cos346day6
... • Solution: Like the 4NF solution for multivalued dependencies, use a separate table to store the multiple values DAVID M. KROENKE’S DATABASE PROCESSING, 10th Edition © 2006 Pearson Prentice Hall ...
... • Solution: Like the 4NF solution for multivalued dependencies, use a separate table to store the multiple values DAVID M. KROENKE’S DATABASE PROCESSING, 10th Edition © 2006 Pearson Prentice Hall ...
Chapter 21:Application Development and Administration
... Data Encryption Standard (DES) substitutes characters and rearranges their order on the basis of an encryption key which is provided to authorized users via a secure mechanism. Scheme is no more secure than the key transmission mechanism since the key has to be shared. ...
... Data Encryption Standard (DES) substitutes characters and rearranges their order on the basis of an encryption key which is provided to authorized users via a secure mechanism. Scheme is no more secure than the key transmission mechanism since the key has to be shared. ...
Data Sheet
... gains in application performance. With TimesTen Cache, a transaction that reads a database record can take less than 3 microseconds (a microsecond is one millionth of a second), and transactions that update or insert a record can take about 7 microseconds (measured with Oracle Linux running on Intel ...
... gains in application performance. With TimesTen Cache, a transaction that reads a database record can take less than 3 microseconds (a microsecond is one millionth of a second), and transactions that update or insert a record can take about 7 microseconds (measured with Oracle Linux running on Intel ...
The Revised NTP TDMS System
... The Toxicology Data Management System (TDMS) for the National Toxicology Program (NTP) is sponsored by National Institute of Environmental Health Sciences (NIEHS). This is a reporting system that is used to analyze the toxicity of chemical agents by performing long-term and short-term studies of the ...
... The Toxicology Data Management System (TDMS) for the National Toxicology Program (NTP) is sponsored by National Institute of Environmental Health Sciences (NIEHS). This is a reporting system that is used to analyze the toxicity of chemical agents by performing long-term and short-term studies of the ...
Business Transactions
... • Identify Business Transactions and how Management Support Systems use transaction data • Become familiar with Transaction Processing System components and main properties ...
... • Identify Business Transactions and how Management Support Systems use transaction data • Become familiar with Transaction Processing System components and main properties ...
SQL Server 2016, New Database Features
... SQL Server 2016 Developer Edition offers the full feature set of SQL Server 2016 Enterprise Edition, but Developer Edition is for development and test only, and not for production environments or use with production data. Scale out relational and non-relational data queries with the simplicity of T- ...
... SQL Server 2016 Developer Edition offers the full feature set of SQL Server 2016 Enterprise Edition, but Developer Edition is for development and test only, and not for production environments or use with production data. Scale out relational and non-relational data queries with the simplicity of T- ...
Slide 1
... handles the user interface (Access Forms, Oracle Forms, Reports) and a database server stores the data. The actual functionality (business logic) of the application resides on the client and/or in the databases •Web-based (multi-tier architecture): A client computer uses a browser to access informat ...
... handles the user interface (Access Forms, Oracle Forms, Reports) and a database server stores the data. The actual functionality (business logic) of the application resides on the client and/or in the databases •Web-based (multi-tier architecture): A client computer uses a browser to access informat ...
Using Oracle 8i
... Oracle is a relational database management system that uses SQL as its data manipulation language. Information on SQL is given separately to these notes. These notes are a fast-start to the way we will use Oracle in the labs and supplement the SQL*Plus User's Guide and Reference manual available on ...
... Oracle is a relational database management system that uses SQL as its data manipulation language. Information on SQL is given separately to these notes. These notes are a fast-start to the way we will use Oracle in the labs and supplement the SQL*Plus User's Guide and Reference manual available on ...
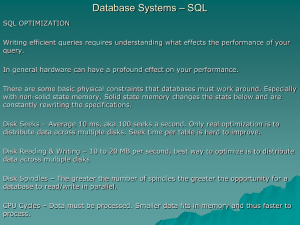
Optimizing SQL
... The more extensive your permissions are, the less optimized your database will be. Table level, column level permissions, resource counting, etc can be problematic if you have a large number of statements being executed. However, if you have a few very queries that execute over a large amount of dat ...
... The more extensive your permissions are, the less optimized your database will be. Table level, column level permissions, resource counting, etc can be problematic if you have a large number of statements being executed. However, if you have a few very queries that execute over a large amount of dat ...
Visual Basic Database Access
... • Command Object: The command object allows us to execute a SQL statement or a stored procedure. • DataReader: It is a read-only and forward-only pointer into a table to retrieve records. • DataSet Object: A DataSet object can hold several tables and relationships between tables. • DataAdapter: This ...
... • Command Object: The command object allows us to execute a SQL statement or a stored procedure. • DataReader: It is a read-only and forward-only pointer into a table to retrieve records. • DataSet Object: A DataSet object can hold several tables and relationships between tables. • DataAdapter: This ...
Severance-SI502-W09-Week14
... http://sqlitebrowser.sourceforge.net/ SQLite is embedded in Python and a number of other languages ...
... http://sqlitebrowser.sourceforge.net/ SQLite is embedded in Python and a number of other languages ...
Use the
... – Use the JDBC driver from the data-sources.xml file that is provided with Oracle Application Server 10g. – Use a properties file to store connection details. ...
... – Use the JDBC driver from the data-sources.xml file that is provided with Oracle Application Server 10g. – Use a properties file to store connection details. ...
Database Systems - University of Texas at Dallas
... • Complex problem of efficiently implementing a view for querying • Query modificationapproach – Modify view query into a query on underlying base tables – Disadvantage: inefficient for views defined via complex queries that are time-consuming to execute ...
... • Complex problem of efficiently implementing a view for querying • Query modificationapproach – Modify view query into a query on underlying base tables – Disadvantage: inefficient for views defined via complex queries that are time-consuming to execute ...
Two Phase Locking - Department of Computer Science
... • The part of the DBMS that keeps track of the locks issued to transactions is call the lock manager. The lock manager maintains a lock table which is a hash table with data object identifier as the key. The DBMS also maintains a descriptive entry for each transaction in a transaction table. The ent ...
... • The part of the DBMS that keeps track of the locks issued to transactions is call the lock manager. The lock manager maintains a lock table which is a hash table with data object identifier as the key. The DBMS also maintains a descriptive entry for each transaction in a transaction table. The ent ...
Distributed Databases - Computer Science, NMSU
... Salary > ‘20000’; call the result R1 • At site C, select all tuples from Emp2 satisfying Title = ‘manager’; call the result R2 • At some site to be determined by minimizing communication costs, perform the join of R1 and R2, project on the result using Name; send result to site A – In multidatabase ...
... Salary > ‘20000’; call the result R1 • At site C, select all tuples from Emp2 satisfying Title = ‘manager’; call the result R2 • At some site to be determined by minimizing communication costs, perform the join of R1 and R2, project on the result using Name; send result to site A – In multidatabase ...
An application of a relational database system for
... searched, and average values of processing time are shown. cEX-HR2 database was indexed and sorted by the formula weight column. dDatabase files of EX-HR2 were placed on the solid-state drive (SSD). eMaximum of 8 threads of HR2 were executed in parallel. ...
... searched, and average values of processing time are shown. cEX-HR2 database was indexed and sorted by the formula weight column. dDatabase files of EX-HR2 were placed on the solid-state drive (SSD). eMaximum of 8 threads of HR2 were executed in parallel. ...
Access Utilities - D. H. D`Urso and Associates
... Student “hands-on” - by the end of the class the student will have worked through all the Access Utilities and secured a database Exercises are cumulative – later examples build on objects created earlier ...
... Student “hands-on” - by the end of the class the student will have worked through all the Access Utilities and secured a database Exercises are cumulative – later examples build on objects created earlier ...
Complexity and Approximation of Fixing Numerical Attributes in
... Databases may become inconsistent wrt a given set of integrity constraints (ICs) DBMS has no mechanism to maintain certain classes of ICs Data of different sources are being integrated Even if the independent data sources are consistent, integrated data may not New constraints are imposed on pre-exis ...
... Databases may become inconsistent wrt a given set of integrity constraints (ICs) DBMS has no mechanism to maintain certain classes of ICs Data of different sources are being integrated Even if the independent data sources are consistent, integrated data may not New constraints are imposed on pre-exis ...
Oracle Architecture Basic
... Performs automatic process recovery Cleans up abnormally terminated connections Rolls back non committed transactions Releases resources held by abnormally terminated transactions Restarts failed shared server and dispatcher ...
... Performs automatic process recovery Cleans up abnormally terminated connections Rolls back non committed transactions Releases resources held by abnormally terminated transactions Restarts failed shared server and dispatcher ...
Database Application Security Models
... • Used in decision-support applications • Collection of many types of data taken from a number of different databases • Typically composed of a database server • Accessed by software applications or reporting applications: online analytical processing (OLAP) ...
... • Used in decision-support applications • Collection of many types of data taken from a number of different databases • Typically composed of a database server • Accessed by software applications or reporting applications: online analytical processing (OLAP) ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".