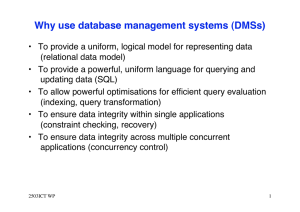
Introduction to Database Systems
... methodology, DBMS functions, database administration, and other database management approaches, such as client/server databases, object oriented databases, and data warehouses. At the completion of this course, students should be able to understand a user's database requirements and translate those ...
... methodology, DBMS functions, database administration, and other database management approaches, such as client/server databases, object oriented databases, and data warehouses. At the completion of this course, students should be able to understand a user's database requirements and translate those ...
DATA INDEPENDENCE AND DATABASE VIEWS
... Tuple might disappear from view! • WITH CHECK OPTION clause at end of view definition ensures new and updated tuples match view definition (else error) ...
... Tuple might disappear from view! • WITH CHECK OPTION clause at end of view definition ensures new and updated tuples match view definition (else error) ...
Development - Downloads
... The following is intended to outline Oracle’s general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. ...
... The following is intended to outline Oracle’s general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. ...
Best Practice Premier Keyboard Shortcuts
... By default, Best Practice uses the free version of SQL. The free version of SQL limits the amount of RAM that can be used by the instance, and is only suitable for practices that have up to about 10–15 concurrent users. If the practice has more concurrent users, Best Practice Software recommend that ...
... By default, Best Practice uses the free version of SQL. The free version of SQL limits the amount of RAM that can be used by the instance, and is only suitable for practices that have up to about 10–15 concurrent users. If the practice has more concurrent users, Best Practice Software recommend that ...
F1: A Distributed SQL Database That Scales
... schema often has several root tables, and in fact, a completely flat MySQL-style schema is still possible. Using hierarchy however, to the extent that it matches data semantics, is highly beneficial. In AdWords, most transactions are typically updating data for a single advertiser at a time, so we m ...
... schema often has several root tables, and in fact, a completely flat MySQL-style schema is still possible. Using hierarchy however, to the extent that it matches data semantics, is highly beneficial. In AdWords, most transactions are typically updating data for a single advertiser at a time, so we m ...
ppt - UMBC
... – Search for place within a radius of a latitude and longitude – Simple text searches, just like Google searches to return places • Restaurants in Baltimore ...
... – Search for place within a radius of a latitude and longitude – Simple text searches, just like Google searches to return places • Restaurants in Baltimore ...
DBAdminFund_PPT_5.2
... An incremental backup backs up only those files that have changed since the last backup. Only the changes are written to the backup media. If there has not been any changes, then no backup is made. Incremental backups should be made every day since the last full backup. ...
... An incremental backup backs up only those files that have changed since the last backup. Only the changes are written to the backup media. If there has not been any changes, then no backup is made. Incremental backups should be made every day since the last full backup. ...
DB2 Java Performance with pureQuery and Data Studio
... be manage properly by the programmer to maintain transaction service integrity. In addition to the setAutoCommit a database connection is usually generated with a pureQuery module. The connection information can be great to relieve the java application developer from this tedious task. The common er ...
... be manage properly by the programmer to maintain transaction service integrity. In addition to the setAutoCommit a database connection is usually generated with a pureQuery module. The connection information can be great to relieve the java application developer from this tedious task. The common er ...
ITU-R SG 1/WP 1B WORKSHOP: SPECTRUM MANAGEMENT ISSUES ON COGNITIVE RADIO SYSTEMS
... geolocation databases to determine a possibility for using cognitive radio devices in the border areas. The administrations establish a sharable geolocation database of protected radio devices for cross-border coordination of cognitive systems. SG 1/WP 1B Workshop: Spectrum Management issues on to ...
... geolocation databases to determine a possibility for using cognitive radio devices in the border areas. The administrations establish a sharable geolocation database of protected radio devices for cross-border coordination of cognitive systems. SG 1/WP 1B Workshop: Spectrum Management issues on to ...
person-name
... Drawback: getting information about, e.g., employee requires accessing two tables ...
... Drawback: getting information about, e.g., employee requires accessing two tables ...
Chapter 4
... identify each entity instance • Composite identifier: primary key composed of more than one attribute Database Systems, 8th Edition ...
... identify each entity instance • Composite identifier: primary key composed of more than one attribute Database Systems, 8th Edition ...
Parallel DBMS
... Selection may not require all sites for range or hash partitioning. Indexes can be built at each partition. Question: How do indexes differ in the different schemes? ...
... Selection may not require all sites for range or hash partitioning. Indexes can be built at each partition. Question: How do indexes differ in the different schemes? ...
All Things Database Encryption
... TDE only encrypts “data at rest” TDE protects data if following is stolen or lost - ...
... TDE only encrypts “data at rest” TDE protects data if following is stolen or lost - ...
Automatic Conflict Resolution to Integrate Relational Databases
... query results returned from each individual database. (e.g. Southstorm) data integration - transforming data representational conflicts at the global level. For example, “M” and “F” may represent “Male” and “Female” in one database, and another may represent these concepts using “0” and “1”. ...
... query results returned from each individual database. (e.g. Southstorm) data integration - transforming data representational conflicts at the global level. For example, “M” and “F” may represent “Male” and “Female” in one database, and another may represent these concepts using “0” and “1”. ...
Chapter 1
... Nature of Relational Databases • All data, even data about data such as a table and column names, are stored in tables. • Each row in a table should have a column (or columns) that uniquely identifies it, a primary key. • This primary key is repeated in other tables to create a relationship. • When ...
... Nature of Relational Databases • All data, even data about data such as a table and column names, are stored in tables. • Each row in a table should have a column (or columns) that uniquely identifies it, a primary key. • This primary key is repeated in other tables to create a relationship. • When ...
7. Decision Trees and Decision Rules
... By exchanging a single node category description for a more complex category pattern description, the distribution of information processing is distributed beyond a single ART module, which is more consistent with studies of neurobiological organization. ...
... By exchanging a single node category description for a more complex category pattern description, the distribution of information processing is distributed beyond a single ART module, which is more consistent with studies of neurobiological organization. ...
ppt - UMass Boston Computer Science
... Persistent objects have field-materialized identity It makes sense—Innate object identity depends on memory addresses, a short-lived phenomenon So long-lived objects (could be years…) have to be identified this way, it’s not the database’s fault ...
... Persistent objects have field-materialized identity It makes sense—Innate object identity depends on memory addresses, a short-lived phenomenon So long-lived objects (could be years…) have to be identified this way, it’s not the database’s fault ...
Database Mirroring: Maximizing Availability Through Automation
... VLDBs Myth: Cannot use compression in SQL Server 2005 Myth: Must initialize with a full backup ...
... VLDBs Myth: Cannot use compression in SQL Server 2005 Myth: Must initialize with a full backup ...
Decision Tree Construction - Department of Computer Science
... grouping-list. Why? Each answer record corresponds to a group, and there must be a single value per group. • The aggregate-list generates one value per group. • What about the group-qualification? ...
... grouping-list. Why? Each answer record corresponds to a group, and there must be a single value per group. • The aggregate-list generates one value per group. • What about the group-qualification? ...
Using Management Information Systems
... The data integrity problem can occur only if data are duplicated. Because of this, one easy way to eliminate the problem is to eliminate the duplicated data. This can be done by transforming the table into two tables. Because such joining of tables is common, DBMS products have been programm ...
... The data integrity problem can occur only if data are duplicated. Because of this, one easy way to eliminate the problem is to eliminate the duplicated data. This can be done by transforming the table into two tables. Because such joining of tables is common, DBMS products have been programm ...
All-Flash Arrays for Improving Database Performance to
... 2.1 Database Performance and Server and Storage System Resources Databases are used to extract the required information from large amounts of data at high speed. To achieve high-speed data access, database operations should be performed on the server as much as possible. The access frequency to the ...
... 2.1 Database Performance and Server and Storage System Resources Databases are used to extract the required information from large amounts of data at high speed. To achieve high-speed data access, database operations should be performed on the server as much as possible. The access frequency to the ...
Dynamic Query Forms for Database Queries
... Recently proposed automatic approaches to generate the database query forms without user participation presented a data-driven method. It first finds a set of data attributes, which are most likely queried based on the database schema and data instances. Then, the query forms are generated based on ...
... Recently proposed automatic approaches to generate the database query forms without user participation presented a data-driven method. It first finds a set of data attributes, which are most likely queried based on the database schema and data instances. Then, the query forms are generated based on ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".