under the heading ‘Annex III Inventory’. If a substance appears on this list, then in ECHA’s opinion it is presumed to meet the criterion b(ii), above; that is, it is predicted to be hazardous. The list does not tak ...
... ECHA’s Annex III Inventory ECHA have published a list of substances on their website under the heading ‘Annex III Inventory’. If a substance appears on this list, then in ECHA’s opinion it is presumed to meet the criterion b(ii), above; that is, it is predicted to be hazardous. The list does not tak ...
Multi-Domain Integration with MOF and extended Triple
... requirements document contains information on includes and extends relationships which is needed by the use case document. In the class diagram document we represent both relationships as aggregations. Thus, the class diagram document does not provide this information. We avoid the problems from Fig ...
... requirements document contains information on includes and extends relationships which is needed by the use case document. In the class diagram document we represent both relationships as aggregations. Thus, the class diagram document does not provide this information. We avoid the problems from Fig ...
data model
... “Operations for specifying database retrievals and updates by referring to the concepts of the data model.” Operations on the data model may include basic operations and user-defined operations. (e.g. A user-defined operation is COMPUTE_GPA which can be applied to a STUDENT object.) ...
... “Operations for specifying database retrievals and updates by referring to the concepts of the data model.” Operations on the data model may include basic operations and user-defined operations. (e.g. A user-defined operation is COMPUTE_GPA which can be applied to a STUDENT object.) ...
View PDF - CiteSeerX
... Many data mining systems search for interesting information in databases at low levels. That is, the language of the interesting information returned is composed of only the terms occurring in the data itself. In this paper, we will consider a high-level classi cation rule in which the language, of ...
... Many data mining systems search for interesting information in databases at low levels. That is, the language of the interesting information returned is composed of only the terms occurring in the data itself. In this paper, we will consider a high-level classi cation rule in which the language, of ...
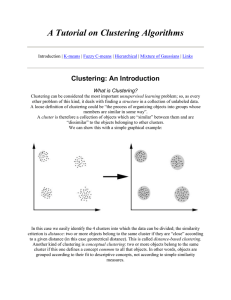
A Tutorial on Clustering Algorithms
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
... idea is to define k centroids, one for each cluster. These centroids shoud be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given d ...
Lecture 19 - The University of Texas at Dallas
... If the privacy policies are different from user preferences, the user is notified User can then decide how to proceed User/Client maintains the privacy controller - That is, Privacy controller determines whether an untrusted web site can give out public information to a third party so that the ...
... If the privacy policies are different from user preferences, the user is notified User can then decide how to proceed User/Client maintains the privacy controller - That is, Privacy controller determines whether an untrusted web site can give out public information to a third party so that the ...
PPT - Esri
... Portal for ArcGIS http://www.landscape.blm.gov/geoportal/catalog/main/portal.page ...
... Portal for ArcGIS http://www.landscape.blm.gov/geoportal/catalog/main/portal.page ...
Preserving Indonesia's heritage
... to preserve Borobudur for future generations, the historical site needed to be properly documented and a highly detailed digital rendering made. 3D laser scanners play an important part in mapping and documenting cultural heritage. When deterioration or unexpected natural disasters, such as floods, ...
... to preserve Borobudur for future generations, the historical site needed to be properly documented and a highly detailed digital rendering made. 3D laser scanners play an important part in mapping and documenting cultural heritage. When deterioration or unexpected natural disasters, such as floods, ...
NBBD Overview Presentation
... Once the account validation steps are complete, a repository record and a Direct account are provisioned for the registrant’s organization and an invoice is presented to complete activation (this is for demonstration purposes only – many sustainability models may be supported). ...
... Once the account validation steps are complete, a repository record and a Direct account are provisioned for the registrant’s organization and an invoice is presented to complete activation (this is for demonstration purposes only – many sustainability models may be supported). ...
Web Data Mining Techniques and Implementation for Handling Big
... Data can come from a variety of sources and in a variety of types that includes not only structured traditional relational data, but also semi-structured and unstructured data. Machine generated data such as click stream logs and email logs of unstructured data are larger in magnitude when compared ...
... Data can come from a variety of sources and in a variety of types that includes not only structured traditional relational data, but also semi-structured and unstructured data. Machine generated data such as click stream logs and email logs of unstructured data are larger in magnitude when compared ...
Interact: Gesture Recognition in the Cloud
... people with speaking or hearing disabilities that communicate explicitly through a set of gestures which form what we call a “sign language”. Communication outside of their communities for those people is often difficult, as most people are not familiar with sign languages. Also, the number of diffe ...
... people with speaking or hearing disabilities that communicate explicitly through a set of gestures which form what we call a “sign language”. Communication outside of their communities for those people is often difficult, as most people are not familiar with sign languages. Also, the number of diffe ...
DUA #: Leave blank if new request – if amendment request, then
... DUA #: Leave blank if new request – if amendment request, then please enter applicable DUA # Attachment B This attachment supplements the above-referenced Data Use Agreement (DUA) between the Centers for Medicare and Medicaid Services and the User (as set forth in the DUA). Upon execution by both pa ...
... DUA #: Leave blank if new request – if amendment request, then please enter applicable DUA # Attachment B This attachment supplements the above-referenced Data Use Agreement (DUA) between the Centers for Medicare and Medicaid Services and the User (as set forth in the DUA). Upon execution by both pa ...
History of SQL
... database are correct. The next revision was in 1992, and is known as SQL-92 or SQL 2. This was a major revision, and added more features to the language. The most important updates were more features related to DDL, data types, orthogonallity and set operations. These DDL features included alter and ...
... database are correct. The next revision was in 1992, and is known as SQL-92 or SQL 2. This was a major revision, and added more features to the language. The most important updates were more features related to DDL, data types, orthogonallity and set operations. These DDL features included alter and ...
Chapter 2
... the structure and constraints for the whole database for a community of users. Uses a conceptual or an implementation data model. • External schemas at the external level to describe the various user views. Usually uses the same data model as the conceptual level. Elmasri and Navathe, Fundamentals o ...
... the structure and constraints for the whole database for a community of users. Uses a conceptual or an implementation data model. • External schemas at the external level to describe the various user views. Usually uses the same data model as the conceptual level. Elmasri and Navathe, Fundamentals o ...
Database Systems For XML Data Storing
... § After storing the XML data in the relational database, following operations such as exclusion control, search, back up management will be easy. § There is a need to manage the XML characteristic information, i.e. character code, namespace, parent-child and forward-back relationship between tag ele ...
... § After storing the XML data in the relational database, following operations such as exclusion control, search, back up management will be easy. § There is a need to manage the XML characteristic information, i.e. character code, namespace, parent-child and forward-back relationship between tag ele ...
IEEE Paper Template in A4 (V1)
... on text refinement and knowledge distillation. Text refinement is an approach of transforming free-form text or document to intermediate form. Several techniques have been proposed for text mining including conceptual structure, association rule mining, episode rule mining, decision trees, and rule ...
... on text refinement and knowledge distillation. Text refinement is an approach of transforming free-form text or document to intermediate form. Several techniques have been proposed for text mining including conceptual structure, association rule mining, episode rule mining, decision trees, and rule ...
CIFS Service Description
... group and another for common documents. In creating directories for users in a department please note the following: 1. That everyone in the workgroup will have access to all the directories, the purpose here is not for maintain confidentiality but separating common documents. 2. The quota is counte ...
... group and another for common documents. In creating directories for users in a department please note the following: 1. That everyone in the workgroup will have access to all the directories, the purpose here is not for maintain confidentiality but separating common documents. 2. The quota is counte ...
Slide 1
... • Well-defined policies can help administrators to control and manage change proactively within the data services environment. ...
... • Well-defined policies can help administrators to control and manage change proactively within the data services environment. ...
Decision Support Systems
... learning and evolution by the user, the DSS builder, and the DSS itself ...
... learning and evolution by the user, the DSS builder, and the DSS itself ...
Distributed DBMS Architecture
... are identified together with the functionality that the system will provide for each class. The objectives of the system are clearly identified. But how do you achieve these objectives? BZUPAGES.COM ...
... are identified together with the functionality that the system will provide for each class. The objectives of the system are clearly identified. But how do you achieve these objectives? BZUPAGES.COM ...