Object Discovery: Soft Attributed Graph Mining
... We categorize this research in terms of its contribution to both graph theory and computer vision. From the theoretical perspective, this study can be considered as the first attempt to formulate the idea of mining maximal frequent subgraphs in the challenging domain of messy visual data, and as a c ...
... We categorize this research in terms of its contribution to both graph theory and computer vision. From the theoretical perspective, this study can be considered as the first attempt to formulate the idea of mining maximal frequent subgraphs in the challenging domain of messy visual data, and as a c ...
Introduction of Week 2
... System catalog is Active – automatically build and maintained Integrated – the system catalog is a part of DBMS and up-todate with any changes within the database Non-subvertible – DMBS operations are the only mechanism for populating the system catalog ...
... System catalog is Active – automatically build and maintained Integrated – the system catalog is a part of DBMS and up-todate with any changes within the database Non-subvertible – DMBS operations are the only mechanism for populating the system catalog ...
data
... updating it by withdrawing money (say $50 each) at the same time Security problems Hard to provide user access to some, but not all, data Database systems offer solutions to all the above problems ...
... updating it by withdrawing money (say $50 each) at the same time Security problems Hard to provide user access to some, but not all, data Database systems offer solutions to all the above problems ...
SYLLABUS B.Sc. INFORMATION
... Variables and Arrays, Declarations, Operators & Expressions, Library functions, Statements, Symbolic Constants, Preprocessor directives Data Input and Output- getchar(), putchar(), scanf(), printf(), gets(), puts() functions Control Statements- if-else, while, do-while, goto , for statements, nested ...
... Variables and Arrays, Declarations, Operators & Expressions, Library functions, Statements, Symbolic Constants, Preprocessor directives Data Input and Output- getchar(), putchar(), scanf(), printf(), gets(), puts() functions Control Statements- if-else, while, do-while, goto , for statements, nested ...
Database Systems: Design, Implementation, and Management
... • Simply use of batch processing concept – Update all data once a day • Considered as one phase locking ...
... • Simply use of batch processing concept – Update all data once a day • Considered as one phase locking ...
History of SQL
... integrity checks. This included defining primary keys, check constraints and referential integrity. A primary keys lets you uniquely identify an entity in a table, check constraints lets you limit the value range that can be placed in a column, and referential integrity ensures that relationships b ...
... integrity checks. This included defining primary keys, check constraints and referential integrity. A primary keys lets you uniquely identify an entity in a table, check constraints lets you limit the value range that can be placed in a column, and referential integrity ensures that relationships b ...
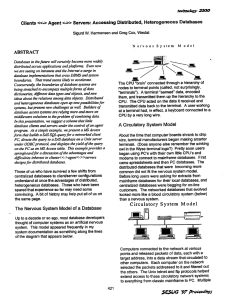
Clients <<-> Agent <->> Servers: Accessing Distributed, Heterogeneous Databases
... statement through to an IP address of a SAS server running SAS Share and SAS SHARE*NET. The ·passed-in" SAS • SQl code appears above. The _ server is listening at that address for SQl queries embedded in ODBC sCripts. It executes the query as a Unix process. The process transfers the yield of the qu ...
... statement through to an IP address of a SAS server running SAS Share and SAS SHARE*NET. The ·passed-in" SAS • SQl code appears above. The _ server is listening at that address for SQl queries embedded in ODBC sCripts. It executes the query as a Unix process. The process transfers the yield of the qu ...
Database Design Process IT420: Database Management and Organization
... Logical design: transform ER model into relational schema Schema refinement: Normalization Physical tuning ...
... Logical design: transform ER model into relational schema Schema refinement: Normalization Physical tuning ...
Database Design
... weeks 2 to 5 inclusive in the form of an on-line multiple choice quiz. Learning outcome 1 Examples of questions: ...
... weeks 2 to 5 inclusive in the form of an on-line multiple choice quiz. Learning outcome 1 Examples of questions: ...
Biometric FAQs
... Does BioStore record images of individual fingerprints? BioStore does not store images of fingerprints on its system, and never will. Only mathematical representations of certain points of a finger image are recorded, typically between ten and sixty depending on the characteristics of the finger. Th ...
... Does BioStore record images of individual fingerprints? BioStore does not store images of fingerprints on its system, and never will. Only mathematical representations of certain points of a finger image are recorded, typically between ten and sixty depending on the characteristics of the finger. Th ...
Bradley
... •The data reader object allows you to obtain the results of a SELECT statement from a command object. ...
... •The data reader object allows you to obtain the results of a SELECT statement from a command object. ...
Data Management Needs and Challenges for Telemetry Scientists
... To address complex questions related to marine mammal telemetry and understanding animal ecology, I had to become more of a data manager …And, in the process, I’ve become less of a biologist ...
... To address complex questions related to marine mammal telemetry and understanding animal ecology, I had to become more of a data manager …And, in the process, I’ve become less of a biologist ...
Fall 2008, INFS614 - GMU Computer Science
... DBMS ensures that execution of {T1,…, Tn} is equivalent to some serial execution T1’…Tn’. – Before reading/writing an object, a transaction requests a lock on the object, and waits till the DBMS gives it the lock. All locks are released at the end of the transaction. (Strict 2PL locking ...
... DBMS ensures that execution of {T1,…, Tn} is equivalent to some serial execution T1’…Tn’. – Before reading/writing an object, a transaction requests a lock on the object, and waits till the DBMS gives it the lock. All locks are released at the end of the transaction. (Strict 2PL locking ...
Introduction to Database Systems
... changes in logical structure of data. Physical data independence: Protection from changes in physical structure of data. ...
... changes in logical structure of data. Physical data independence: Protection from changes in physical structure of data. ...
Public Network aka Cluster Interconnect Oracle
... Users of 12.1.0.1 will have to upgrade to 12.1.0.2 or higher by 2016 No current Oracle version fits well the entire LHC Run 2. ...
... Users of 12.1.0.1 will have to upgrade to 12.1.0.2 or higher by 2016 No current Oracle version fits well the entire LHC Run 2. ...
Chapter 5 review
... (1,0):(0,1): Foreign key goes on whichever side will cause fewer nulls (1,1):(1,1): This relationship almost never exists in the real world. You probably made a mistake. Verify your cardinalities, or merge the two tables. Exception: this relationship is sometimes used for database performance ...
... (1,0):(0,1): Foreign key goes on whichever side will cause fewer nulls (1,1):(1,1): This relationship almost never exists in the real world. You probably made a mistake. Verify your cardinalities, or merge the two tables. Exception: this relationship is sometimes used for database performance ...
Creating & Modifying Database tables
... – Limits value that can be placed in specific column – Irrespective of values that exist in other table rows ...
... – Limits value that can be placed in specific column – Irrespective of values that exist in other table rows ...
No Slide Title
... • Each row-column entry in the table must have a single atomic value. • Data values in columns are of the same kind. In relational terms, this property states that all values in a given column must come from the same domain, a set of values that the column can have. • Each row is unique. No two rows ...
... • Each row-column entry in the table must have a single atomic value. • Data values in columns are of the same kind. In relational terms, this property states that all values in a given column must come from the same domain, a set of values that the column can have. • Each row is unique. No two rows ...
Project Midterm Presentation
... - used to get the default html for the module, what should be seen then first loading the specific page. - Returns an array of arrays, each with the form [divID] = html ...
... - used to get the default html for the module, what should be seen then first loading the specific page. - Returns an array of arrays, each with the form [divID] = html ...
The Evolving Role of SQL in Genetics, Breeding, and Selection Work
... Trac,ing the ancestors of selected breeders is one of the i n _ g queries psrtonned by the project. This process enables detection of inbreeding and gene frequency count of the current stock. If breeders had evolved after four cycles, these have desl'8nded from 16 purebred ancestors in the first gen ...
... Trac,ing the ancestors of selected breeders is one of the i n _ g queries psrtonned by the project. This process enables detection of inbreeding and gene frequency count of the current stock. If breeders had evolved after four cycles, these have desl'8nded from 16 purebred ancestors in the first gen ...
Database model

A database model is a type of data model that determines the logical structure of a database and fundamentally determines in which manner data can be stored, organized, and manipulated. The most popular example of a database model is the relational model, which uses a table-based format.