Visual Basic Database Access
... • Command Object: The command object allows us to execute a SQL statement or a stored procedure. • DataReader: It is a read-only and forward-only pointer into a table to retrieve records. • DataSet Object: A DataSet object can hold several tables and relationships between tables. • DataAdapter: This ...
... • Command Object: The command object allows us to execute a SQL statement or a stored procedure. • DataReader: It is a read-only and forward-only pointer into a table to retrieve records. • DataSet Object: A DataSet object can hold several tables and relationships between tables. • DataAdapter: This ...
PowerPoint ****
... Database proxy intercepts application’s query and rewrites it by anonymizing table and column names & encrypting constants with the key of the encryption scheme best suited for the operation and the user Database proxy checks if the DBMS needs to adjust encryption level before executing the query - ...
... Database proxy intercepts application’s query and rewrites it by anonymizing table and column names & encrypting constants with the key of the encryption scheme best suited for the operation and the user Database proxy checks if the DBMS needs to adjust encryption level before executing the query - ...
Freedom to Research
... standard, it can be very difficult to distinguish between what is and is not protected. For example, what is the level of creativity needed to protect a database in the U.S.? What is the level of skill needed in Canada? Or the levels of industriousness or economic investment required in Australia ...
... standard, it can be very difficult to distinguish between what is and is not protected. For example, what is the level of creativity needed to protect a database in the U.S.? What is the level of skill needed in Canada? Or the levels of industriousness or economic investment required in Australia ...
About the Presentations
... dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most databases • A primary key is used to uniquely identify each record Oracle 11g: SQL ...
... dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most databases • A primary key is used to uniquely identify each record Oracle 11g: SQL ...
About the Presentations
... dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most databases • A primary key is used to uniquely identify each record Oracle 11g: SQL ...
... dependencies have been removed, then it is in third-normal form (3NF), which is generally sufficient for most databases • A primary key is used to uniquely identify each record Oracle 11g: SQL ...
Hadoop vs. Parallel Databases
... • We are amazed at the hype that the MapReduce proponents have spread about how it represents a paradigm shift in the development of scalable, data-intensive applications! • 1. A giant step backward in the programming paradigm for large-scale data intensive applications! • 2. A sub-optimal implem ...
... • We are amazed at the hype that the MapReduce proponents have spread about how it represents a paradigm shift in the development of scalable, data-intensive applications! • 1. A giant step backward in the programming paradigm for large-scale data intensive applications! • 2. A sub-optimal implem ...
LN28 - WSU EECS
... RDF provides a foundation for representing and processing metadata RDF has a graph-based data model RDF has an XML-based syntax to support syntactic interoperability RDF has a decentralized philosophy and allows incremental building of knowledge, and its sharing and reuse ...
... RDF provides a foundation for representing and processing metadata RDF has a graph-based data model RDF has an XML-based syntax to support syntactic interoperability RDF has a decentralized philosophy and allows incremental building of knowledge, and its sharing and reuse ...
Lab 6
... the place where a value will be inserted during runtime, in this case, the search criteria provided by the user when executing the application. The following command is used to associate a value with the parameter marker. ...
... the place where a value will be inserted during runtime, in this case, the search criteria provided by the user when executing the application. The following command is used to associate a value with the parameter marker. ...
COGENT Database - NSW Department of Primary Industries
... standard web browser is able to view it. Initially a basic set of functionality has been provided, but this may be expanded in time. Specialist Access: Users with skills in using thirdparty products to access data (eg, ArcView or Crystal Reports) have access to non-confidential data tables in order ...
... standard web browser is able to view it. Initially a basic set of functionality has been provided, but this may be expanded in time. Specialist Access: Users with skills in using thirdparty products to access data (eg, ArcView or Crystal Reports) have access to non-confidential data tables in order ...
What is a Database
... entity set customer and another entity set account and the relationship between them – Other types of schema: relational schema, object schema, OR schema » Relational and OR schemas: SQL DDL Physical schema: database design at the physical level Example: the set of customers is an indexed-sequen ...
... entity set customer and another entity set account and the relationship between them – Other types of schema: relational schema, object schema, OR schema » Relational and OR schemas: SQL DDL Physical schema: database design at the physical level Example: the set of customers is an indexed-sequen ...
Session 5
... Index is a general term for an Oracle/SQL feature, used primarily to speed execution and (sometimes) impose uniqueness upon certain data. Indexes provide a faster access method to one table’s data than doing a ‘full table scan’. So instead of a query having to search all of the data within a table, ...
... Index is a general term for an Oracle/SQL feature, used primarily to speed execution and (sometimes) impose uniqueness upon certain data. Indexes provide a faster access method to one table’s data than doing a ‘full table scan’. So instead of a query having to search all of the data within a table, ...
View-based Query Processing for Semistructured Data.
... View-based query processing is the problem of processing queries over a database based on a set of materialized views, rather than on the raw data in the database. It is a fundamental problem in several settings, such as data warehousing, mobile computing, query optimization, and data integration, a ...
... View-based query processing is the problem of processing queries over a database based on a set of materialized views, rather than on the raw data in the database. It is a fundamental problem in several settings, such as data warehousing, mobile computing, query optimization, and data integration, a ...
IMS1907 Database Systems
... Internal Schema Physical schema – set of specifications describing how data from a logical schema are stored in a computer’s secondary memory for a specific DBMS – ideally one physical schema for each logical schema – describes organisation of physical records, file organisations, access paths to d ...
... Internal Schema Physical schema – set of specifications describing how data from a logical schema are stored in a computer’s secondary memory for a specific DBMS – ideally one physical schema for each logical schema – describes organisation of physical records, file organisations, access paths to d ...
Generic Instance Search from 1 Example Contribution II. Loc
... on-the-fly all boxes by summing inside-box point scores and dividing the pre-computed norms. Point scores are computed once. ...
... on-the-fly all boxes by summing inside-box point scores and dividing the pre-computed norms. Point scores are computed once. ...
Product Brochure
... shipping labels, using a pre-designed, tested template while entering portions of the data at print time is ideal. TechnoRiverStudio allows this by providing powerful combination of static templates with Print Time data entry dialog. Both text and barcodes in the document can be configured to suppor ...
... shipping labels, using a pre-designed, tested template while entering portions of the data at print time is ideal. TechnoRiverStudio allows this by providing powerful combination of static templates with Print Time data entry dialog. Both text and barcodes in the document can be configured to suppor ...
CH 13 Database Resource Management
... previously stored in separate files into a common pool of data records that provides data for many applications. The data stored in a database is independent of the application programs using it and of the type of secondary storage devices on which it is stored. The Database Management Approach: The ...
... previously stored in separate files into a common pool of data records that provides data for many applications. The data stored in a database is independent of the application programs using it and of the type of secondary storage devices on which it is stored. The Database Management Approach: The ...
MAYUR Relational Database Management System Model Answer
... To protect database we must take security measures at various levels as follows: 1) Physical Consideration:-The physical location where the actual computer system is located should be secured. 2) Human consideration:-Users of database system should be authorized carefully. 3) Operating System:-The o ...
... To protect database we must take security measures at various levels as follows: 1) Physical Consideration:-The physical location where the actual computer system is located should be secured. 2) Human consideration:-Users of database system should be authorized carefully. 3) Operating System:-The o ...
Object-Oriented Databases
... – Key Identification: What attributes are used to identify rows in a table? – Normalization: Table decomposition to solve update problems, normal forms ...
... – Key Identification: What attributes are used to identify rows in a table? – Normalization: Table decomposition to solve update problems, normal forms ...
Fact-Finding Techniques Fact-Finding
... including database planning, system definition, and requirements collection and analysis stages. Enables developer to learn about the terminology, problems, opportunities, constraints, requirements, and priorities of the organisation and the users of the system. ...
... including database planning, system definition, and requirements collection and analysis stages. Enables developer to learn about the terminology, problems, opportunities, constraints, requirements, and priorities of the organisation and the users of the system. ...
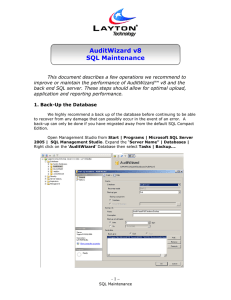
AuditWizard v8 SQL Maintenance
... that auditing began in your environment or since the last purge. Audit History tracks all changes that have been made since the last audit. For users that are auditing every 15-30 days, you may want to perform this purge at least quarterly (both histories). For users that audit on 0-14 days, we reco ...
... that auditing began in your environment or since the last purge. Audit History tracks all changes that have been made since the last audit. For users that are auditing every 15-30 days, you may want to perform this purge at least quarterly (both histories). For users that audit on 0-14 days, we reco ...
Unit 5 - NIST NACOL
... order that is useful to people who receive it. Database A database is a collection of related information about a subject organized in a useful manner that provides a base or foundation for procedure, such as retrieving information, drawing conclusion and make decision. A Database is a collection of ...
... order that is useful to people who receive it. Database A database is a collection of related information about a subject organized in a useful manner that provides a base or foundation for procedure, such as retrieving information, drawing conclusion and make decision. A Database is a collection of ...
Handout: Databases, and Databases in R
... If information is split across tables, we need to join it back together. The operation which does so is called a “join”, naturally enough, which in SQL shows up as a JOIN clause in SELECT, modifying the FROM. (In R, we join dataframes with the merge command; it has all the functionality of JOIN, tho ...
... If information is split across tables, we need to join it back together. The operation which does so is called a “join”, naturally enough, which in SQL shows up as a JOIN clause in SELECT, modifying the FROM. (In R, we join dataframes with the merge command; it has all the functionality of JOIN, tho ...
Database model

A database model is a type of data model that determines the logical structure of a database and fundamentally determines in which manner data can be stored, organized, and manipulated. The most popular example of a database model is the relational model, which uses a table-based format.