Microsoft SQL Server Native High Availability with XtremIO
... and deduplicate multiple copies of the same database eliminates the disadvantage of AAG and changes the capacity utilization of the non-shared model used for availability groups. Figure 2 displays the before and after states to demonstrate how XtremIO changes the storage footprint for Availability G ...
... and deduplicate multiple copies of the same database eliminates the disadvantage of AAG and changes the capacity utilization of the non-shared model used for availability groups. Figure 2 displays the before and after states to demonstrate how XtremIO changes the storage footprint for Availability G ...
Introduction
... Database - a collection of related data that is persistent and too large to fit into main memory Database Management System – an automated system that maintains and provides multi-user access to a database, and whose operation is efficient, easy to use, and safe Information System – A system (i.e., ...
... Database - a collection of related data that is persistent and too large to fit into main memory Database Management System – an automated system that maintains and provides multi-user access to a database, and whose operation is efficient, easy to use, and safe Information System – A system (i.e., ...
Document
... Author’s ID number in the database. In the books database, this integer field is defined as an autoincremented field. For each new record inserted in this table, the database automatically increments the authorID value to ensure that each record has a unique authorID. This field represents the table ...
... Author’s ID number in the database. In the books database, this integer field is defined as an autoincremented field. For each new record inserted in this table, the database automatically increments the authorID value to ensure that each record has a unique authorID. This field represents the table ...
MAA / Data Guard 12c Setup Guide Creating a RAC Physical
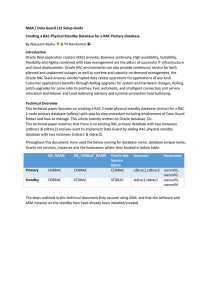
... Note: Recommended to use SPFILE, if PFILE is in use the update/append the above parameters as required. 2. Configure the RAC primary database initialization parameters to support standby role. SQL> alter system set FAL_SERVER='stdrac1,stdrac2' scope=both sid='*' DB_FILE_NAME_CONVERT/LOG_FILE_NAME_CO ...
... Note: Recommended to use SPFILE, if PFILE is in use the update/append the above parameters as required. 2. Configure the RAC primary database initialization parameters to support standby role. SQL> alter system set FAL_SERVER='stdrac1,stdrac2' scope=both sid='*' DB_FILE_NAME_CONVERT/LOG_FILE_NAME_CO ...
Slide 1
... Each database user has a log table in the SDE database or table space that tracks a user’s actions If all users use one login, all their actions will write to one table and this table will grow very large very fast Doing this also prohibits from restricting user access on a layer by layer basis ...
... Each database user has a log table in the SDE database or table space that tracks a user’s actions If all users use one login, all their actions will write to one table and this table will grow very large very fast Doing this also prohibits from restricting user access on a layer by layer basis ...
Chapter 5: Concurrency Control Techniques.
... 2. A transaction T must issue the operation write_lock(X) before any write_item(X) operation is performed in T. 3. A transaction T must issue the operation unlock(X) after all read_item(X) and write_item(X) operations are completed in T. 4. A transaction T must not issue a read_lock(X) operation if ...
... 2. A transaction T must issue the operation write_lock(X) before any write_item(X) operation is performed in T. 3. A transaction T must issue the operation unlock(X) after all read_item(X) and write_item(X) operations are completed in T. 4. A transaction T must not issue a read_lock(X) operation if ...
Application Development in Web Mapping 2. Spatial Data Storage
... A column describes a peculiar attribute of a certain record. A car can be described with a registration number, color, model name, year, etc. Each attribute value is stored in a column. Every column has a name and a data type. The terms column, field and attribute have similar meanings. Data type Th ...
... A column describes a peculiar attribute of a certain record. A car can be described with a registration number, color, model name, year, etc. Each attribute value is stored in a column. Every column has a name and a data type. The terms column, field and attribute have similar meanings. Data type Th ...
DA-10562 - Worldwide
... this, ISG Navigator allows data sources lacking one or more of these capabilities (such as file systems without query processing and cursor management) to benefit from this functionality. Similarly, ISG Navigator provides the necessary SQL extensions to support hierarchical queries and queries over ...
... this, ISG Navigator allows data sources lacking one or more of these capabilities (such as file systems without query processing and cursor management) to benefit from this functionality. Similarly, ISG Navigator provides the necessary SQL extensions to support hierarchical queries and queries over ...
Chapter 14 Methodology - Conceptual Database Design
... How would you identify attributes from a user’s requirements specification and then associate the attributes with entity or relationship types? In a similar way to identifying entities, we look for nouns or noun phrases in the users’ requirements specification. The attributes can be identified where ...
... How would you identify attributes from a user’s requirements specification and then associate the attributes with entity or relationship types? In a similar way to identifying entities, we look for nouns or noun phrases in the users’ requirements specification. The attributes can be identified where ...
Chapter 12
... Database Systems: Design, Implementation, & Management, 7th Edition, Rob & Coronel ...
... Database Systems: Design, Implementation, & Management, 7th Edition, Rob & Coronel ...
PowerPoint Chapter 12
... Database Systems: Design, Implementation, & Management, 7th Edition, Rob & Coronel ...
... Database Systems: Design, Implementation, & Management, 7th Edition, Rob & Coronel ...
Document
... • Transaction Log API (XLA) • Track real-time data changes • Monitor transaction updates • Propagate changes to external applications • Implement real-time event notification and processing ...
... • Transaction Log API (XLA) • Track real-time data changes • Monitor transaction updates • Propagate changes to external applications • Implement real-time event notification and processing ...
r – s
... E.g. multivalued attribute values are not atomic E.g. composite attribute values are not atomic The special value null is a member of every domain The null value causes complications in the definition of many ...
... E.g. multivalued attribute values are not atomic E.g. composite attribute values are not atomic The special value null is a member of every domain The null value causes complications in the definition of many ...
Indexing Spatial Data
... Spatial data is typically queried using a graphical query language; results are also displayed in a graphical manner. Graphical interface constitutes the front-end Extensions of SQL with abstract data types, such as lines, polygons and bit maps, have been proposed to interface with backend. allows r ...
... Spatial data is typically queried using a graphical query language; results are also displayed in a graphical manner. Graphical interface constitutes the front-end Extensions of SQL with abstract data types, such as lines, polygons and bit maps, have been proposed to interface with backend. allows r ...
View Report - PDF
... remediation effort, including detecting proprietary information in policy-violating situations and removing any unnecessary or outdated information. Phase 2 also includes making a number of infrastructure and policy changes and enhancements to protect remaining proprietary data. Major architectural ...
... remediation effort, including detecting proprietary information in policy-violating situations and removing any unnecessary or outdated information. Phase 2 also includes making a number of infrastructure and policy changes and enhancements to protect remaining proprietary data. Major architectural ...
An Introduction to DB2
... resources. Unlike DB2, the ADABAS nucleus needs only 1 region to run in and, because of ADABAS’ unique ability to compress data, it is stingy on DASD ...
... resources. Unlike DB2, the ADABAS nucleus needs only 1 region to run in and, because of ADABAS’ unique ability to compress data, it is stingy on DASD ...
Chapter 2
... • The relational model is currently the most popular model • Data is stored in tables • Columns are named • Each row contains values for each column, though some values may be missing • Rows are referred to as entities • The primary key is one or more columns in a table whose value(s) uniquely ident ...
... • The relational model is currently the most popular model • Data is stored in tables • Columns are named • Each row contains values for each column, though some values may be missing • Rows are referred to as entities • The primary key is one or more columns in a table whose value(s) uniquely ident ...
dbp10_ch04
... • Received one or more tables of existing data • Need to store data in new database • Problem: Store data as received, or transform? ...
... • Received one or more tables of existing data • Need to store data in new database • Problem: Store data as received, or transform? ...
Chp4: Relational Algebra
... Not supported as a primitive operator, but useful for expressing queries like: Find sailors who have reserved all boats. Let A have 2 fields, x and y; B have only field y: A/B = x | x , y A y B ...
... Not supported as a primitive operator, but useful for expressing queries like: Find sailors who have reserved all boats. Let A have 2 fields, x and y; B have only field y: A/B = x | x , y A y B ...
Database Tools by Skype
... Rule 1: Minimize number of connections. Channel all incoming queries through optimal number of database connections using pgBouncer Rule 2: Minimize number of indexes constraints that use up performance and resources. For example backoffice applications need quite often more and different indexes th ...
... Rule 1: Minimize number of connections. Channel all incoming queries through optimal number of database connections using pgBouncer Rule 2: Minimize number of indexes constraints that use up performance and resources. For example backoffice applications need quite often more and different indexes th ...
Encoding the Password - A low maintenance way to secure your data access
... The Application Login ID and password eliminate the maintenance of individual user login accounts on the database. The PROC PWENCODE procedure enables the password to be encoded and saved in a secure location. By combining the two steps we reduce the maintenance workload and steer clear the password ...
... The Application Login ID and password eliminate the maintenance of individual user login accounts on the database. The PROC PWENCODE procedure enables the password to be encoded and saved in a secure location. By combining the two steps we reduce the maintenance workload and steer clear the password ...
Click to
... exporting and importing the existing Springlake system documents’ and/or system audit records from the database. E.g. a Springlake server is setup and configured on a staging server. By using the export and import function, the configuration can be imported to the production server quickly. Copyrigh ...
... exporting and importing the existing Springlake system documents’ and/or system audit records from the database. E.g. a Springlake server is setup and configured on a staging server. By using the export and import function, the configuration can be imported to the production server quickly. Copyrigh ...
CSc-340 10a
... Cascading rollback – a single transaction failure leads to a series of transaction rollbacks. Consider the following schedule where none of the transactions has yet committed (so the schedule is recoverable) ...
... Cascading rollback – a single transaction failure leads to a series of transaction rollbacks. Consider the following schedule where none of the transactions has yet committed (so the schedule is recoverable) ...
Distributed Databases - University of Texas at El Paso
... Database Administration Database Administration Functions: Selection of Hardware and Software Difficult to keep abreast of current technology Difficult to predict future changes Emphasis on established off-the-shelf products ...
... Database Administration Database Administration Functions: Selection of Hardware and Software Difficult to keep abreast of current technology Difficult to predict future changes Emphasis on established off-the-shelf products ...
Microsoft Jet Database Engine
The Microsoft Jet Database Engine is a database engine on which several Microsoft products have been built. A database engine is the underlying component of a database, a collection of information stored on a computer in a systematic way. The first version of Jet was developed in 1992, consisting of three modules which could be used to manipulate a database.Database connect for MicrosoftJET stands for Joint Engine Technology, sometimes being referred to as Microsoft JET Engine or simply Jet. Microsoft Access and Visual Basic use or have used Jet as their underlying database engine. It has since been superseded for general use, however, first by Microsoft Desktop Engine (MSDE), then later by SQL Server Express. For larger database needs, Jet databases can be upgraded (or, in Microsoft parlance, ""up-sized"") to Microsoft's flagship database product, SQL Server.However, this does not mean that a MS Jet (Red) database cannot match MS SQL Server in storage capacity. A 5 billion record MS Jet (Red) database with compression and encryption turned on requires about 1 terabyte of disk storage space, comprising hundreds of (*.mdb) files, each acting as partial table, and not as a database in itself.Over the years, Jet has become almost synonymous with Microsoft Access, to the extent that many people refer to a Jet database as an ""Access database"".