Install Guide for SQL Server 2008 - DaaS (Data as a Service) offering
... need Local Administrator privileges. For a remote installation, you will need Operating System Administrator privileges. If you are on a workgroup network you will need Administrator rights on the domain. To configure databases and install data, you will need Database Administration privileges. A ne ...
... need Local Administrator privileges. For a remote installation, you will need Operating System Administrator privileges. If you are on a workgroup network you will need Administrator rights on the domain. To configure databases and install data, you will need Database Administration privileges. A ne ...
Intro - Millersville University
... Application program interface (e.g., ODBC/JDBC) which allow SQL queries to be sent to a database ...
... Application program interface (e.g., ODBC/JDBC) which allow SQL queries to be sent to a database ...
9781111969608_PPT_ch11
... SQL Parsing Phase (cont’d.) • Query optimizer analyzes SQL query and finds most efficient way to access data – Validated for syntax compliance – Validated against data dictionary • Tables and column names are correct • User has proper access rights ...
... SQL Parsing Phase (cont’d.) • Query optimizer analyzes SQL query and finds most efficient way to access data – Validated for syntax compliance – Validated against data dictionary • Tables and column names are correct • User has proper access rights ...
Group Project: Relational Database for a Distribution Firm
... MGMT 341 Project 1: Designing Relational Database Due date: November 28, 2005, Monday, at the beginning of class In this project, you will use Microsoft Access to build a typical relational database. Suppose that you own a small business and all data records now reside in an Excel spreadsheet (downl ...
... MGMT 341 Project 1: Designing Relational Database Due date: November 28, 2005, Monday, at the beginning of class In this project, you will use Microsoft Access to build a typical relational database. Suppose that you own a small business and all data records now reside in an Excel spreadsheet (downl ...
Chapter 8 - Databases
... that they map from names to values. The biggest difference is that the database is on disk (or other permanent storage), so it persists after the program ends. Because a database is stored on permanent storage, it can store far more data than variables, which are limited to the size of the memory in ...
... that they map from names to values. The biggest difference is that the database is on disk (or other permanent storage), so it persists after the program ends. Because a database is stored on permanent storage, it can store far more data than variables, which are limited to the size of the memory in ...
Designing 3NF for Ad Hoc Queries
... Setting the Default Database As a valid user, you will normally have access rights to your own user database and the objects it contains. You may also have permission to access objects in other databases. The user name you logon with is usually your default database. (This depends on how you were cr ...
... Setting the Default Database As a valid user, you will normally have access rights to your own user database and the objects it contains. You may also have permission to access objects in other databases. The user name you logon with is usually your default database. (This depends on how you were cr ...
Database
... A database management system or DBMS consists of a group of programs that manipulate the data within a database. It provides an interface between the database and the user, or the database and application programs. ...
... A database management system or DBMS consists of a group of programs that manipulate the data within a database. It provides an interface between the database and the user, or the database and application programs. ...
An Introduction to SQL
... Note that when a table is dropped, any data that you entered into the table is dropped ...
... Note that when a table is dropped, any data that you entered into the table is dropped ...
FREE Sample Here
... personal database that can be used to create a multiuser application. Figure 1-21 shows how this is accomplished. In general, personal databases should not be used for mission-critical applications. They impose a heavy network load when configured for multiple users, and do not generally provide the ...
... personal database that can be used to create a multiuser application. Figure 1-21 shows how this is accomplished. In general, personal databases should not be used for mission-critical applications. They impose a heavy network load when configured for multiple users, and do not generally provide the ...
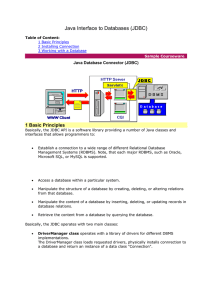
Java Interface to Databases (JDBC)
... 3. a so-called Database URL, which encoded using standard URL syntax (protocol + host + object). The protocol part starts always with "jdbc:" folowed by the name of the RDBMS (in our case "mysql") and terminated with "://" symbols. Thus, the protocol part in our example is "jdbc:mysql://". The host ...
... 3. a so-called Database URL, which encoded using standard URL syntax (protocol + host + object). The protocol part starts always with "jdbc:" folowed by the name of the RDBMS (in our case "mysql") and terminated with "://" symbols. Thus, the protocol part in our example is "jdbc:mysql://". The host ...
Chapter 1: Introduction
... between the low-level data stored in the database and the application programs and queries submitted to the system. The storage manager is responsible to the following tasks: ...
... between the low-level data stored in the database and the application programs and queries submitted to the system. The storage manager is responsible to the following tasks: ...
db2_migrate
... For example - /opt/ibm/db2/V9.7/java Go to Tools > Preferences > Database > Third Party JDBC Drivers and click on the Add Entry button. Provide the location of the db2jcc.jar file which you have copied to your client PC. Do the same for the other file db2jcc_license_cu.jar as well. ...
... For example - /opt/ibm/db2/V9.7/java Go to Tools > Preferences > Database > Third Party JDBC Drivers and click on the Add Entry button. Provide the location of the db2jcc.jar file which you have copied to your client PC. Do the same for the other file db2jcc_license_cu.jar as well. ...
Lecture 4.13.2011 - Databases Part 3
... What happens if you don't select all the fields for a query? An Exception will be generated. What makes the Query Builder useful? You don’t have to know SQL. But this is limiting… How were the records sorted in the Payable query? Last Name What SQL code was needed to do it? Ordered by… ...
... What happens if you don't select all the fields for a query? An Exception will be generated. What makes the Query Builder useful? You don’t have to know SQL. But this is limiting… How were the records sorted in the Payable query? Last Name What SQL code was needed to do it? Ordered by… ...
Powerpoint - SQL Saturday
... Setting up Elastic Database Jobs • It’s a customer-hosted Azure solution. • Cost is per component. • Requires the following components setup during install: • Cloud service (worker role to run tasks). • SQL Db (control db to store metadata, S0 default). • Service bus (used for work coordination). • ...
... Setting up Elastic Database Jobs • It’s a customer-hosted Azure solution. • Cost is per component. • Requires the following components setup during install: • Cloud service (worker role to run tasks). • SQL Db (control db to store metadata, S0 default). • Service bus (used for work coordination). • ...
Database_Users
... They are unsophisticated users who interact with the system by invoking one of the application program that have been written previously. ...
... They are unsophisticated users who interact with the system by invoking one of the application program that have been written previously. ...
Database
... • Database management system (DBMS) – Program, or collection of programs, through which users interact with a database ...
... • Database management system (DBMS) – Program, or collection of programs, through which users interact with a database ...
데이터베이스 관리자를 위한 Microsoft SQL Server
... Transactional parallelism — independent agent option used by default Download only articles — to reduce change trac king metadata Reduced contention on reporting subscribers Use snapshot isolation level ...
... Transactional parallelism — independent agent option used by default Download only articles — to reduce change trac king metadata Reduced contention on reporting subscribers Use snapshot isolation level ...
Chapter15 - Columbia College
... • Creating a new copy each time is essential – If it were to be created once and then stored on the user’s computer, then there would be two copies of the information ...
... • Creating a new copy each time is essential – If it were to be created once and then stored on the user’s computer, then there would be two copies of the information ...
Administration Of Users
... • Credentials – Credentials provide a way to allow SQL Server Authentication users to have an identity outside of SQL Server. – Credentials can also be used when a SQL Server Authentication user needs access to a domain resource, such as a file location to store a backup. – A credential can be mappe ...
... • Credentials – Credentials provide a way to allow SQL Server Authentication users to have an identity outside of SQL Server. – Credentials can also be used when a SQL Server Authentication user needs access to a domain resource, such as a file location to store a backup. – A credential can be mappe ...
DBXplorer : A System For Keyword-Based Search Over Relational
... Example for Keyword-Based Search is searching for “Jim Gary” on Microsoft intranet to obtain matched rows, i.e., rows in DB where ‘Jim ...
... Example for Keyword-Based Search is searching for “Jim Gary” on Microsoft intranet to obtain matched rows, i.e., rows in DB where ‘Jim ...
Chapter 1 Overview of Database Concepts
... repeating groups exist and it has a primary key • Second-normal form (2NF) is achieved if the record is in 1NF and has no partial dependencies • After a record is in 2NF and all transitive dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most d ...
... repeating groups exist and it has a primary key • Second-normal form (2NF) is achieved if the record is in 1NF and has no partial dependencies • After a record is in 2NF and all transitive dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most d ...
ppt
... Performance Implications • Do as few calls as possible over the net • Prefer asynchronous approaches – problem: success/failure indications – send lots of stuff, then synchronize ...
... Performance Implications • Do as few calls as possible over the net • Prefer asynchronous approaches – problem: success/failure indications – send lots of stuff, then synchronize ...
Conditions of Employment
... evaluation; written, oral, or performance tests, or other assessment methods. The Department of Employee Relations reserves the right to call only the most qualified candidates to oral and performance examinations. Oral examinations may include written exercises. Selection process component weights ...
... evaluation; written, oral, or performance tests, or other assessment methods. The Department of Employee Relations reserves the right to call only the most qualified candidates to oral and performance examinations. Oral examinations may include written exercises. Selection process component weights ...
Microsoft Access
Microsoft Access is a DBMS (also known as Database Management System) from Microsoft that combines the relational Microsoft Jet Database Engine with a graphical user interface and software-development tools. It is a member of the Microsoft Office suite of applications, included in the Professional and higher editions or sold separately.Microsoft Access stores data in its own format based on the Access Jet Database Engine. It can also import or link directly to data stored in other applications and databases.Software developers and data architects can use Microsoft Access to develop application software, and ""power users"" can use it to build software applications. Like other Office applications, Access is supported by Visual Basic for Applications (VBA), an object-oriented programming language that can reference a variety of objects including DAO (Data Access Objects), ActiveX Data Objects, and many other ActiveX components. Visual objects used in forms and reports expose their methods and properties in the VBA programming environment, and VBA code modules may declare and call Windows operating-system functions.